How To Rotate Your Source IP Address

IP-Go-Round – Source IP Rotation
I was on an engagement recently that was blocking my password sprays based on my IP address. If I made 3 incorrect requests from my IP, I was blocked out from making any other requests for 30 minutes. How annoying is that? It is a great form of security and it might stop attackers looking for a quick way in. But, this form of security shouldn’t be viewed as a way to stop all password spraying. It won’t stop a dedicated hacker, one really trying to get access to your environment.
One of the ways to bypass IP filtering is to use rotating source IPs. ProxyCannon is an amazing tool for automatically routing your traffic through multiple cloud servers to diversify the source IP addresses of your traffic. (Thank you #_shellIntel) . Check out this BHIS blog post that walks you through using ProxyCannon in conjunction with Burp Suite: https://www.blackhillsinfosec.com/using-burp-proxycannon/. However, I wanted to find something a little bit easier to use, so I did some research and found a service called ProxyMesh. It was pretty easy to set up and worked well for rotating source IP addresses during a password spray.
As part of the plan I signed up for, there are two proxy options. One is a proxy that has 10 IPs that are based in the US. The other option is one that is called “open” with 8,743 IPs. I tested speed and reliability with the open proxy and compared that to the US option.
ProxyMesh has multiple levels of payment options. There is a 30-day free trial after your trial is up you can pay as low as $10 a month for the service. Obviously the more you pay, the better service you get. The information found for this blog was gathered using the $10 a month plan. If you buy a better plan, your numbers might be different.
I used two ways to connect to ProxyMesh. The first way was the FoxyProxy add-on in Chrome. The second way was Burp Suite Pro. Both methods work great, so depending on what you are trying to do, you can set it up either way. I will show both methods.
Open FoxyProxy and set up a new proxy. Here are the settings that I have for the open proxy. Note that credentials are required in the authentication section.
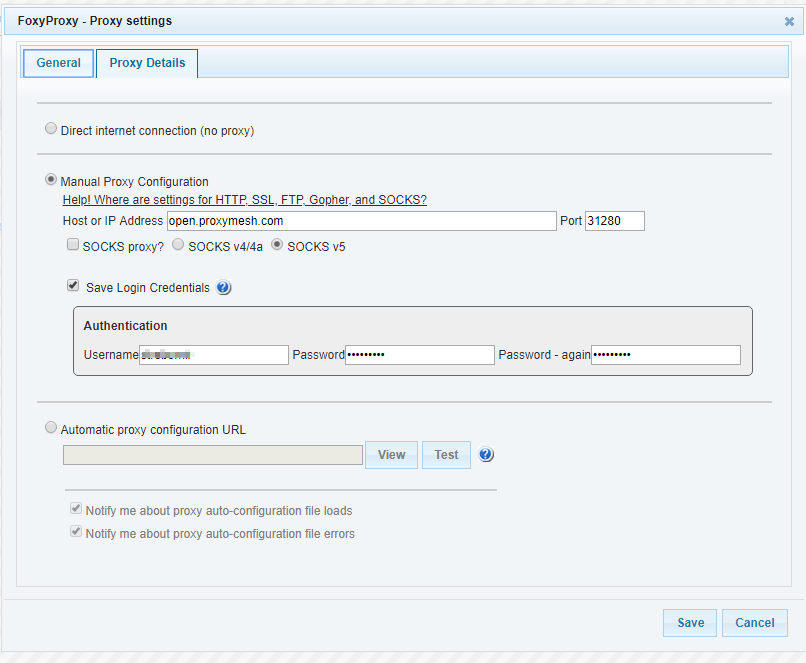
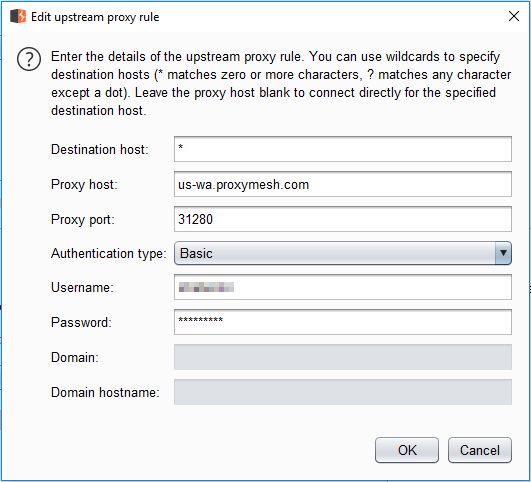
Using the other proxy in ProxyMesh is as simple as changing the Hostname from open.proxymesh.com to us-wa.proxymesh.com. Now, every time I load a web page, it looks like the request will be coming from a different IP. Here are a couple of samples.
