July 1, 2022
Hello everyone!
July is here and Fourth of July festivities are about to launch. And what would a holiday weekend be without a new set of challenges so you can enjoy a different kind of fireworks?
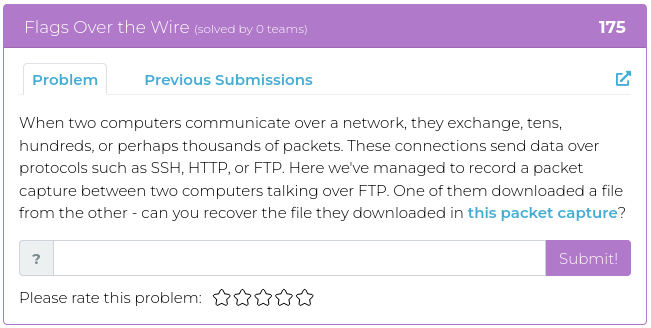
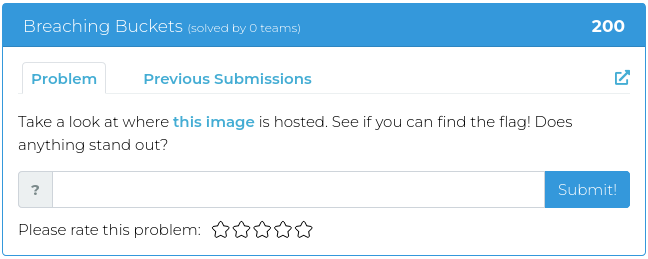
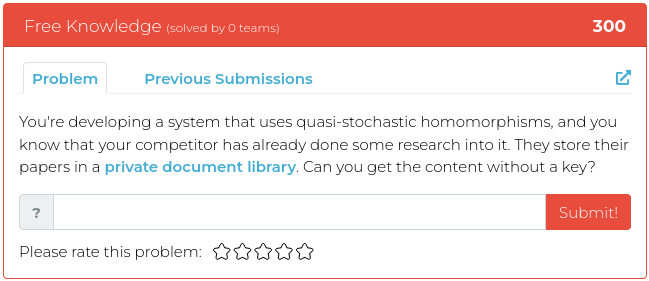
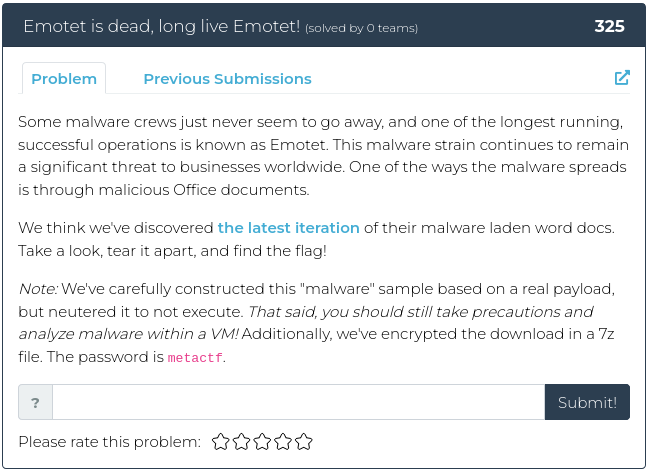
In honor of the Fourth, there are four challenges, each one of a different type. Fourth of July, four challenges, four types of challenges… You get the idea.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.antisyphontraining.com/cyber-range/
June 3, 2022
Hello everyone!
First Wild West Hackin’ Fest (WWHF) Way West, then Memorial Day Weekend… It seems like this year is just flying by! But fear not! We still have challenges to help you keep your haxor skilz sharp and frosty, no matter how hot things get.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
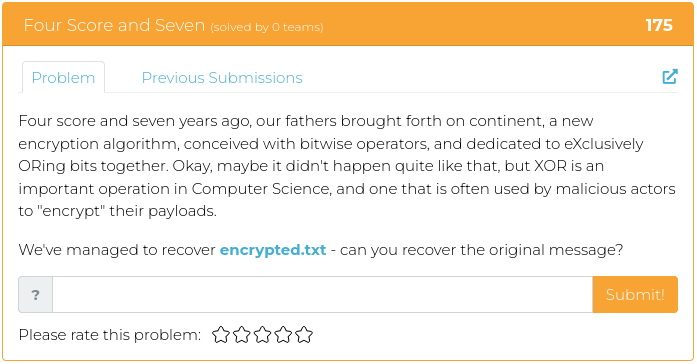
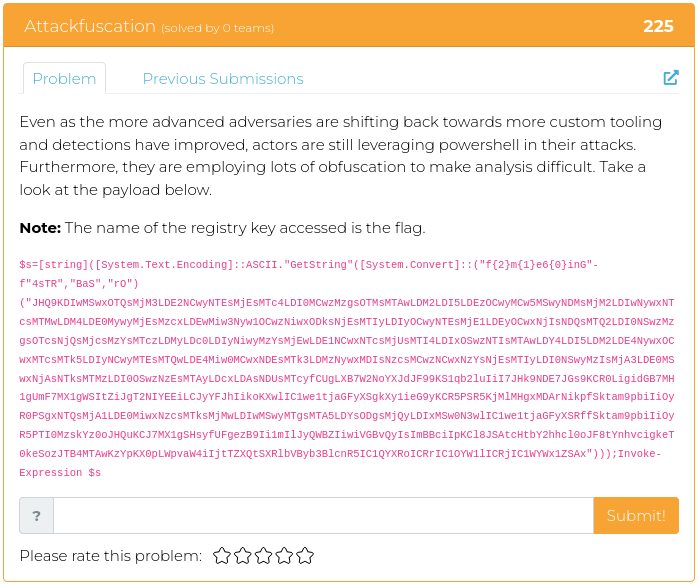
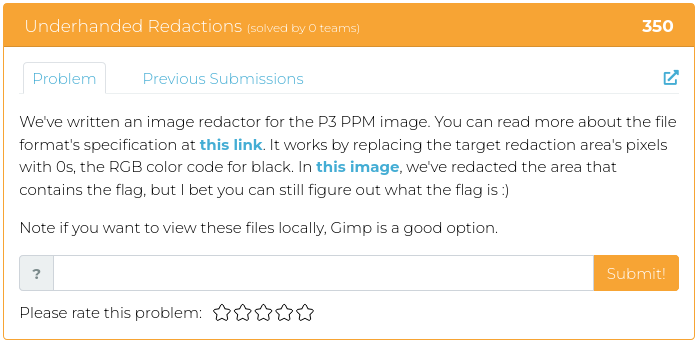
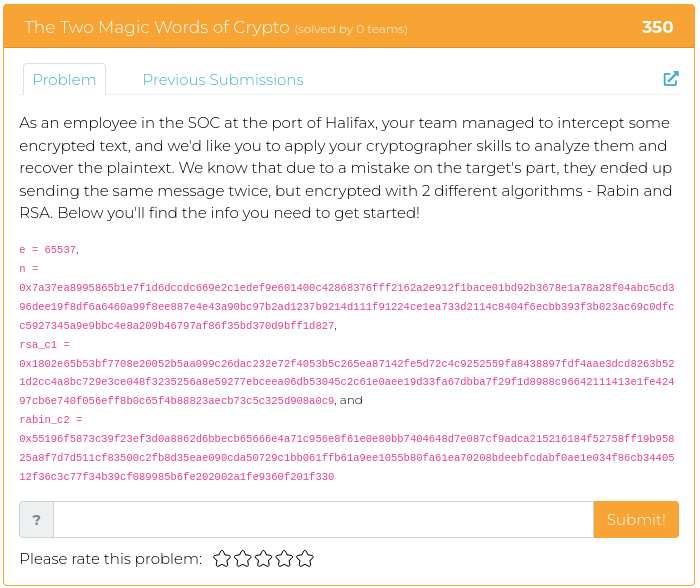
May 13, 2022
Hello everyone!
Whew! Last week at WWHF Way West was an absolute blast! And MetaCTF brought their “A” game, as usual!
If you didn’t get enough CTF excitement last week, or if you just feel like challenging your paraskevidekatriaphobia (fear of Friday the 13th), this week we are releasing four reverse engineering challenges for your enjoyment.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
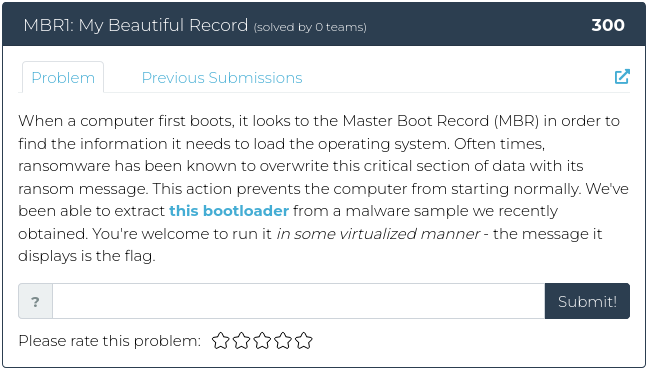
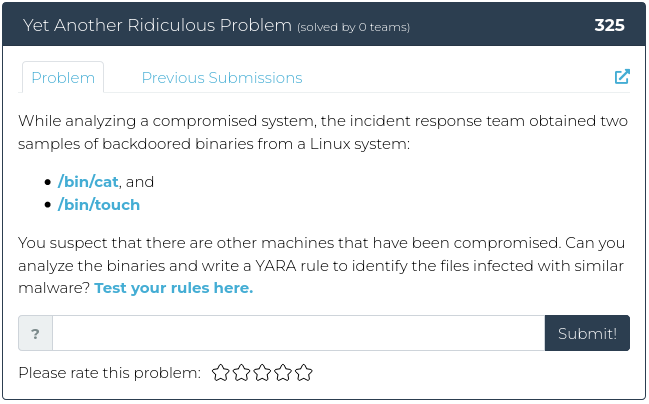
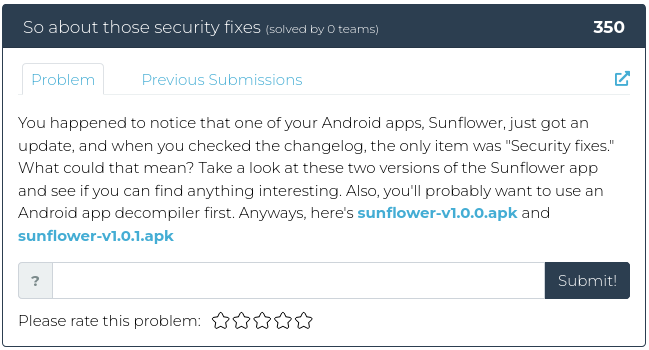
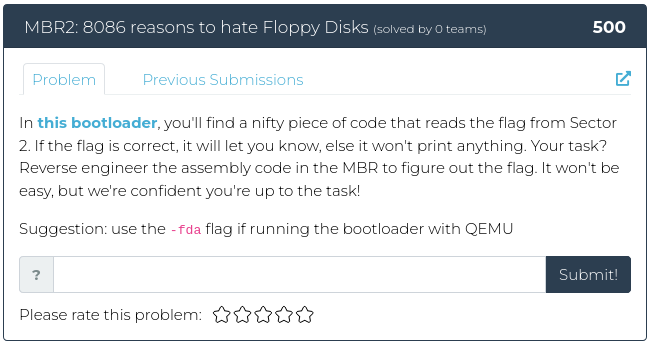
April 22, 2022
Hello everyone!
This week we’re back to the usual number of challenges being released, and they are all slightly different flavors. There’s a little bit of recon, a dash of crypto, some reverse engineering, with forensics on the side. Yum!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
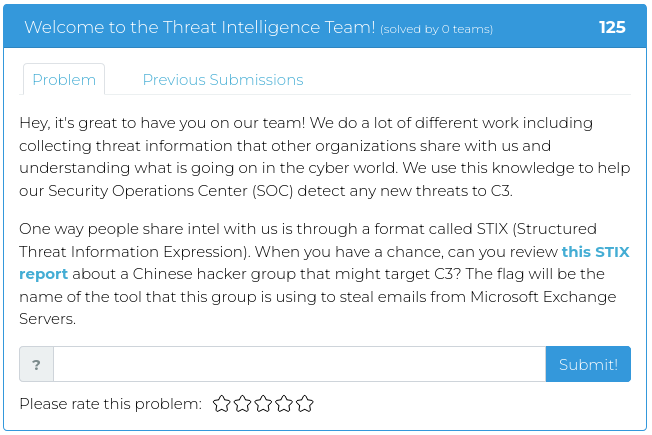
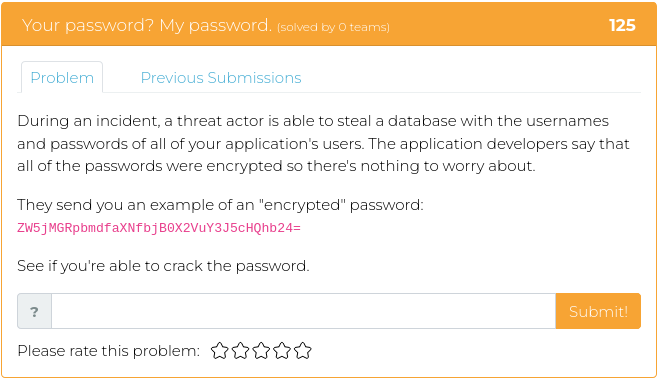
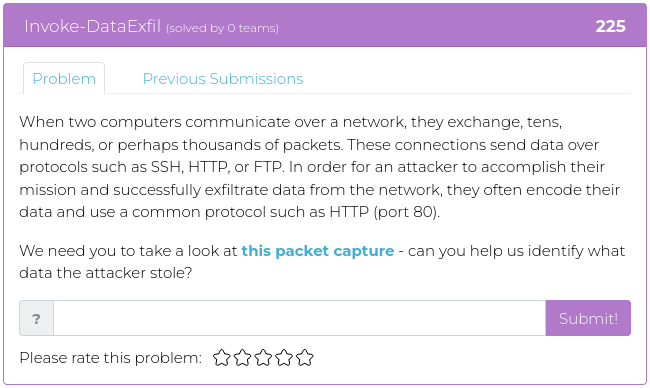
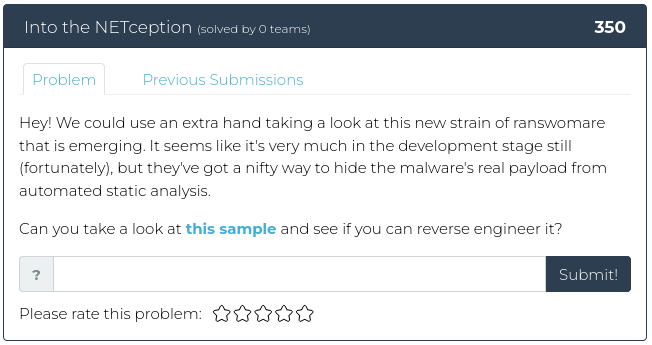
April 1, 2022
Hello everyone!
