Domain Password Audit Tool
Carrie Roberts // A tool to generate password usage statics in a Windows domain based on hashes dumped from a domain controller. The Domain Password Audit Tool (DPAT) is a […]
Carrie Roberts // A tool to generate password usage statics in a Windows domain based on hashes dumped from a domain controller. The Domain Password Audit Tool (DPAT) is a […]
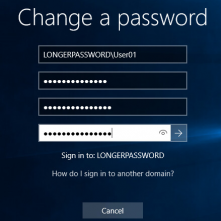
Kent Ickler // As a start to a series on Windows Administration in the eyes of a security-conscious “Windows Guy” I invite you on configuring AD DS PSOs (Password Security […]
Carrie Roberts // Answer: Enough to make it worth it! Penetration testers love to perform password spraying attacks against publicly available email portals as described here in this great post by Beau Bullock. […]

Rick Wisser & Gail Menius // Frequently we get asked about where to store passwords. Should they be stored in a word/excel /txt file on your computer? Maybe, written down […]
Beau Bullock // This is part two of a series of posts (See part 1 here) where I am detailing multiple ways to gain access to domain user credentials without ever being […]

Beau Bullock // In this series of posts I am going to detail multiple ways to gain access to domain user credentials without ever being on a target organization’s network. […]

Sally Vandeven // As pentesters we LOVE passwords – they come in all shapes and sizes. A good password has 16+ characters and a mix of case, digits and special […]

Joff Thyer // Many of us in the penetration testing community are used to scenarios whereby we land a targeted phishing campaign within a Windows enterprise environment and have […]

OSINT stands for open-source intelligence, and it refers to all publicly available information on the open internet which has been obtained without any special requirements (paywalls, invitations, etc.).