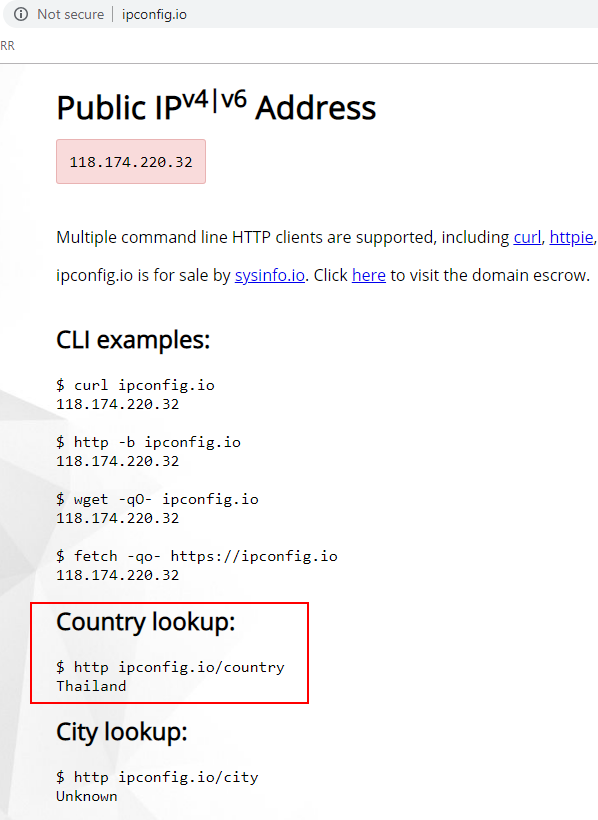
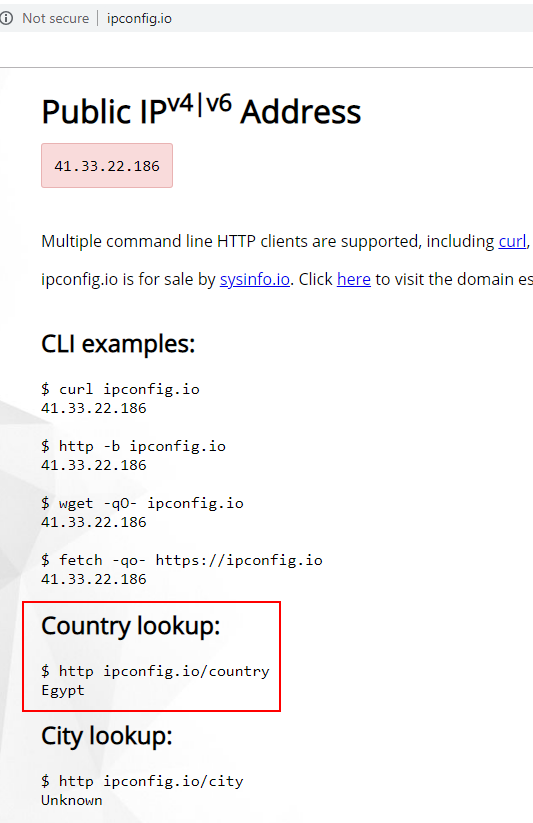
That is pretty cool! However, it is very time consuming to run tests hitting the reload button and copying the numbers down. By using Burp Suite Pro to run my requests, I can more easily track the IPs. In order to use Burp, I need to configure the proxy settings.
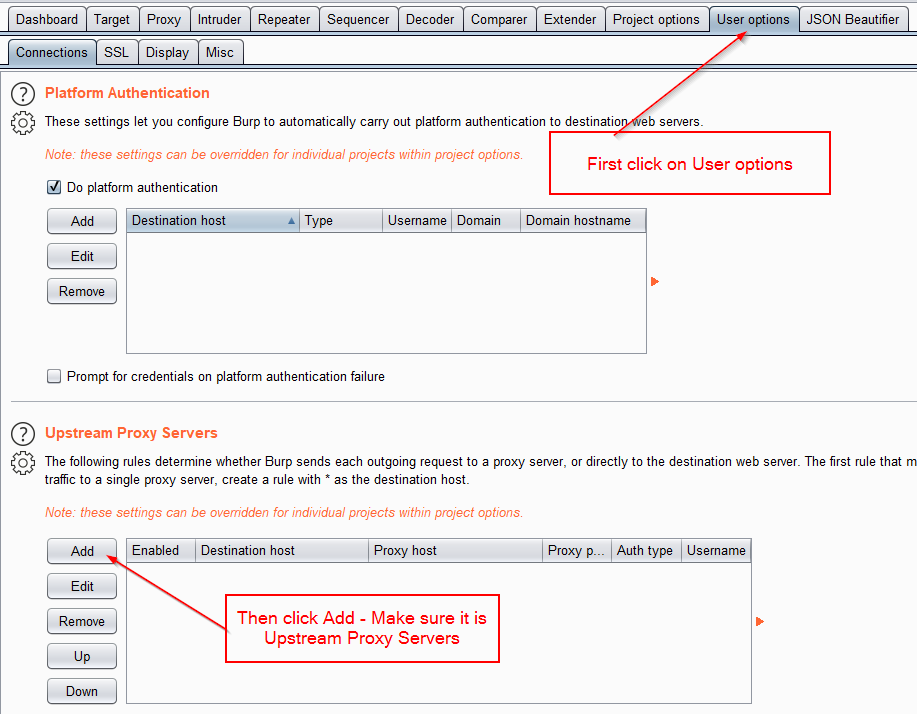
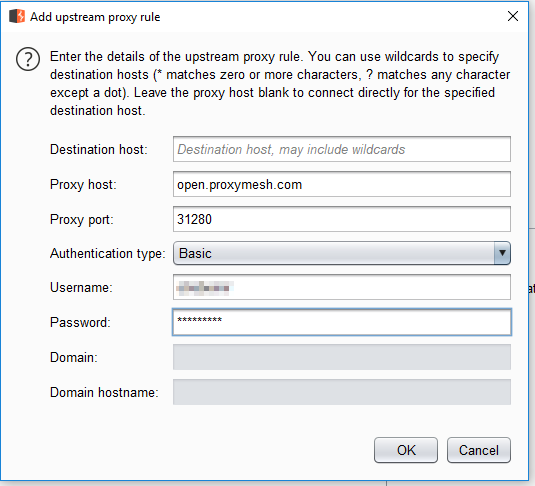
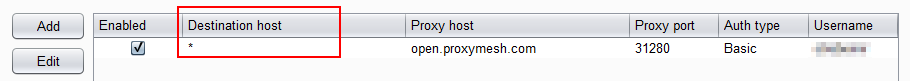
I intentionally left the destination host blank. After it has been added, you will see that it put in the wildcard, so that all destinations are using the proxy.
For the first trial using the open proxy, I ran trials with a sample size of 100 requests to get my IP address from a simple web request. I used the default settings on burp, 5 threads, not throttled. Out of 100 requests, I found that 7 failed with either a “Bad Request” response or a timeout. There were also 2 requests that returned a previously used IP. These 100 requests took just under 1.5 minutes to complete. I ran this same trial a total of 10 times and compiled the following results.
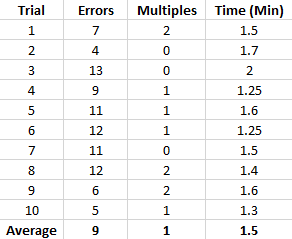
The IPs that were used more than once (Multiples) are minimal and don’t worry me too much. The errors were a little disturbing, but it wasn’t too much work to sort the results and make those few requests again. If it is a problem for you, then you might want to think of other options.
For informational purposes, the sample revealed the following countries for the source of the IPs and the number of times it was seen in a sample of 100 requests. Note, the total does not equal 100 because of errors received.
| Country Source for IP | Number of Times Seen |
| United States | 25 |
| Russia | 10 |
| Thailand | 4 |
| Indonesia | 4 |
| Unknown | 4 |
| Brazil | 4 |
| Canada | 3 |