Whew! March was super intense! With so many exciting things going on, you may have thought we forgot about releasing new challenges for your fun and entertainment. But no! In fact, we are releasing eight challenges to get April off to a rampaging start!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
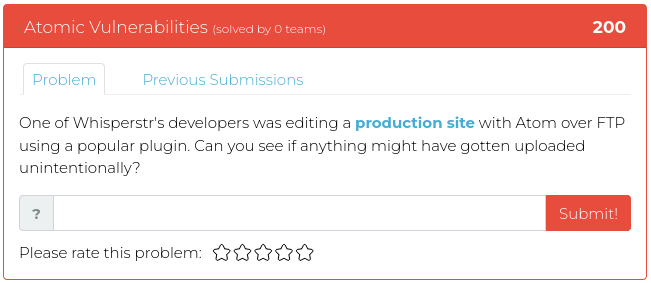
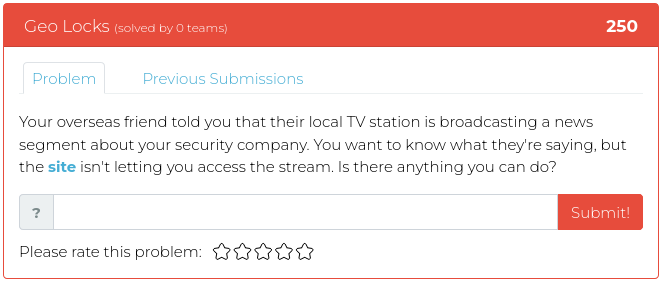
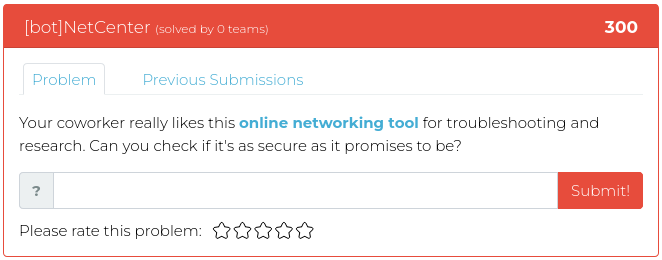
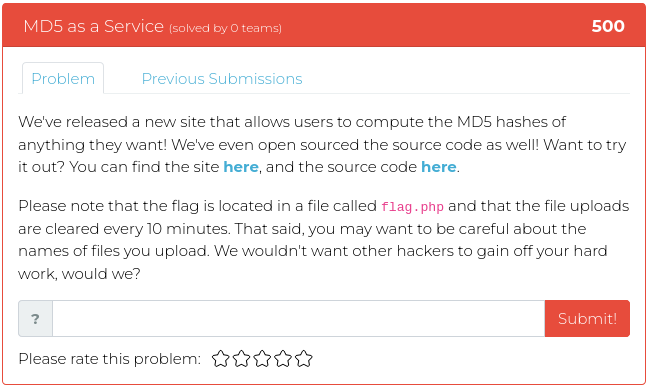
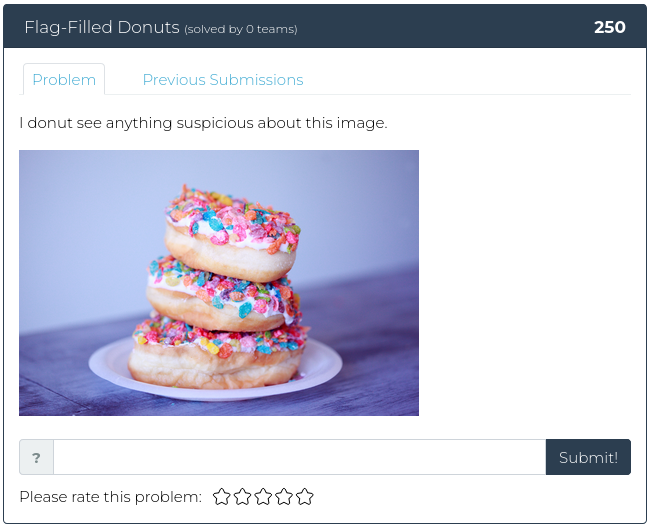
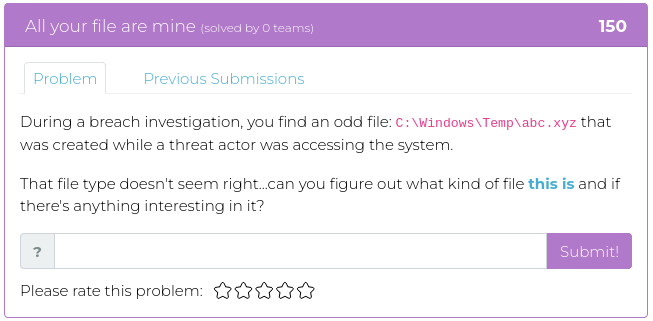
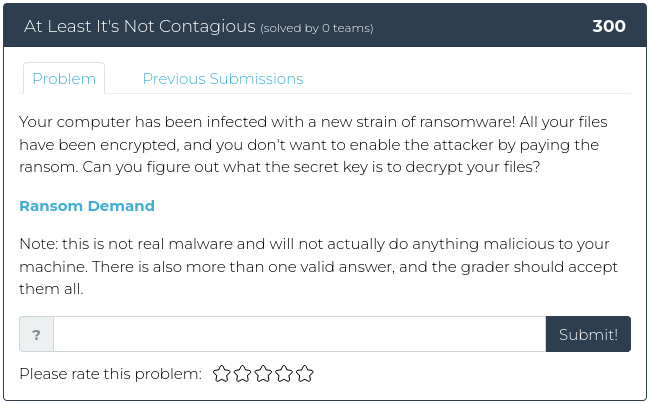
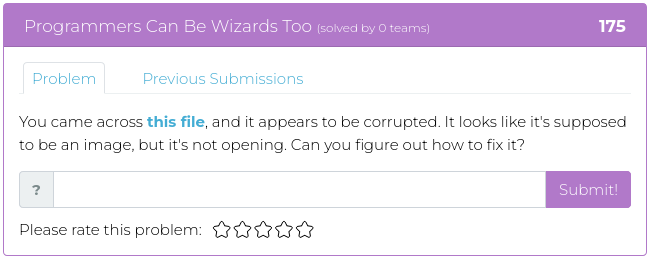
February 25, 2022
Hello everyone!
Although February is the shortest month of the year, this week’s release has a little something extra for you. Normally, we try to release four challenges at a time, but this week we’re serving up five for your hacking pleasure! There isn’t a specific theme, just a nice mix of exploits that are on the challenging side to help keep you warm on a chilly day (or night).
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
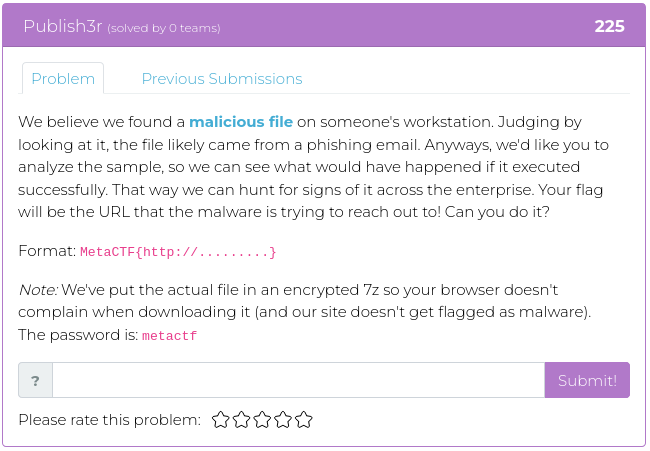
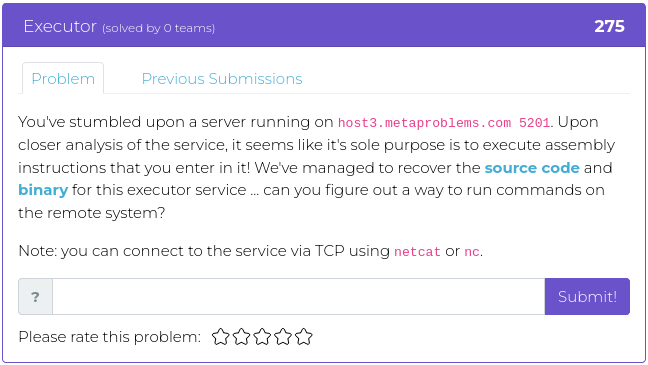
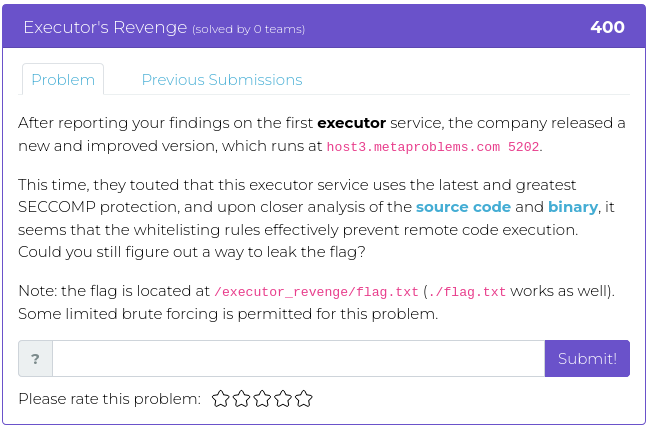
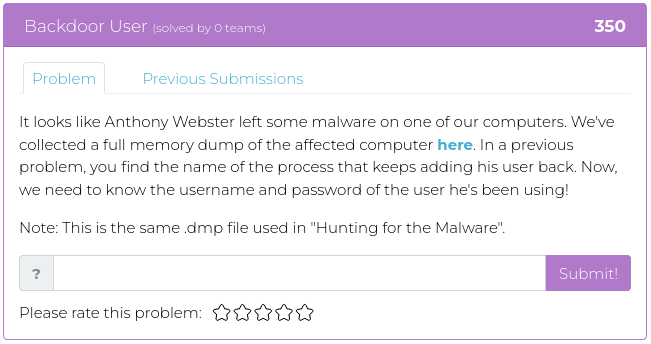
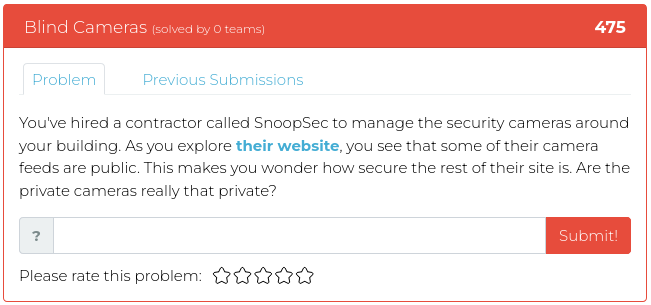
February 11, 2022
Hello everyone!
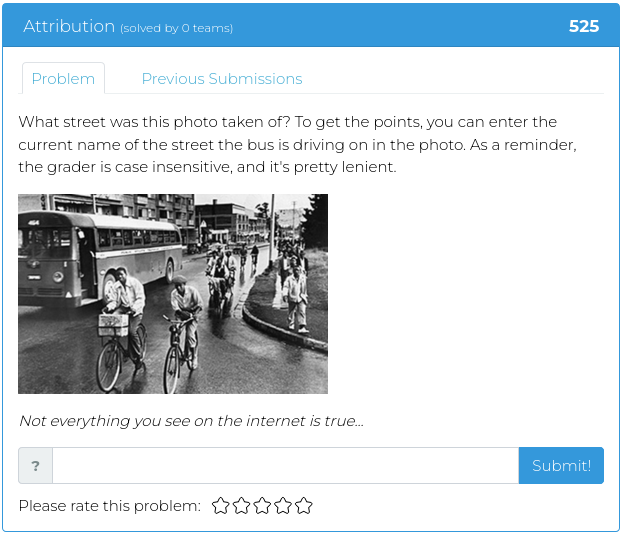
If you enjoyed our last release, you will probably like this week’s, too. Most of this week’s challenges also have to do with reverse engineering software, but this time using Python rather than Assembler. As an added attraction, though, the fourth challenge will test your sleuthing skills to find where a specific photograph was taken.
The image you need to investigate relates to specific events during the civil rights movement in the 1950s, and, in honor of Black History Month, we encourage you to use this challenge to not only figure out where the photo was taken so you can get the points but as an opportunity to learn a bit about the political and social events of those times.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
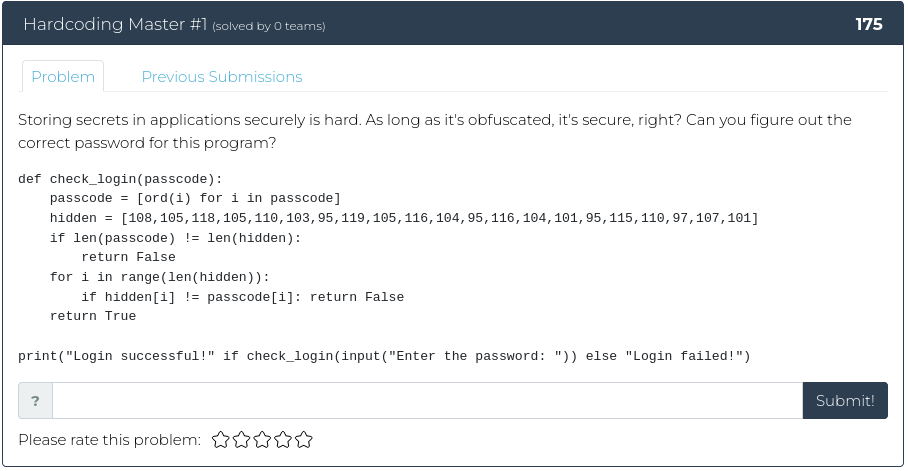
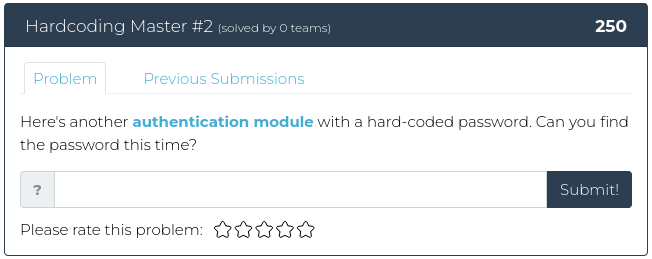
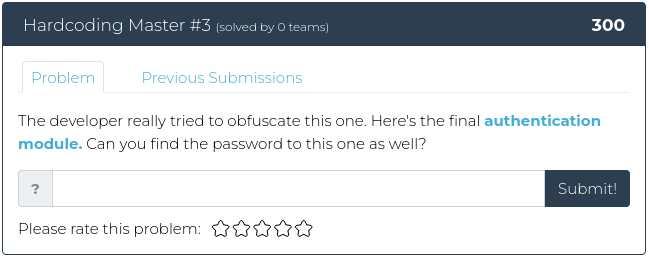
January 28, 2022
Hello there, you happy hacker folk!
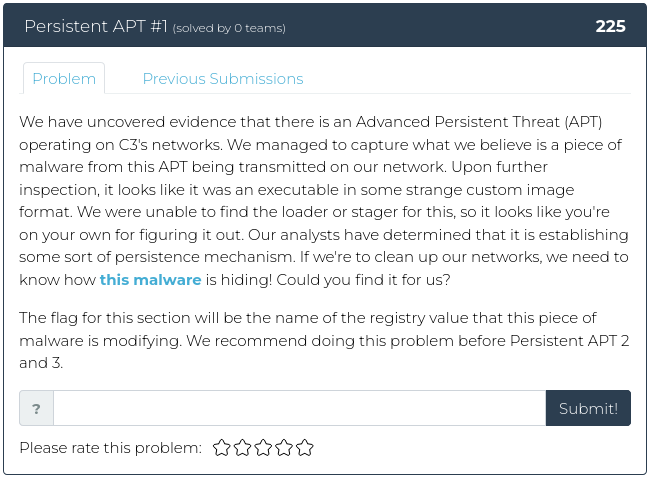
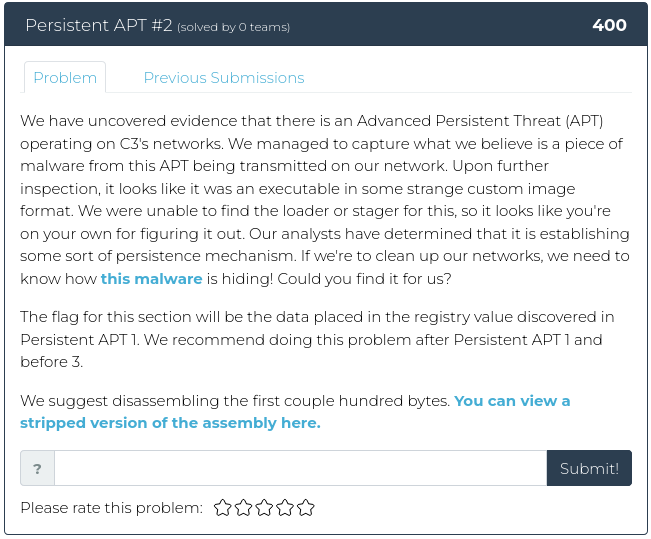
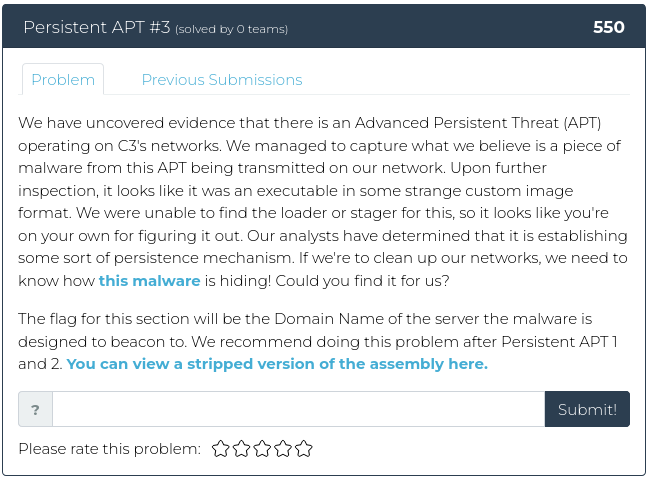
As promised, this week we are decidedly NOT taking it easy on you. For this week’s release, we have three related reverse engineering challenges, plus a web exploitation problem. The first reverse engineering problem is the easiest. From there, we crank things up to 11.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
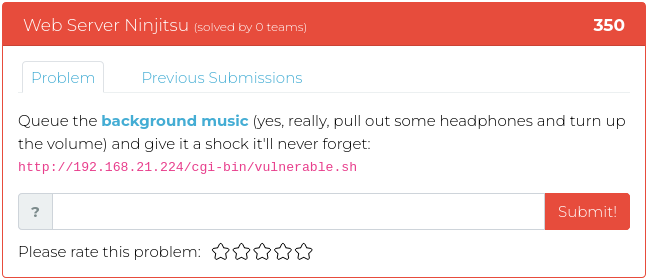
January 14, 2022
Hello and Happy New Year!
