Risky Business
Mike Perez //
At BHIS, a few of our customers have come to us very recently with the “risk du jour”; no, not the Cash for Creds program Beau highlighted but the risk posed when they discover that a business partner or far flung subsidiary has been hit by some ransomware variant. Side note: Be sure to take a listen to our recent ransomware webcast!
To that end, we came up with some quick and dirty recommendations. Note that these recommendations also apply when you’ve got a partner that has suffered a breach or major infection.
- Delineate all business processes/possible interactions (business to business links or automated workflows, etc.) that touch your partner. Isolate those processes and treat any data coming from that partner as potentially hostile or malicious. Set up a dedicated phone or in-person meeting to review with your partner how they are specifically handling those business interaction points post-incident.
- Treat all documents received from your partner within the timeframe of the Incident as hostile and investigate those systems that process those workflows for any signs of malware.
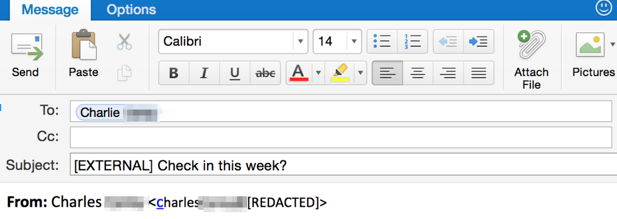
- Enable an SMTP gateway rule specifically flagging email from their domain so it is obvious to the recipients (I.e., your employees) and that automatically quarantines or if appropriate, deletes the attachments. Some email systems will allow you to pre-pend “[EXTERNAL]” or other such flag in the subject line so that employees can readily see internal vs. external email. Consider a rule which prepends your partner’s name so folks are extra vigilant. An example is below.
- Use a segmented and dedicated jump server to initiate any host to host communications with that partner.
- Request to be put in contact with any law enforcement personnel that your partner has contacted.
- Report this incident to your local law enforcement contacts. Leverage FBI and InfraGard contacts to provide you with current information on ransomware incidents in both your geographical area and in your particular industry.
- Ask your partner if they have any anecdotal stories of partners also being infected.
- Start refreshing and also testing your disaster recovery and business continuity plans.
- Test your backups. (You ARE backing up…. Right?)
- Stay paranoid, because now that folks have paid and it’s gotten press coverage, the wolves smell blood.
Yours in paranoia,
Mike
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Pay-Forward-What-You-Can Training
Available live/virtual and on-demand