| Iran | 3 |
| Ukraine | 3 |
| South Africa | 2 |
| Kenya | 2 |
| Germany | 2 |
| France | 2 |
| Ecuador | 2 |
| Colombia | 2 |
| Egypt | 2 |
| Turkey | 1 |
| Taiwan | 1 |
| Serbia | 1 |
| Republic of Korea | 1 |
| Poland | 1 |
| Palestine | 1 |
| Nigeria | 1 |
| Netherlands | 1 |
| Malaysia | 1 |
| Macedonia | 1 |
| Japan | 1 |
| Ireland | 1 |
| Greece | 1 |
| Ghana | 1 |
| Cambodia | 1 |
| Bosnia and Herzegovina | 1 |
| Argentina | 1 |
I changed the settings on the number of threads to 10 to see if that had any impact on the results. It appeared that the errors and multiples were similar, and the time to complete the requests dropped from 1.5 minutes to around 45 seconds to complete. Using more threads didn’t appear to affect the stability of the proxy. I changed the number of threads to 1 and again, the only change was the speed with which the requests processed.
I then changed my proxy to the other option, the US-WA Proxy.
These results were quite different. The 100 requests were much faster, completing in about 13 seconds with the default 5 threads and no throttling. Because the proxy rotates through 10 IPs, all of the IPs were used multiple times. The IPs used were duplicated from 6 to 14 times for the 100 requests. Also, there were no errors returned, and each request returned an IP.
Ultimately, I found that this was an easy and inexpensive way to rotate source IPs. Remember that engagement I was on that was blocking my password sprays? By using ProxyMesh to rotate my IPs I was able to conduct my password spray. While blocking multiple login attempts from one IP is a great security feature, it should not be relied on to completely mitigate the risk of password spraying.
Have you found another rotating proxy that works well? Let us know and we’ll check it out.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