We hope your holidays were filled with all good things, and to get the New Year off to a good start, we thought we would take it a little bit easy on you for the first challenge release of the year. This week’s release has some forensics, some web exploitation, and some cryptography for spice. But don’t think we’ll take things easy on you for long. We have some goodies in the queue guaranteed to make your skull sweat! 😆
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
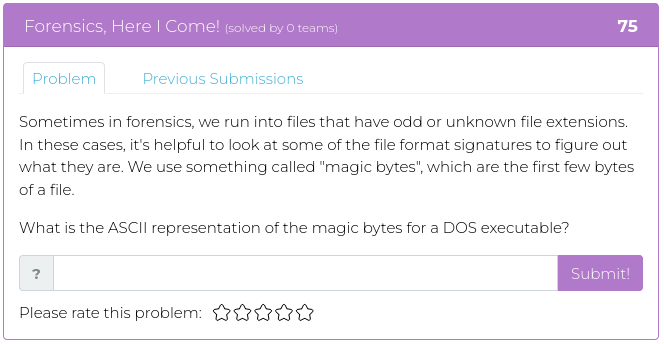
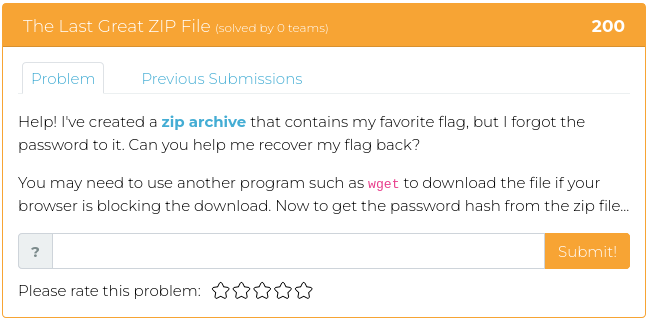
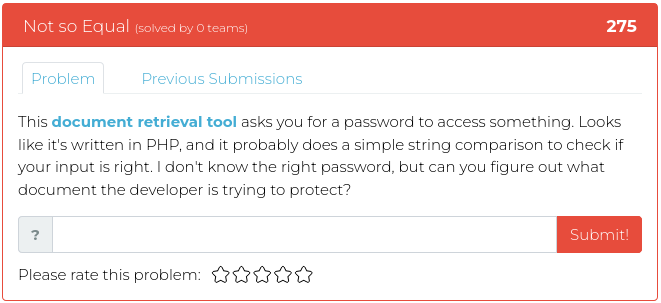
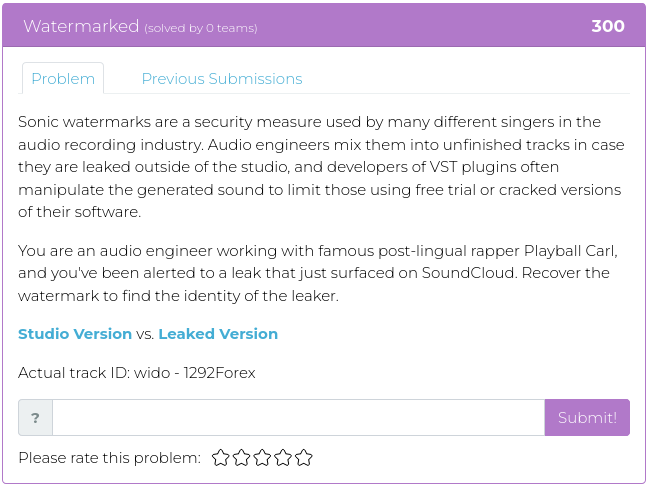
December 24, 2021
Hello everyone!
We hope you all are enjoying the wide variety of CTFs available this holiday season. ✨ Not to be outdone, we’ve released more challenges in the Cyber Range for your continued enjoyment, entertainment, and elf-like enthusiasm! Granted, we didn’t exactly wrap them up with shiny paper and ribbons, but they are timed to give the guy in the red suit a little bit of a break. 🎅
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
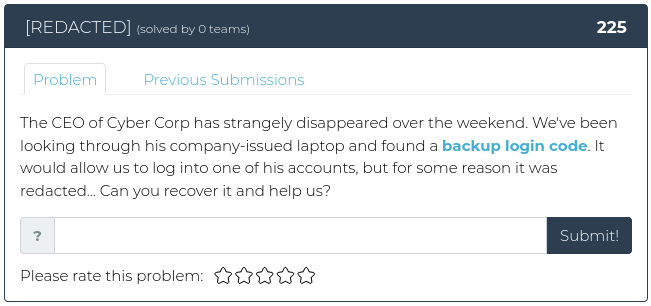
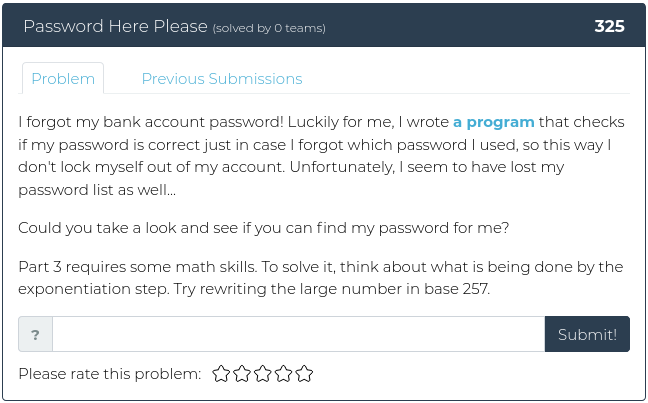
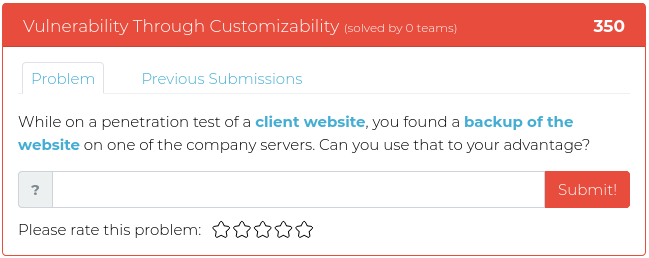
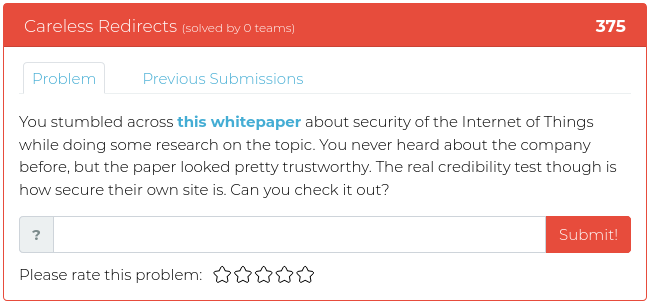
December 3, 2021
Hello everyone!
As you may have heard, the Cyber Range has a new home and is now being hosted by MetaCTF. We took a little extra time to let the dust settle, but now we’re confident that the Ts and crossed and the Is are dotted, and it’s time to release a new batch of challenges for you.
This week we have four new opportunities for you to explore the world of binary exploitation, so fire up your reverse engineering tools and dive in!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
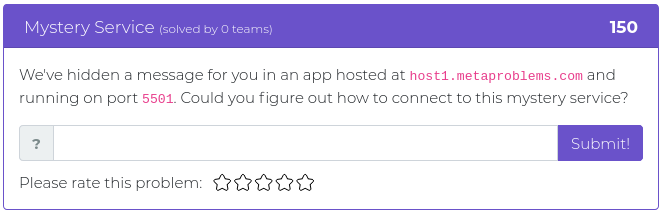
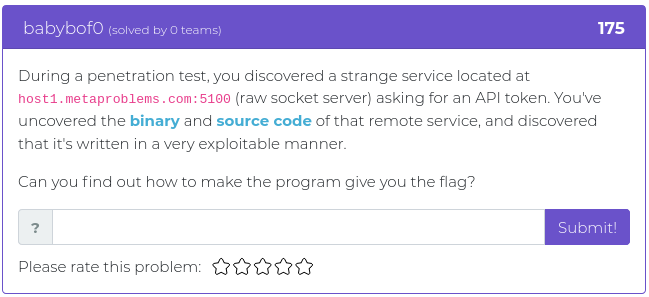
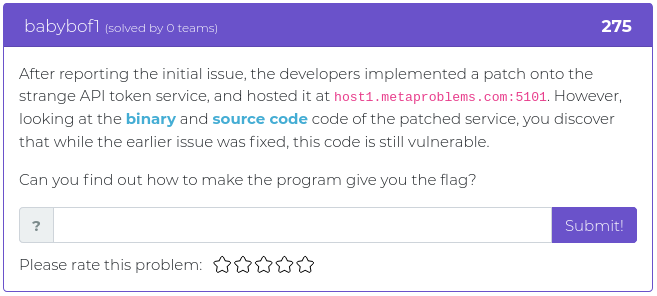
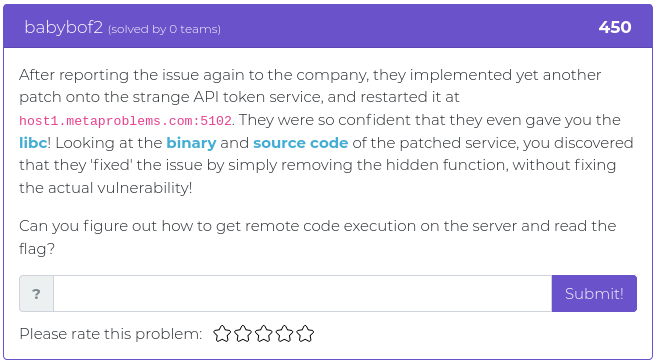
October 29, 2021
Hello everyone!
Halloween is this coming Sunday, October 31, and this week’s release of challenges is a special treat with an assortment of flavors for your fun and entertainment. We have hashes and matrices and algorithms. The flavors run the gamut from crypto to web exploitation. And we threw in an extra challenge, so this week you get six shiny new additions instead of the usual five. We like to think of it like we’re giving out full sized candy bars instead of the smaller, “fun-sized” treats.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun! 🎃
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
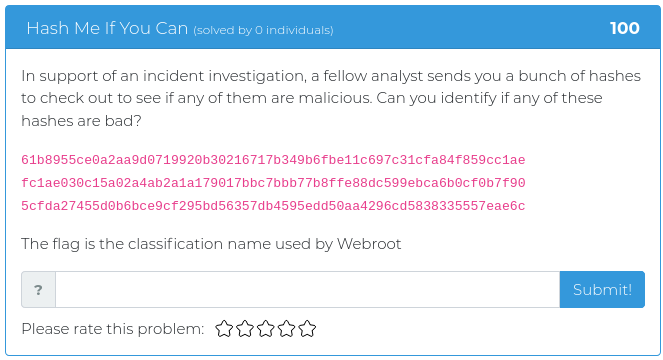
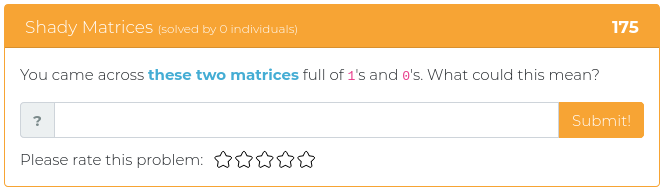
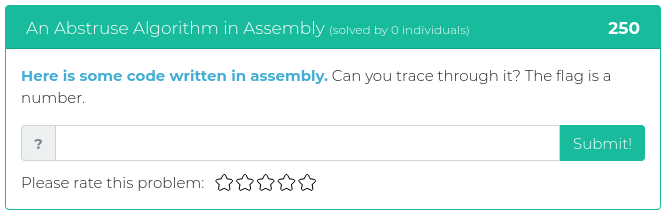
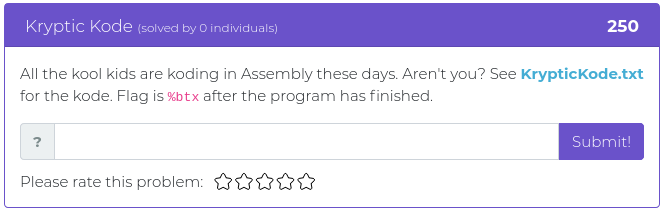
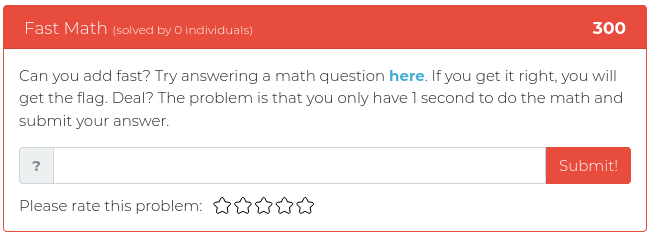
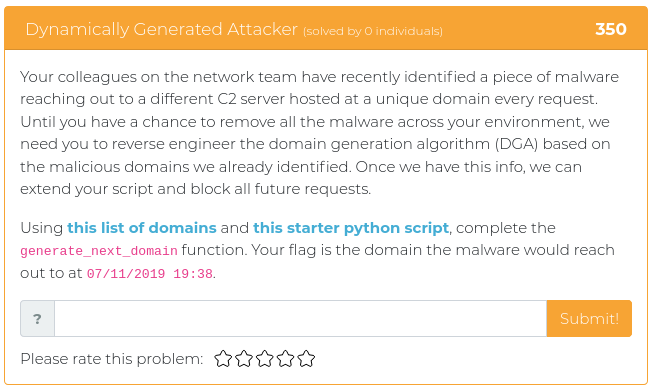
October 19, 2021
Hello everyone!
Did you know that October 15th was National Grouch Day? The good news is that unlike Oscar’s choice in décor, this week’s challenges aren’t garbage! No offense to the Number 1 grouch on Sesame Street but they do live in a trash can, after all.
This batch of freshly baked pumpkin spice challenges is heavy on the forensics, with some cryptography and web exploitation fun for added variety and flavor.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
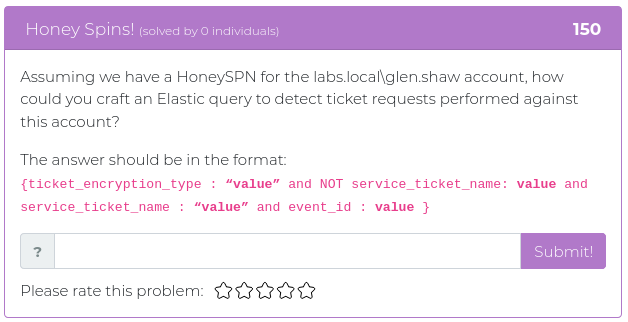
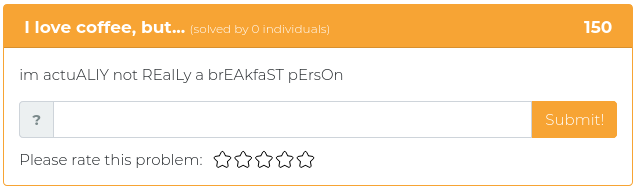
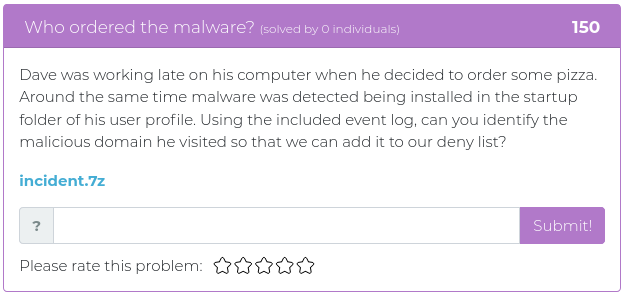
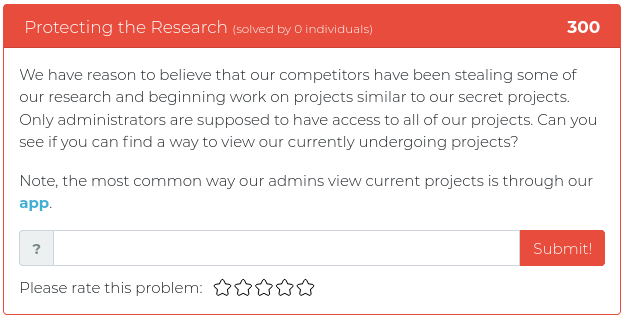
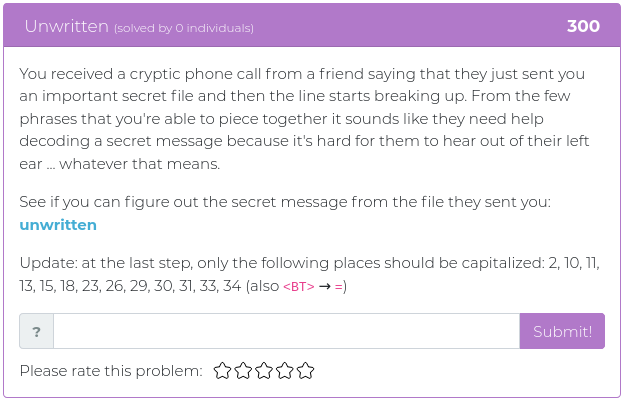
September 28, 2021
Hello everyone!
