Android Dev & Penetration Testing Setup – Part 1
Joff Thyer // Editor’s Note: This is part 1 of a 3 part series. Part 1 will discuss configuring your virtual machine engine and virtual hardware emulation. Part 2 covers installing […]

Joff Thyer // Editor’s Note: This is part 1 of a 3 part series. Part 1 will discuss configuring your virtual machine engine and virtual hardware emulation. Part 2 covers installing […]

Luke Baggett // Imagine a scenario where a Penetration Tester is trying to set up command and control on an internal network blocking all outbound traffic, except traffic towards a […]
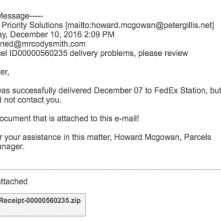
Cody Smith* // As information security professionals we’re not invincible to breaches. Even the most robust security system can’t make up for a lack of user education, which I was […]
John Strand with BHIS testers // Yes, we did this in 2017, but it’s reflecting work done in 2016.

Carrie Roberts // * Would you like to run Mimikatz without Anti-Virus (AV) detecting it? Recently I attempted running the PowerShell script “Invoke-Mimikatz” from PowerSploit on my machine but it was […]

David Fletcher // Recently we were involved in an engagement where we expected to see a large number of Macs in the target environment. As an element of the engagement […]
Carrie Roberts // My current favorite exploit is creating malicious outlook rules as described here. The rule is configured to download an executable file with an EXE extension (.exe) when an […]

Sierra Ward* // Normally I am hidden in the back rooms at BHIS, chipping away at 10 million marketing tasks. I show up occasionally in webcasts, lurking again in the shadows, […]
Check out Carrie’s demo of her DPAT, and if you missed her blog, check that out here.