Pushing Your Way In

Over the past several years, attackers have gained significant traction in targeted environments by using various forms of password guessing. This situation was reflected in the 2020 Verizon DBIR under top threat action varieties.
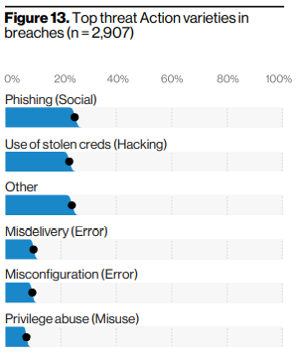
Use of stolen credentials sits right behind phishing as the second most utilized threat action in disclosed breaches. Malware variants don’t appear until number seven item in that list.
As a result of the above, organizations rapidly adopted Multi-Factor authentication on their critical internet-facing services like Virtual Private Networks (VPNs), Virtual Desktop Infrastructure (VDI), web-based email portals, and many others. The COVID 19 crisis served to exacerbate this situation as entire organizations transitioned to remote work.

Like other forms of security, two-factor authentication is not a silver bullet. Attackers have come up with ingenious ways to bypass two-factor authentication using reverse proxy software like CredSniper, Modlishka, and Evilginx2.
On some services, even when two-factor authentication is enforced, the order of operations that the service uses to perform the secondary factor may allow an attacker to validate user credentials. When this happens, the attacker can still perform attacks like password spraying to identify weak passwords. Then the attacker can use the validated credentials to attempt to authenticate to other services exposed by the organization and verify that two-factor implementation is uniform across the organization. Services that serially check credentials can also be used to identify accounts where two-factor is not enabled.

Over time, we have observed one technique that seems to be highly effective when we can find services with two-factor enabled that allow us to validate credentials before checking that secondary authentication factor. First, we typically perform password spraying as described above. If you are not familiar with password spraying, here are some good references that describe the technique:
- https://www.blackhillsinfosec.com/password-spraying-outlook-web-access-how-to-gain-access-to-domain-credentials-without-being-on-a-targets-network-part-2/
- https://www.blackhillsinfosec.com/introducing-mailsniper-a-tool-for-searching-every-users-email-for-sensitive-data/
Next, with valid credentials at hand, we send push notifications to users whose accounts are configured to support them and see who blindly accepts. Often, we will perform this activity at specific times of the day, like 8-9 am, 12-1 pm, or 6-7 pm in the target user’s time zone. These times are chosen because they are likely to be around the same time that the user authenticates for the first time in the morning, returns from lunch, or authenticates after leaving the office. Even with a small number of valid credentials, this technique appears to be very effective.

Because of the above, it is critical that users are properly trained to spot anomalous behavior associated with two-factor authentication. All of the following are indicators of compromise that users should be educated on and reporting to the information security department.
- Unsolicited phone call verifications
- Unsolicited push notifications
- Sign-in notifications from new locations/devices
On many of our engagements, the activities listed above never get reported. When these activities occur, it means that in no uncertain terms, the user’s password has been compromised. If users do not understand that correlation, they will never report the activity.
With so many organizations moving significant portions of their IT infrastructure into the cloud, a compromise like this can have devastating consequences. One such scenario was just discussed in our Attack Tactics 8 webcast.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