We hope you were able to join us for WWHF Virtual Deadwood. Now that the conference is over, we know you will be pumped and primed for lots of new and cool hacking challenges, and this week’s release is loaded with heavyweights! That’s right! Every single challenge in this week’s release is worth 300 points or more.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
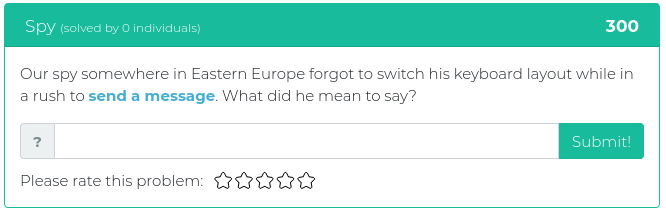
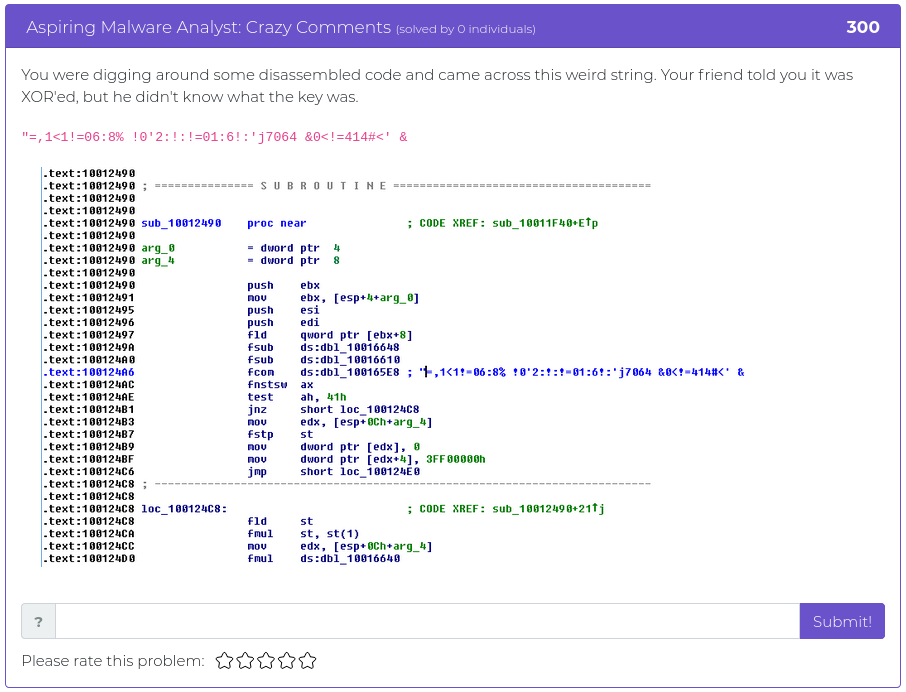
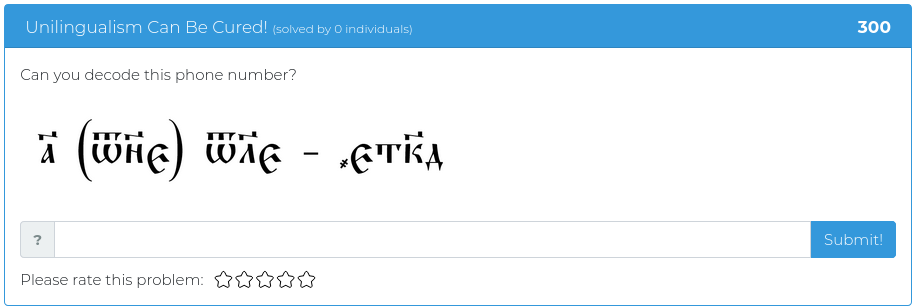
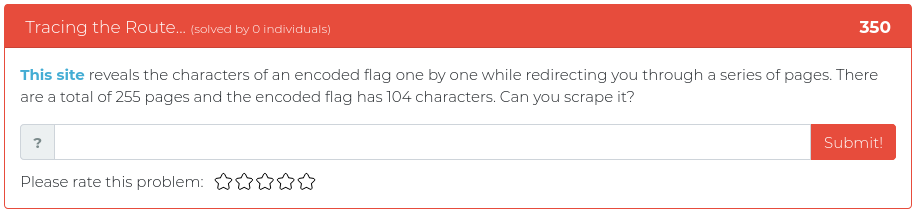
September 10, 2021
Hello everyone!
If you thought we forgot about releasing a new set of Cyber Range challenges last week, think again! We have been SO busy getting ready for Wild West Hackin’ Fest, then there was the Labor Day Weekend… It’s been cRaZy! Fun, but crazy!
It’s still crazy, but we know that you depend on these releases, so here is another batch of shiny, new challenges featuring reverse engineering, reconnaissance, and cryptography to help you hone your cyber-sleuthing synapses.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
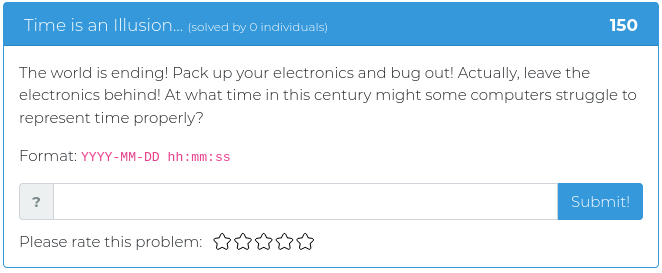
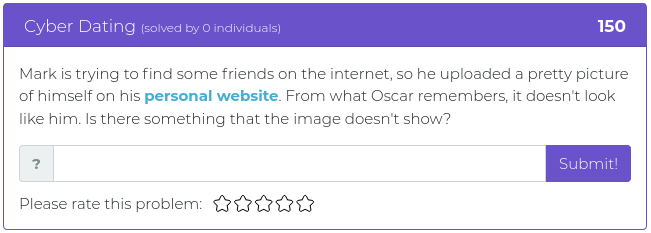
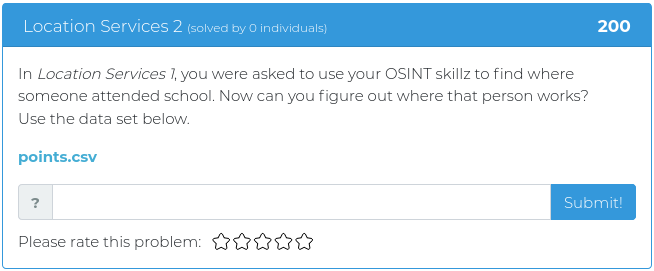
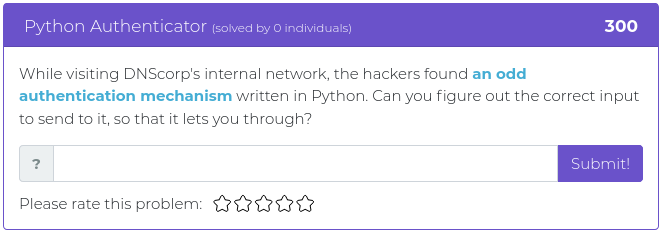
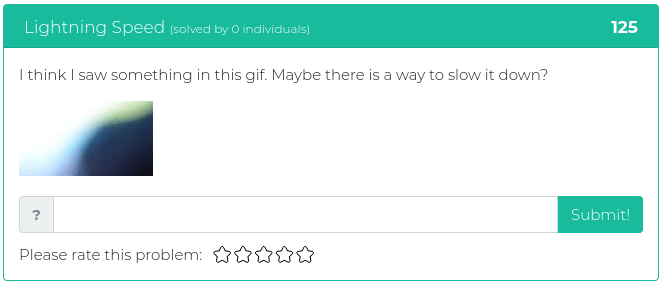
August 20, 2021
Hello everyone!
This week’s release includes mostly heavyweight challenges, with four out of five weighing in at 300 points or more. The heaviest one is worth 600 points, so hopefully, your brain will break a sweat, and the lightest one is only 125 points so you don’t overheat your brain too much.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
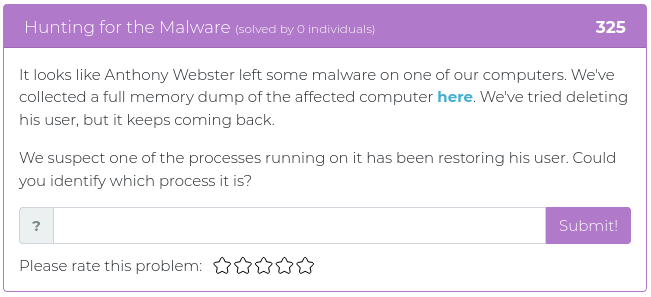
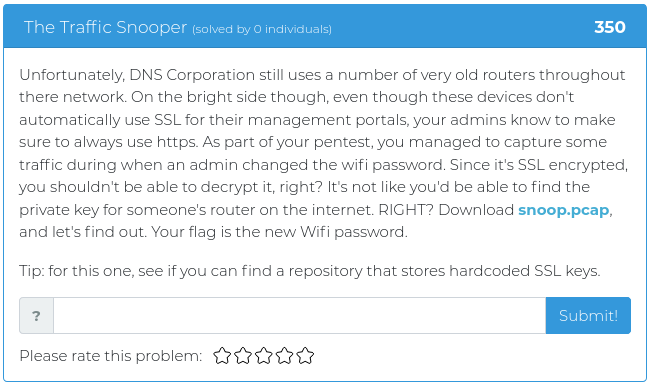
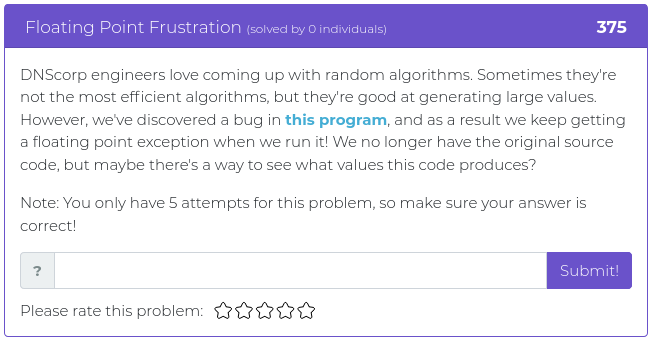
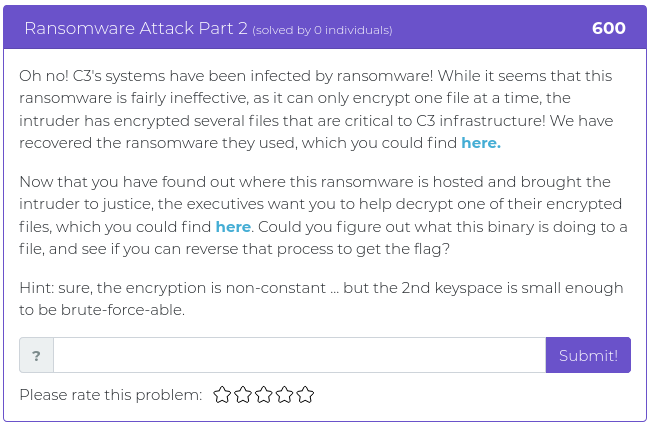
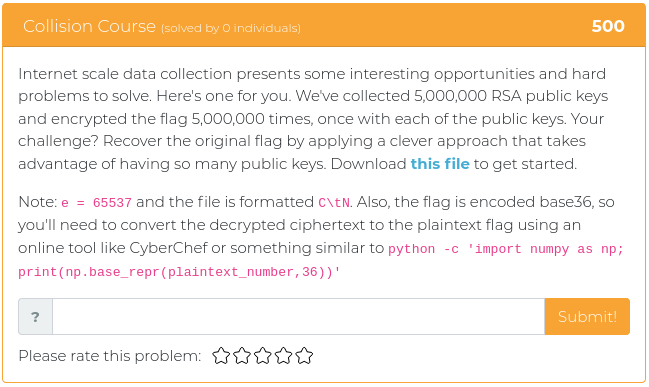
August 6, 2021
Hello everyone!
The last batch of challenges were a little bit more challenging than usual, so this time around we are releasing some easy ones to make up for it. This week’s challenges are worth 250 points each or less, but that doesn’t mean they won’t make you stop and think. Don’t forget, even simple mistakes can still throw a wrench into the works.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
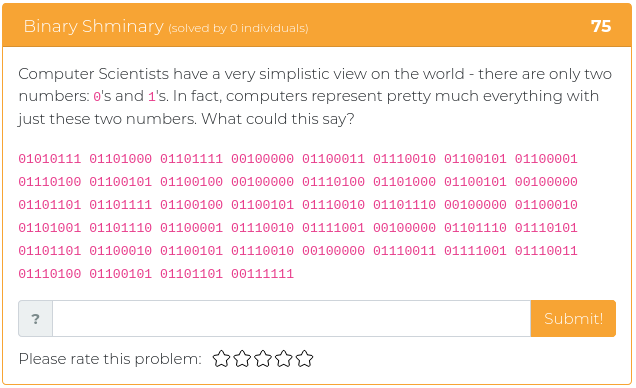
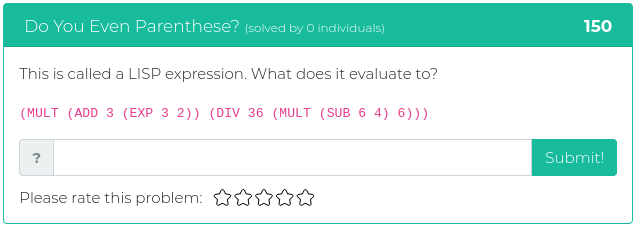
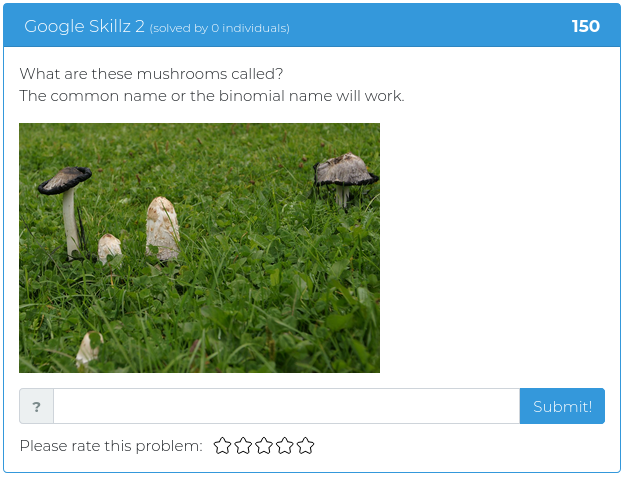
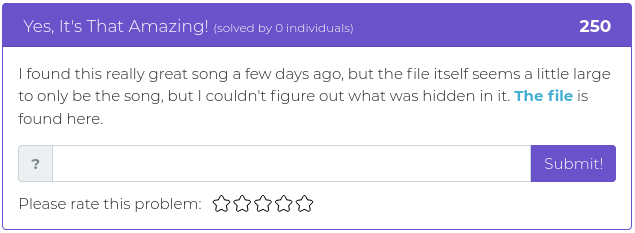
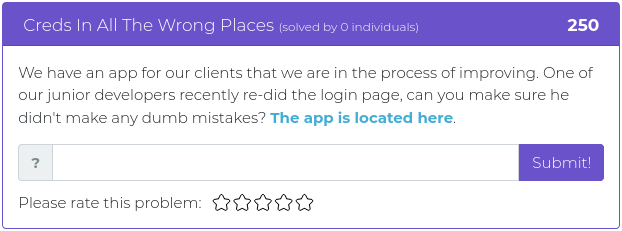
July 23, 2021
Hey folks,
This week’s batch of challenges is a bit tougher than usual. Every single challenge in this week’s release has a point value over 350, which means they are all extra tricky and guaranteed to make your skull sweat. They are all either reverse engineering or forensics problems, as well, which might seem to some to be unfair, or cruel, or just plain mean, but we have faith that you are up to the task. Now go out there and show us what kind of hacking rockstar you are!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
