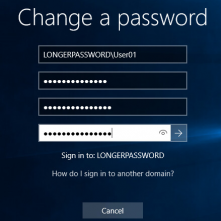
How to Increase the Minimum Character Password Length (15+) Policies in Active Directory
Kent Ickler // As a start to a series on Windows Administration in the eyes of a security-conscious “Windows Guy” I invite you on configuring AD DS PSOs (Password Security […]