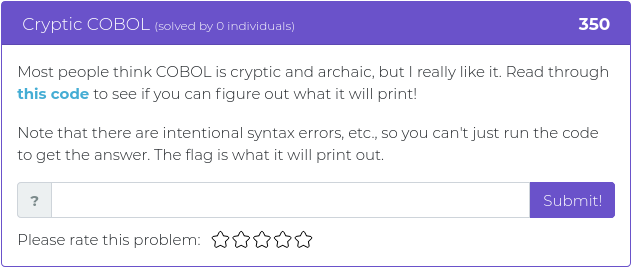
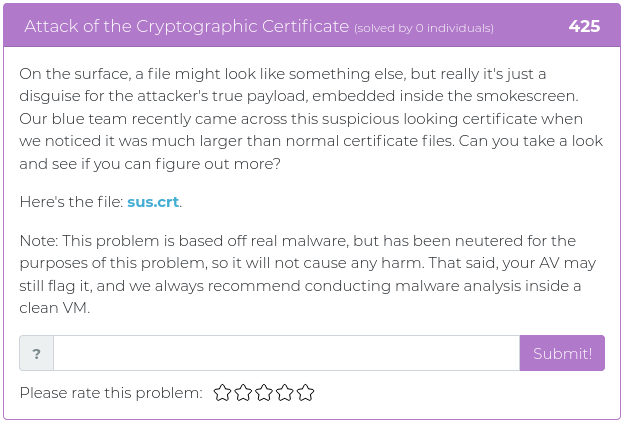
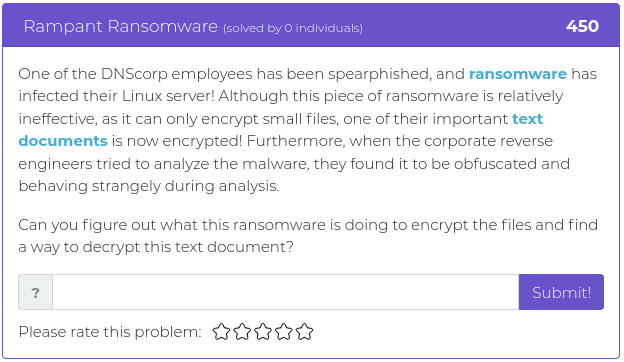
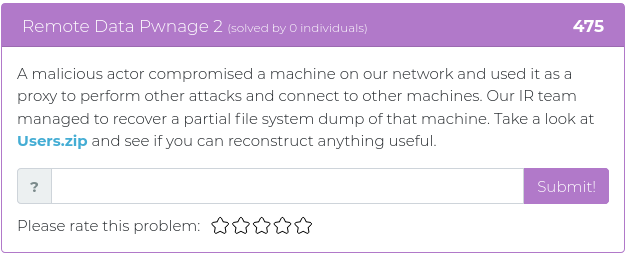
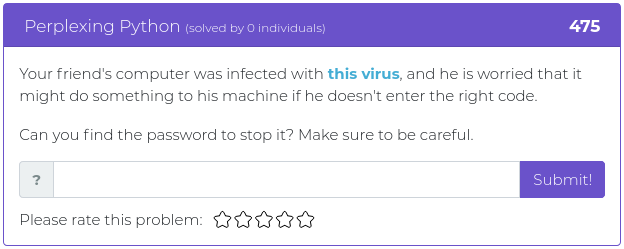
July 9, 2021
Hey folks,
The last batch of challenges we released were all about web app exploitation, and this week’s new challenges are all of a theme, as well. It’s time to dust off your cryptography and phone phreak skills, with a little stego thrown in for spice!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
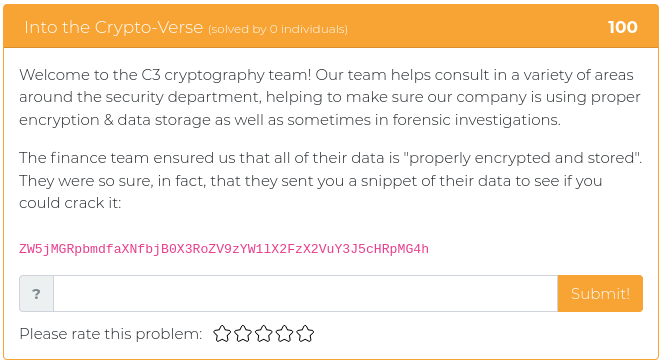
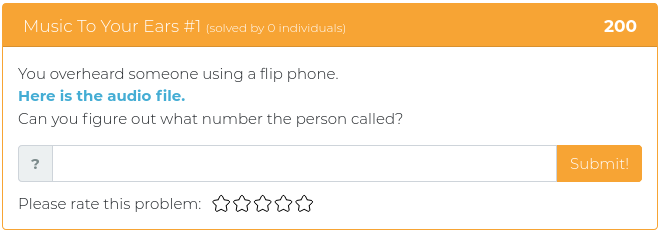
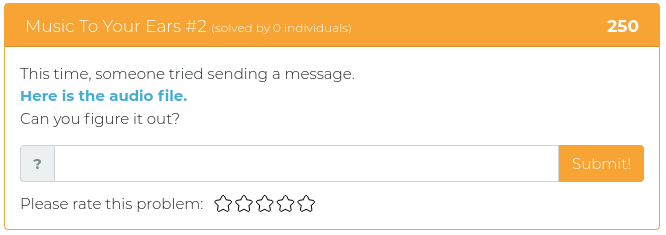
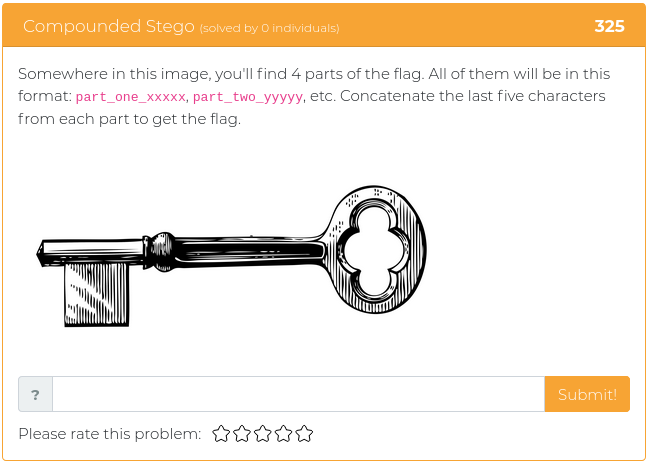
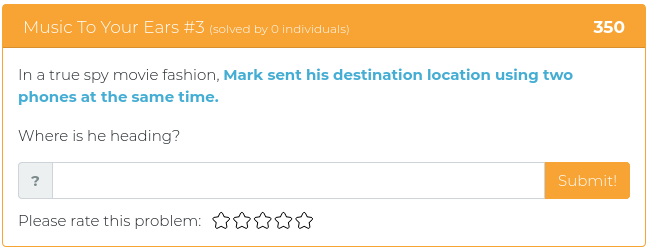
June 25, 2021
Hey folks,
The last batch of challenges we released were all about reverse engineering, and this week’s new challenges are all of a theme, as well. It’s time to dust off your web application, developer, and API programming tools so you can do some serious web app exploitation!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
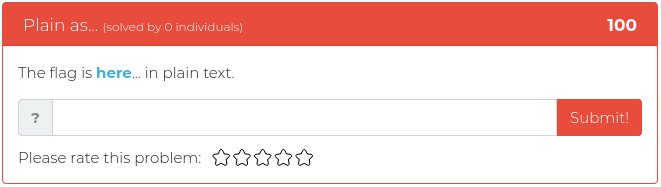
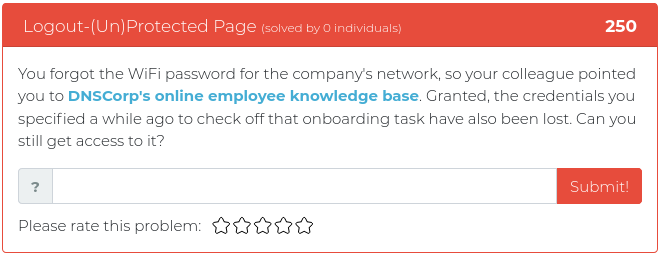
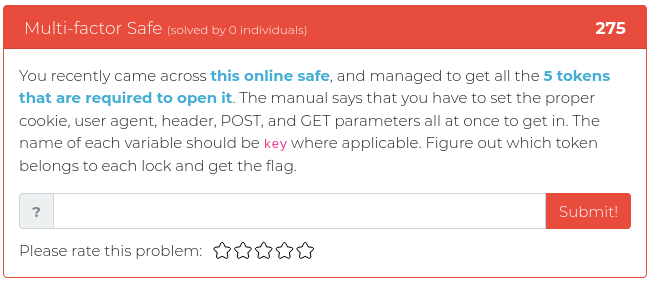
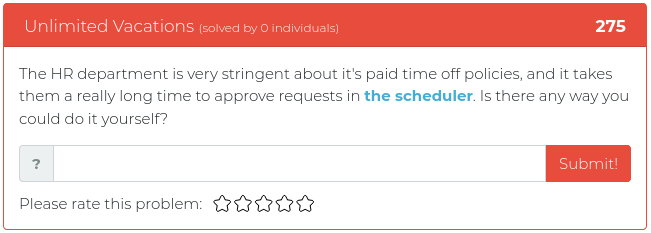
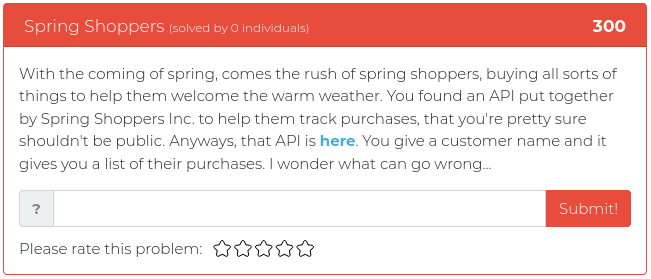
May 28, 2021
Hey folks,
As you probably know already, Memorial Day is an American holiday observed on the last Monday of May which honors the men and women who died while serving in the U.S. military. All that business with BBQs and picnics all weekend long isn’t really what the holiday is about.
Since you likely have a long holiday weekend ahead of you, we decided to release some challenges that are a bit more “challenging”… just to keep you busy!
This week’s release is mostly about reconnaissance, but we threw in some reverse engineering and some math fun, just for spice.
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
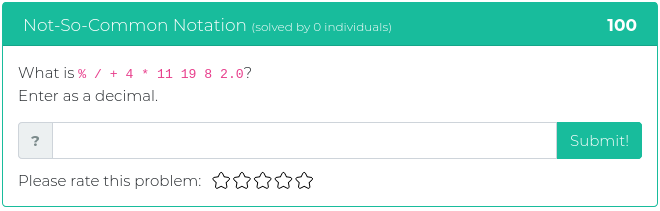
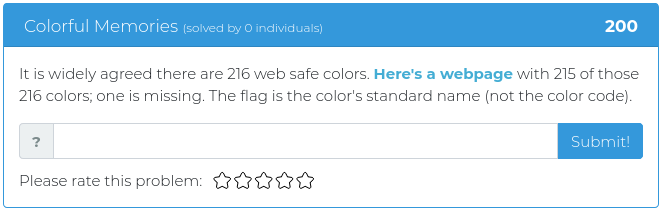
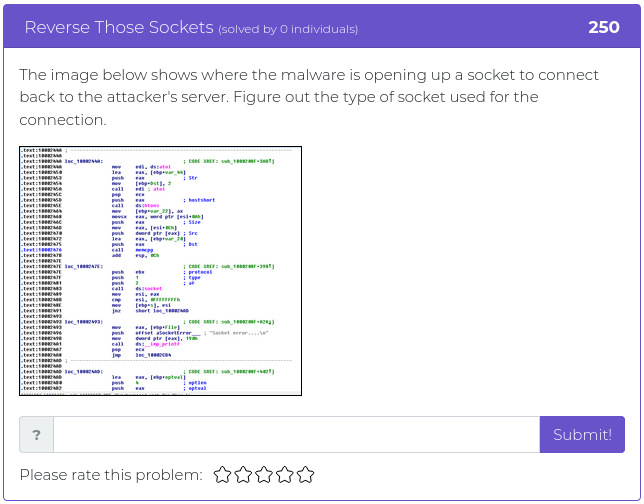
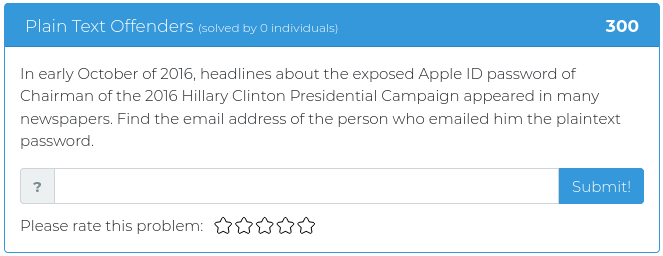
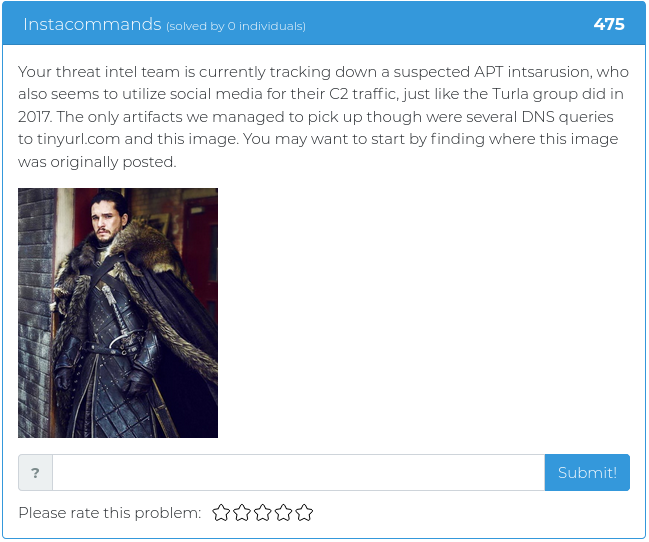
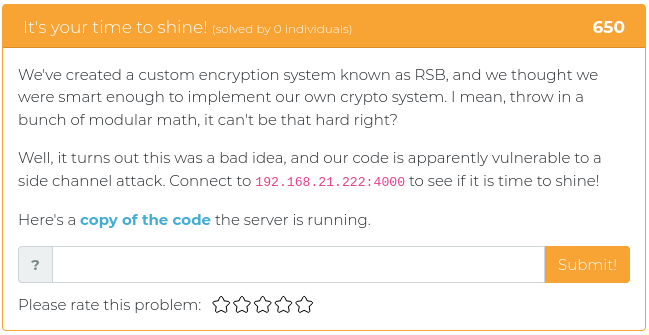
May 14, 2021
Hey folks,
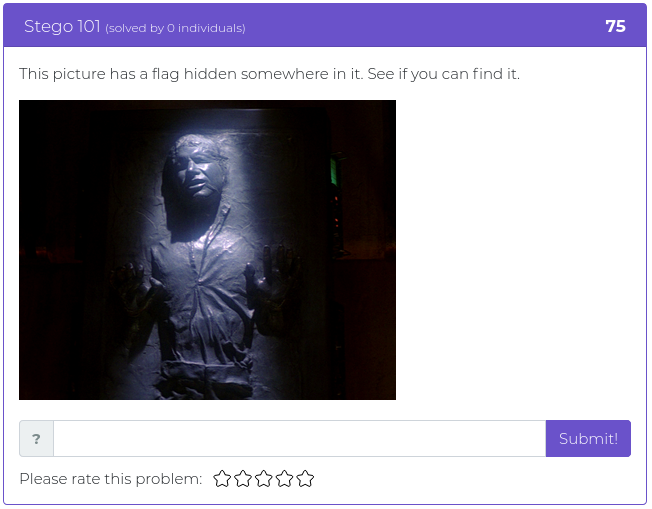
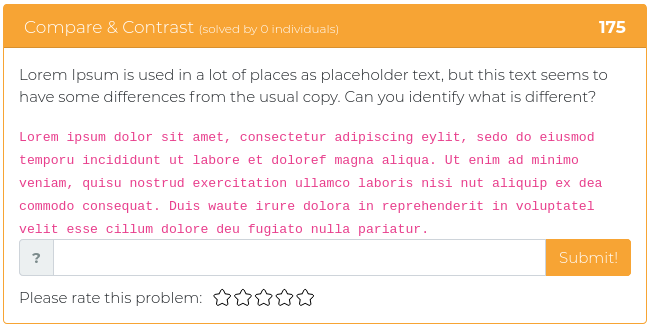
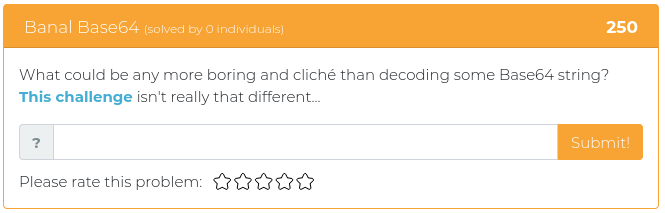
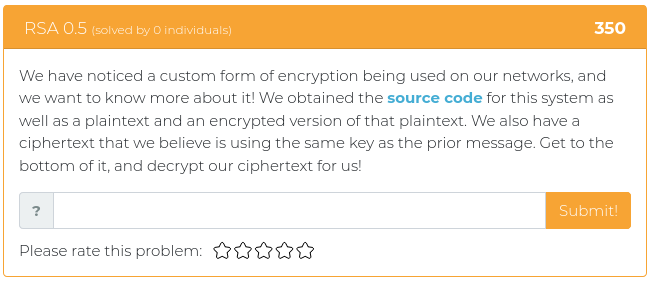
This week’s challenges are mostly about cryptography. Test your mettle against some seemingly simple Base64 encoding, find the extras embedded in a well-known passage that has been used by typesetters since the 1500s, and help out some poor folks who thought building their own encryption system was a good idea. Fun times!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
April 30, 2021
Hey folks,
It’s that time again. For this week’s new challenges, we have a couple of web exploitation tasks, some crypto for those of you who like to hide things, and a forensic quest to help a star-crossed lover. Never a dull moment!
For screenshots and descriptions of this week’s additions, see below.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
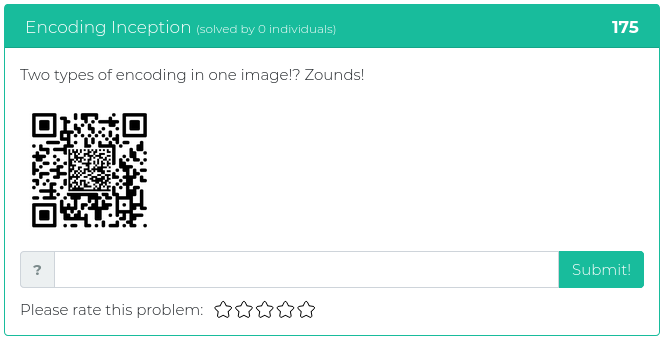
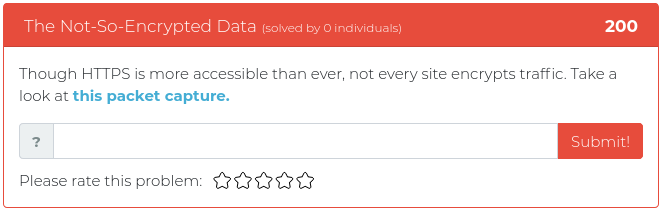
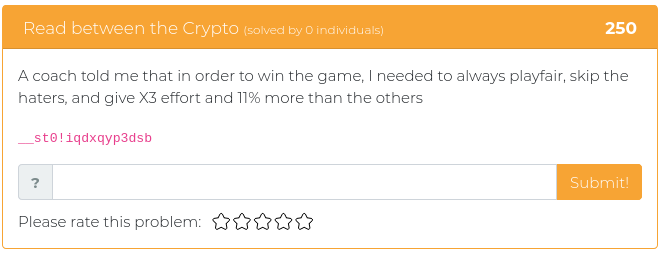
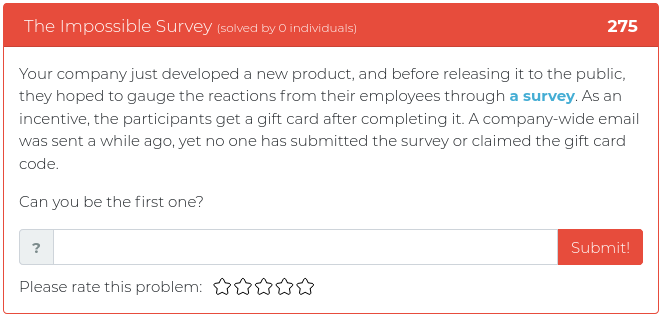
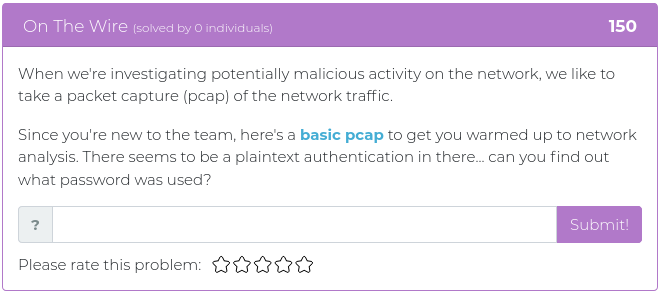
April 16, 2021
Hey folks,
The latest batch of newly released Cyber Range challenges touch on topics relevant to John Strand’s upcoming “SOC Core Skills” class. This is a very popular class that introduces people to key fundamentals used by security operations center (SOC) analysts. To get you thinking like a SOC analyst, this week’s challenges will test your skills at analyzing web server logs and PCAP files and at figuring out how to analyze files that are not exactly what they seem to be.
For more information about John’s class, go to this page:
https://wildwesthackinfest.com/training/soc-core-skills-john-strand/
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
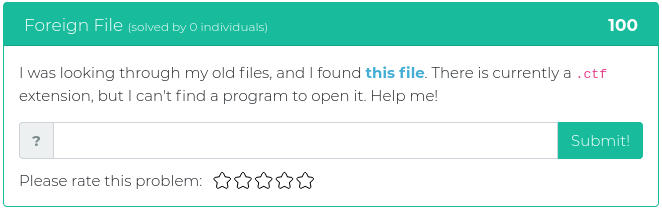
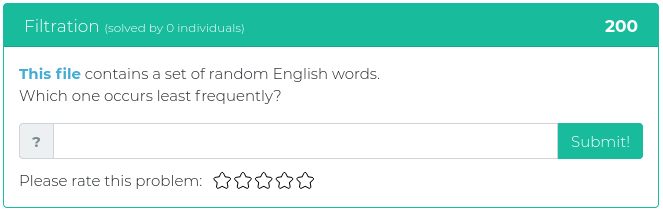
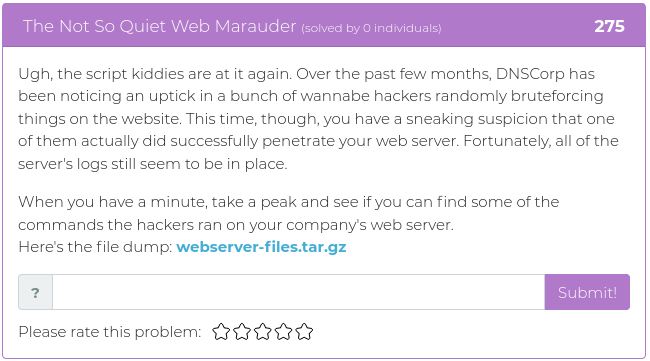
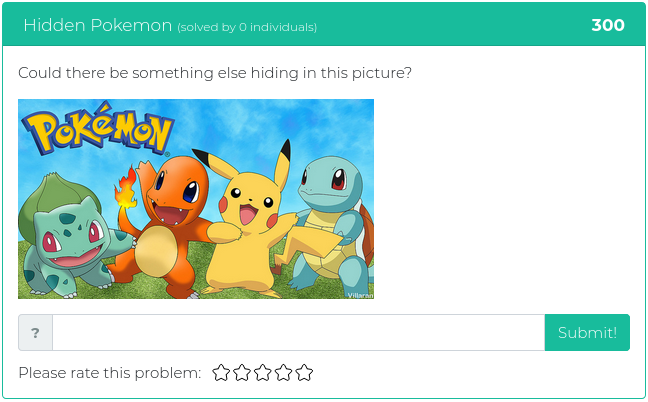
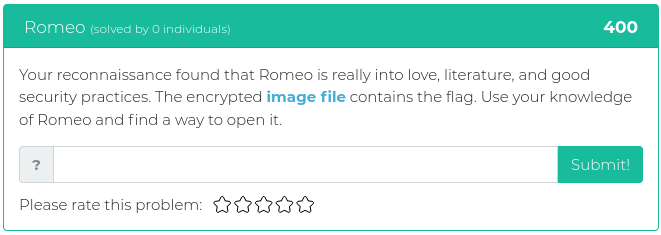
April 2, 2021
Hey folks,
This week’s new challenges are no joke. They have been specially chosen for you to help keep your Red Team skills sharp. You’ll find challenges related to recon, cryptography, reverse engineering, and forensics.
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
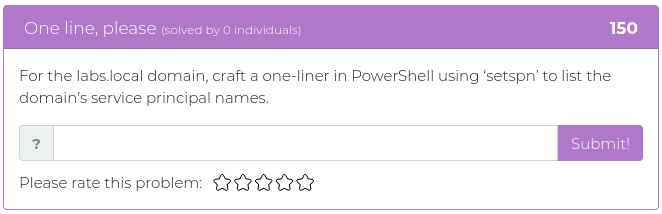
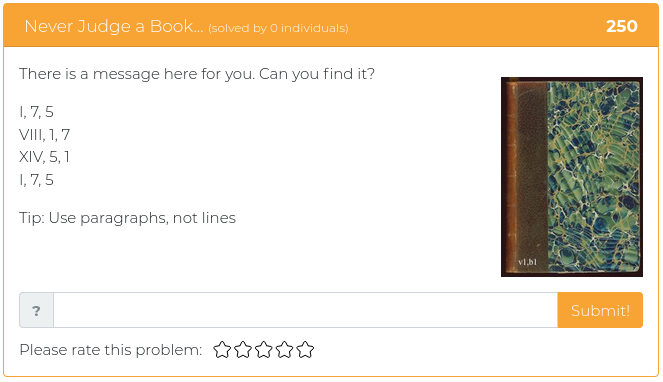
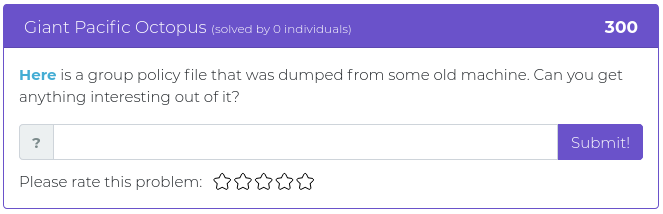
March 19, 2021
Hello folks,
This week we have slightly tougher challenges in store for you. That means more points will be awarded for each problem and better bragging rights when you find the solutions. We wanted to give you some problems that would make your brain sweat!
Good luck and have fun!
The Cyber Range Team
P.S. If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun:
https://www.blackhillsinfosec.com/services/cyber-range/
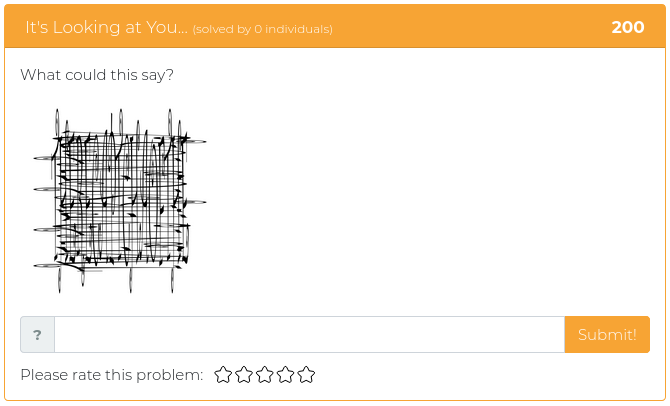
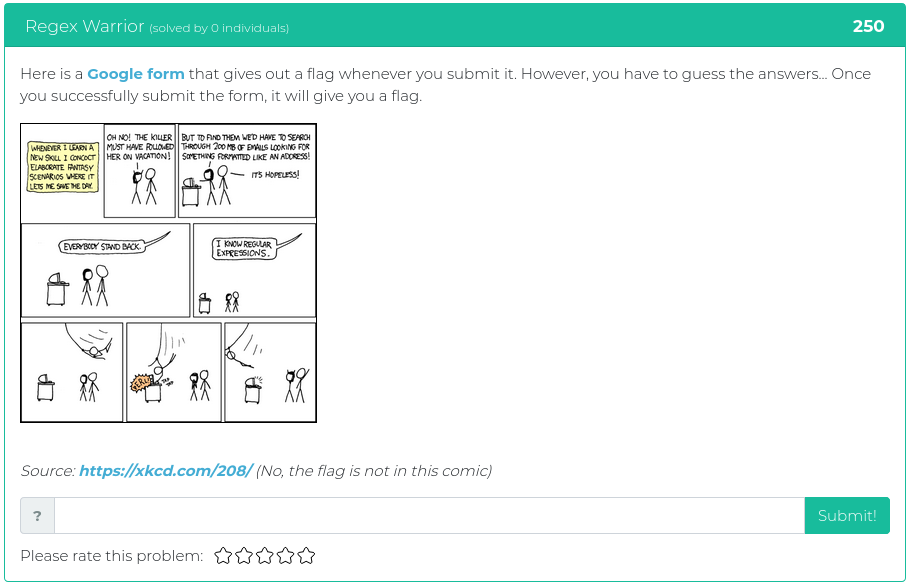
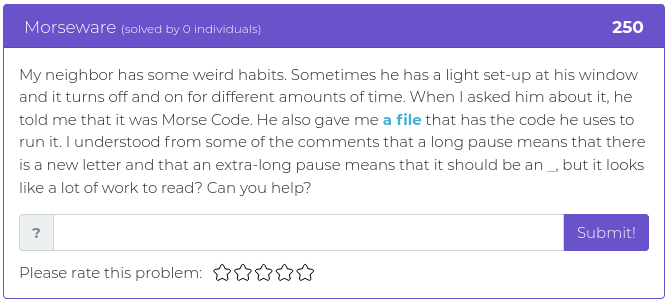
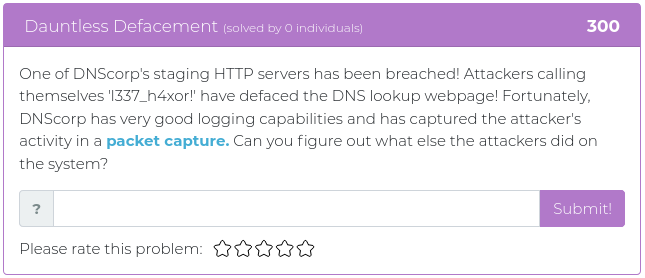
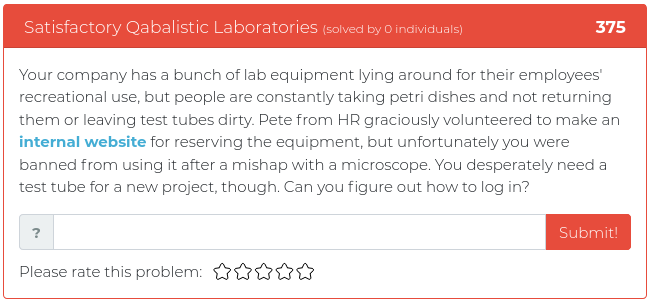
March 5, 2021
Hey folks,
This week’s additions to the Cyber Range have a little of this and a little of that. There’s some recon to see if your Google skills are all that, some web exploitation to see just how sneaky a spider you really are, and a dash of forensics.
Screenshots and descriptions of this week’s new critters are below. Stay tuned for another batch of challenges in a couple of weeks.
If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the action:
https://www.blackhillsinfosec.com/services/cyber-range/
Good luck and have fun!
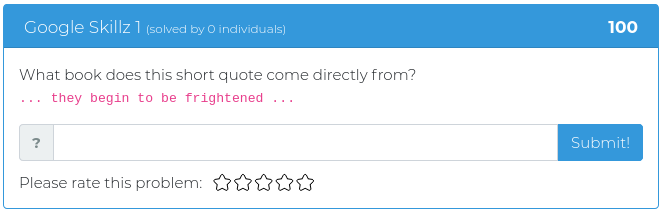
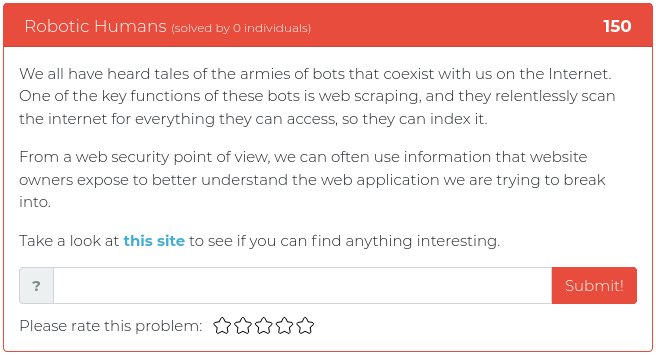
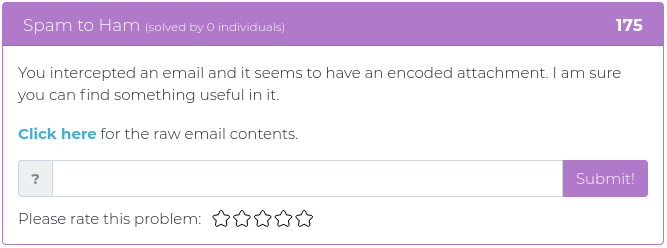
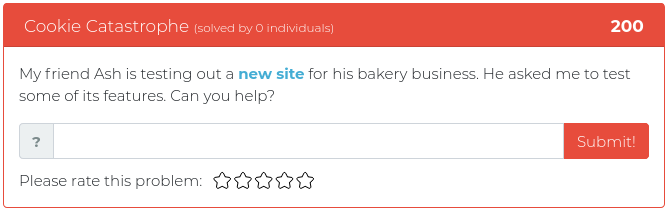
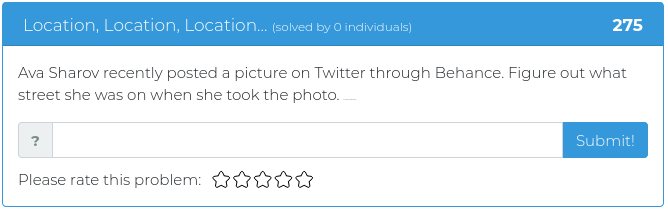
February 19, 2021
Howdy folks,
This week the Cyber Range is pleased to release a collection of challenges that tackle everything from crypto to Kerberoasting! We tried to wrassle up some problems to coincide with Darin and Carrie Roberts’ class about Atomic Red Team and other really cool attack emulation tools, but rustling those challenges was more like bronco bustin’! Score 1 for the broncos.
Not to fear! The latest batch of challenges has a little something for everyone, and we’ll keep working to corral those other varmints just as soon as we can. Until then, set your sights on these rascals. You can find screenshots and descriptions of the new critters below.
If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun:
https://www.blackhillsinfosec.com/services/cyber-range/
And for more info about the Roberts’ class, Attack Emulation Tools: Atomic Red Team, CALDERA and More, go here:
https://wildwesthackinfest.com/training/attack-emulation-atomic-red-team-caldera-and-more/
Good luck and have fun!
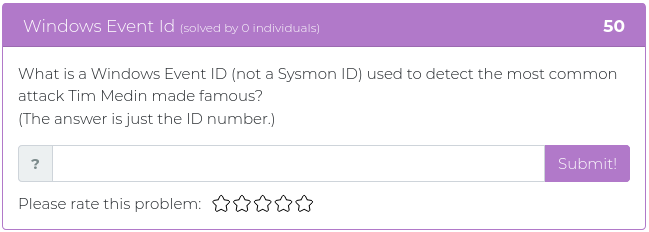
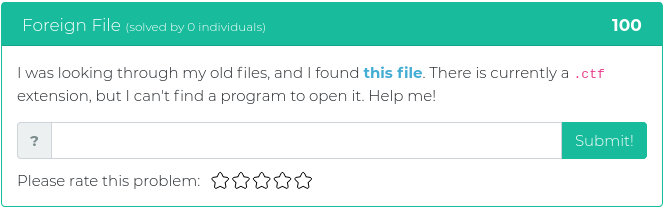
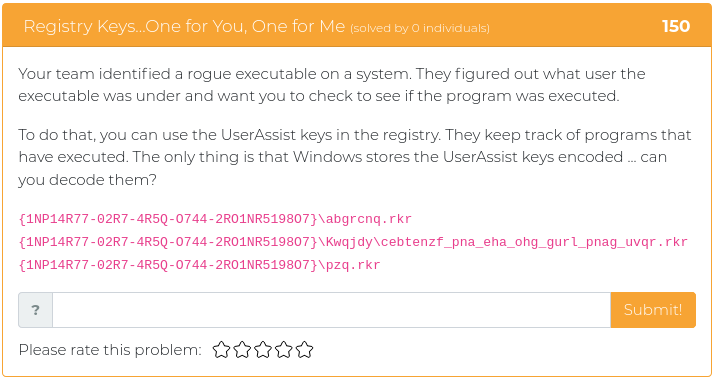
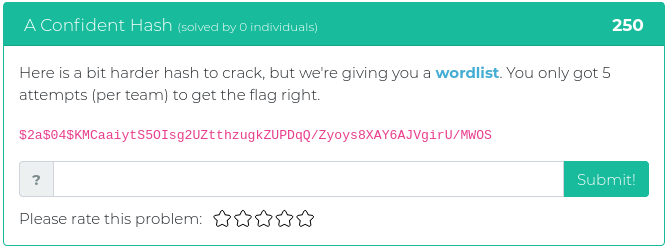
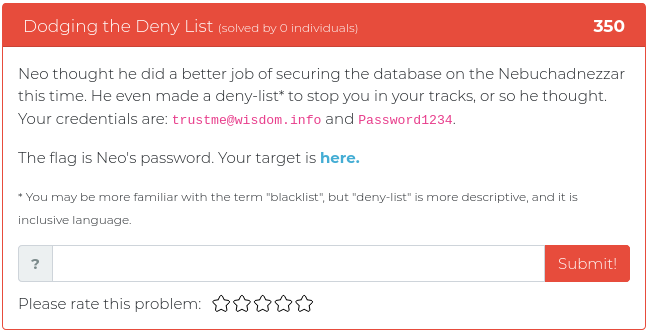
February 5, 2021
Howdy folks,
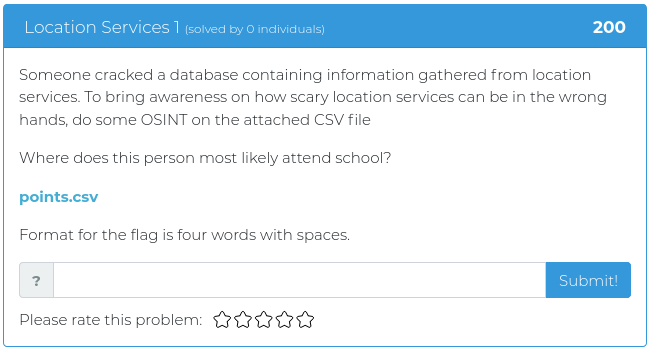
This week we are releasing five new Cyber Range problems to coincide with Kent Ickler and Jordan Drysdale’s Applied Purple Teaming training course, which started on February 2. We specifically picked problems that relate to some of the concepts and issues they cover, including the MITRE ATT&CK framework, PowerShell exploits, and enterprise OSINT awareness. You can find screenshots and descriptions of the new problems below.
These new problems are just the latest ones we’ve released. More are in development as this goes to press, so stay tuned for the challenges yet to come.
If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun:
https://www.blackhillsinfosec.com/services/cyber-range/
Good luck and have fun!
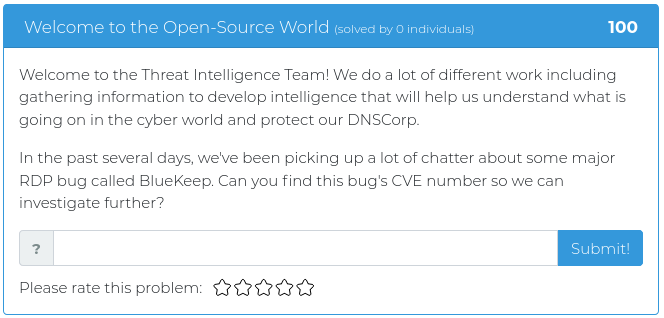
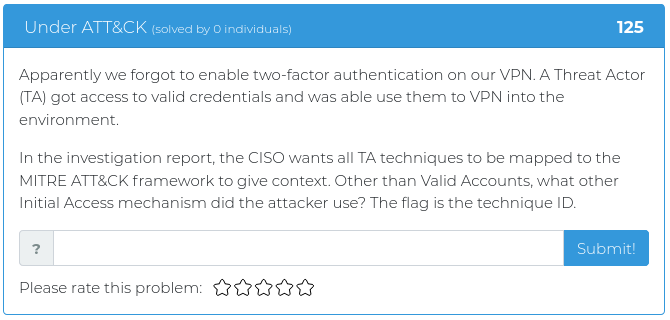
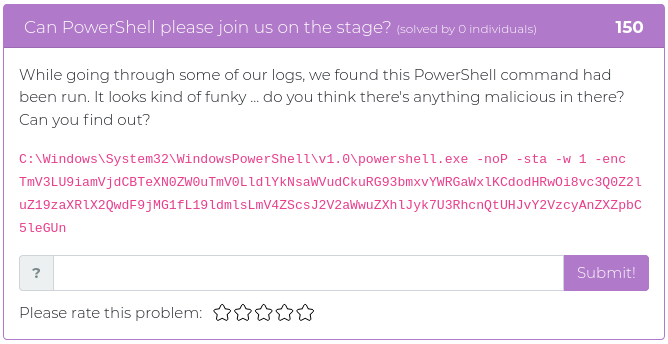
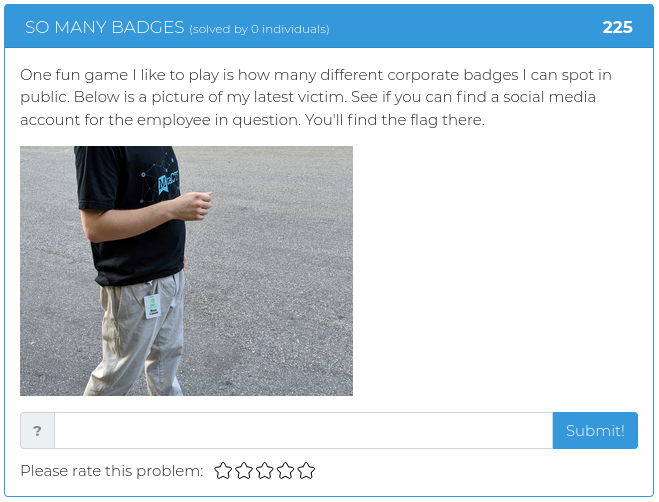
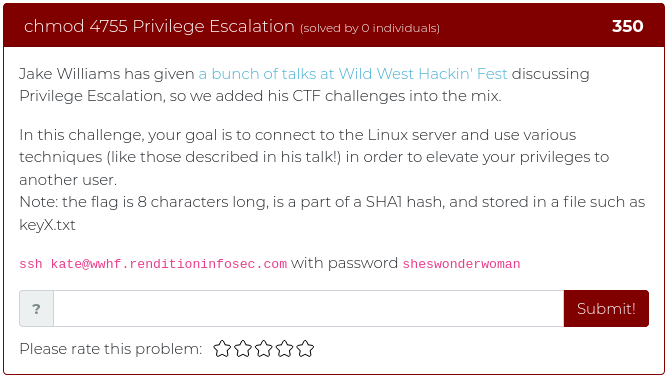
January 22, 2021
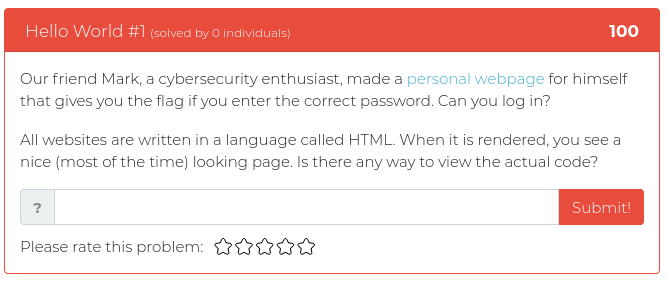
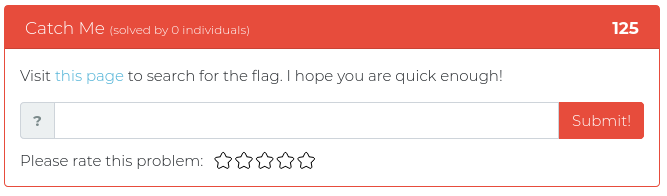
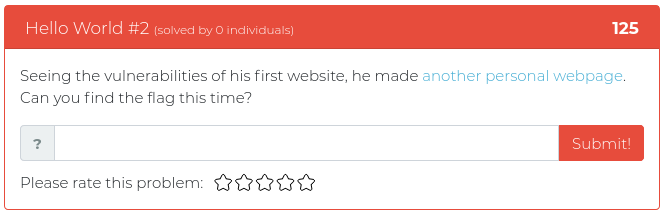
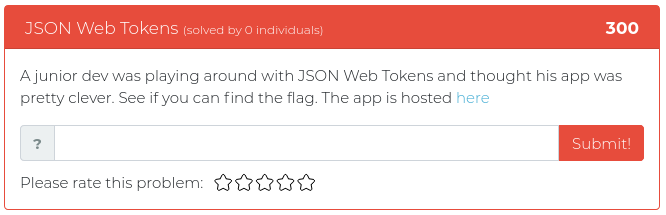
This week we are releasing five new Cyber Range problems to get you in the mood for BB King’s upcoming class all about Modern WebApp Pentesting. These new problems address a variety of common issues found in modern websites, from plaintext passwords hidden in source code to JSON web token abuse and fun with SQL injection. You can find screenshots of the new problems below.
If you’re not already signed up for the BHIS Antisyphon Cyber Range, the following page has screenshots, info, and, of course, a link where you can sign up and join in the fun: https://www.blackhillsinfosec.com/services/cyber-range/
For more info about BB’s class, Modern WebApp Pentesting, go here:
https://wildwesthackinfest.com/training/modern-webapp-pentesting/
Good luck and have fun!
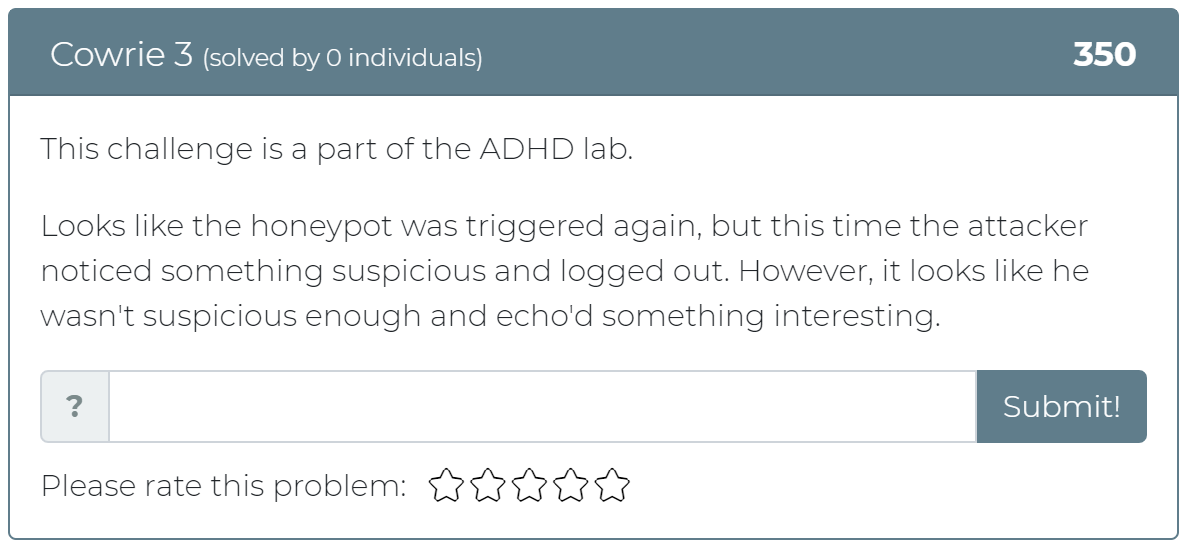
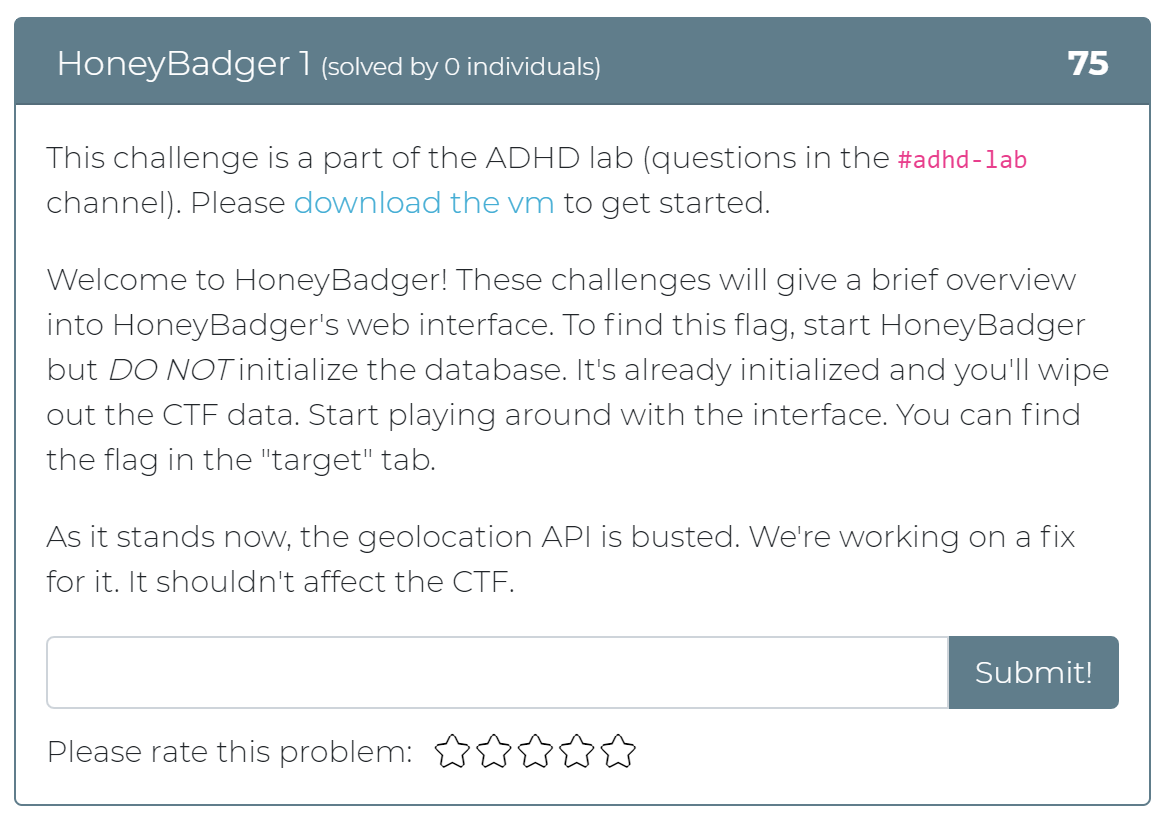
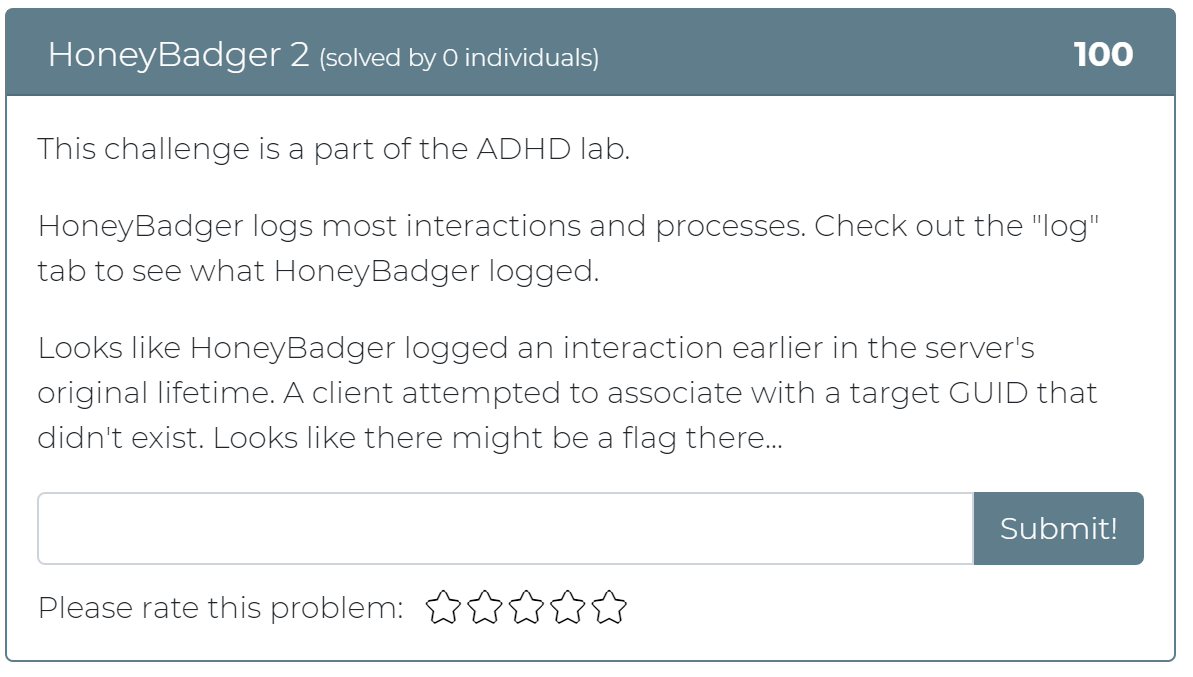
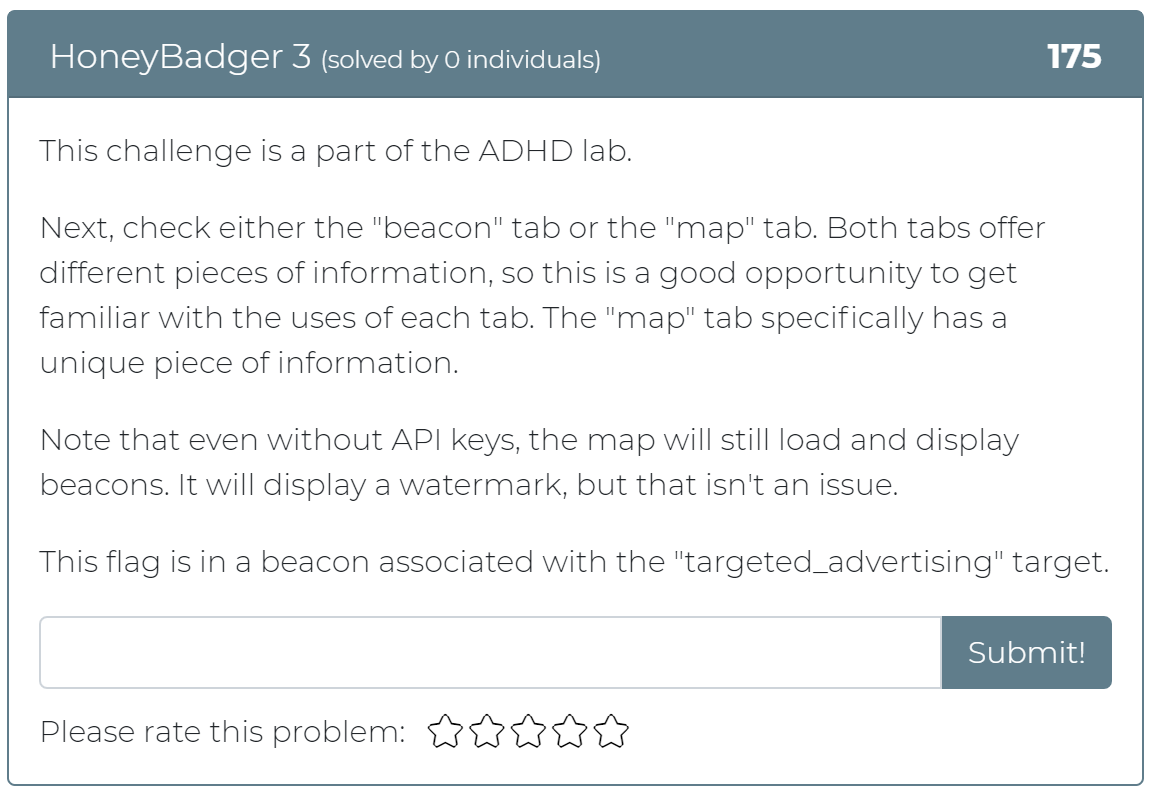
January 1, 2021
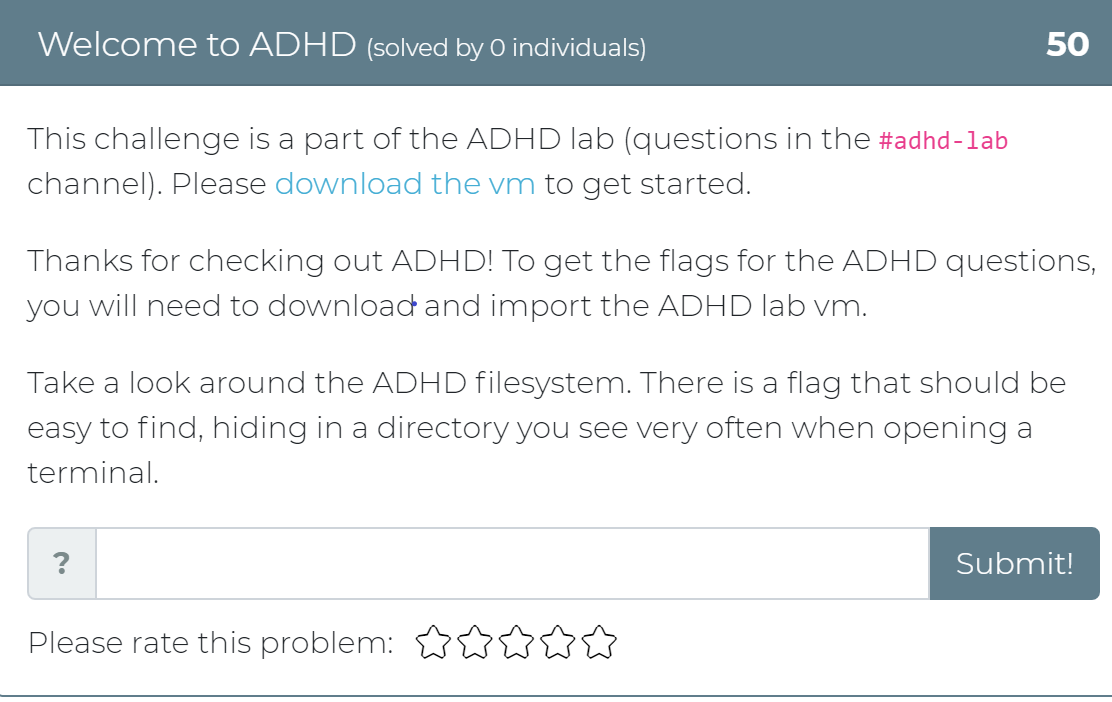
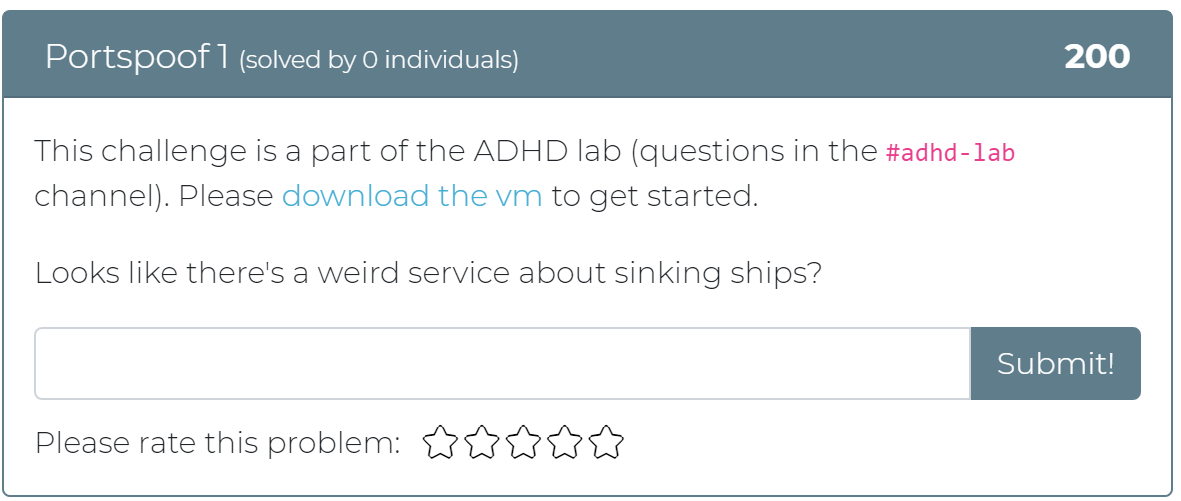
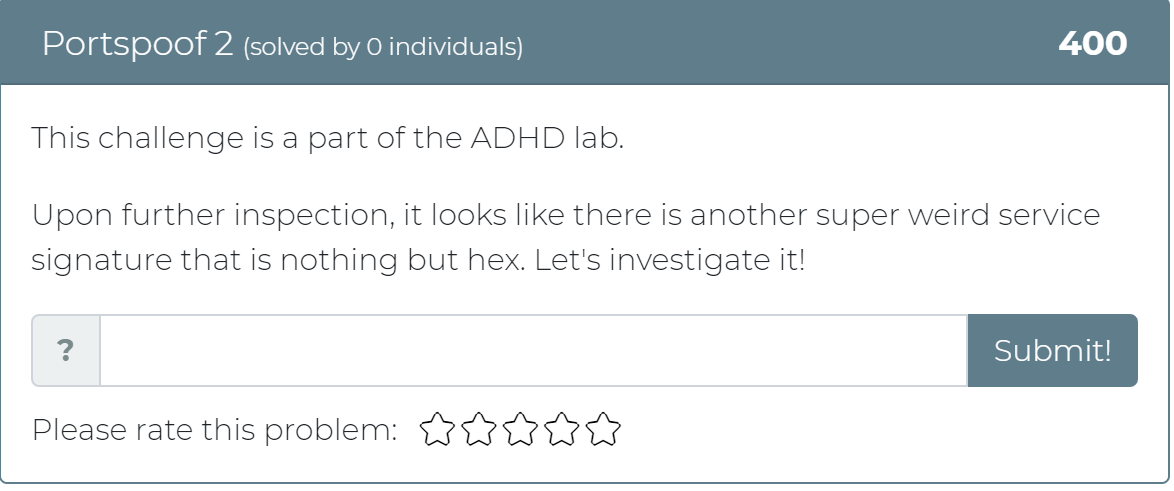
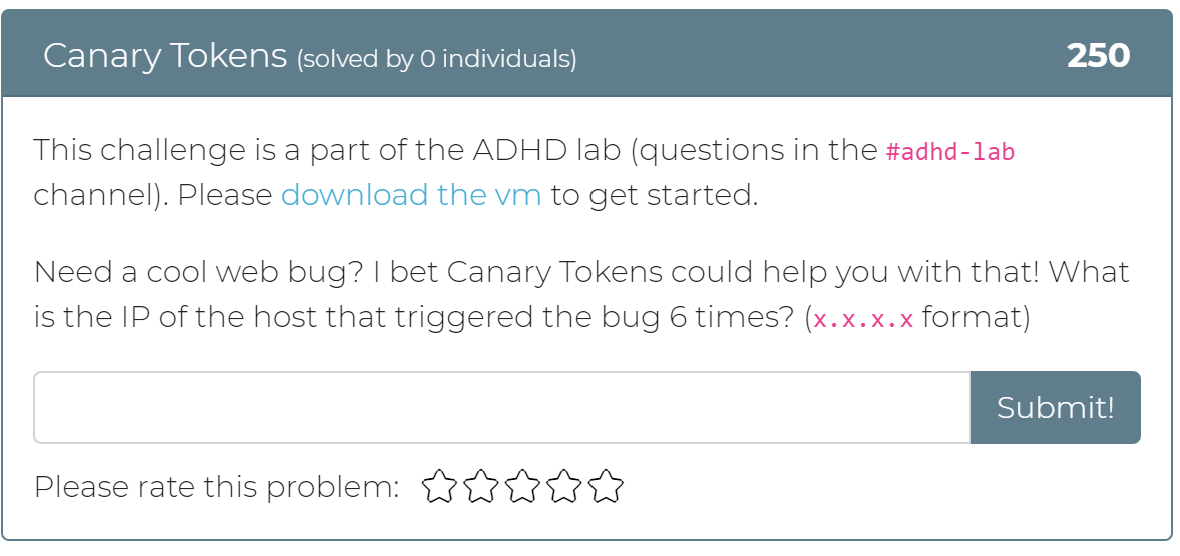
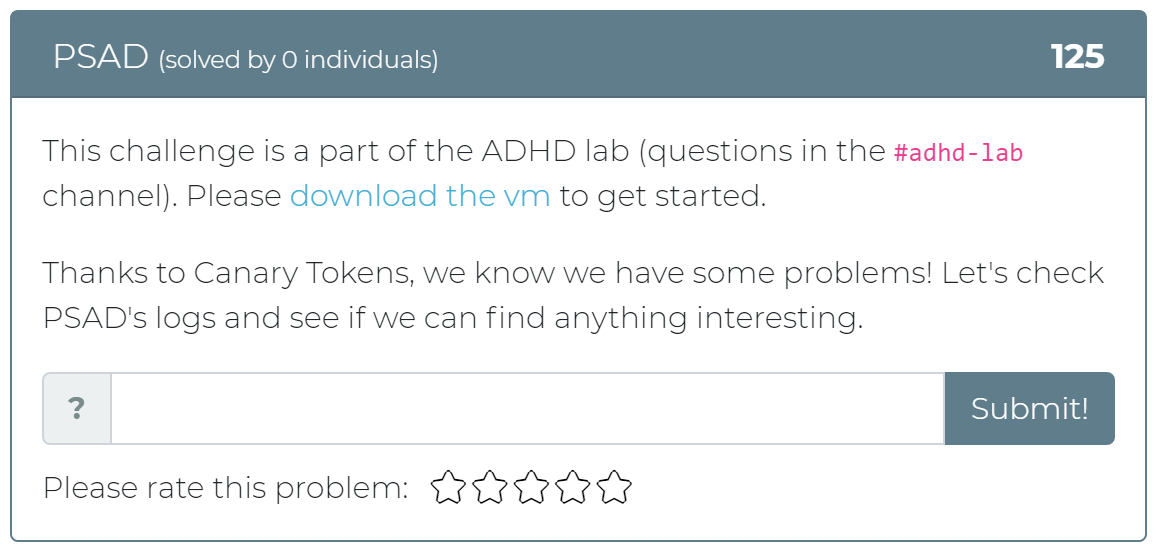
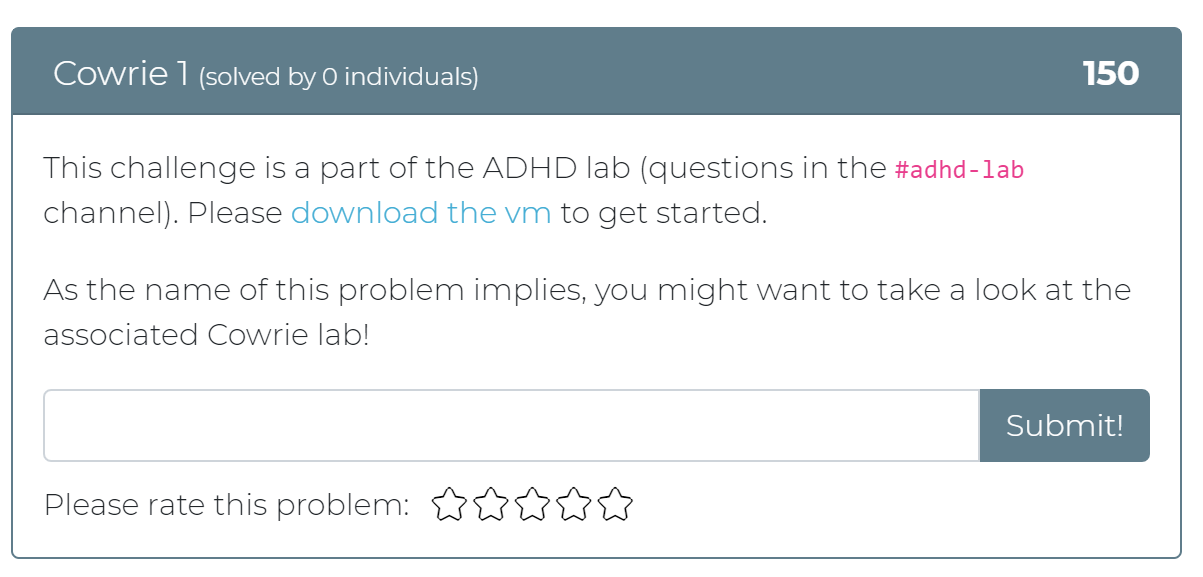
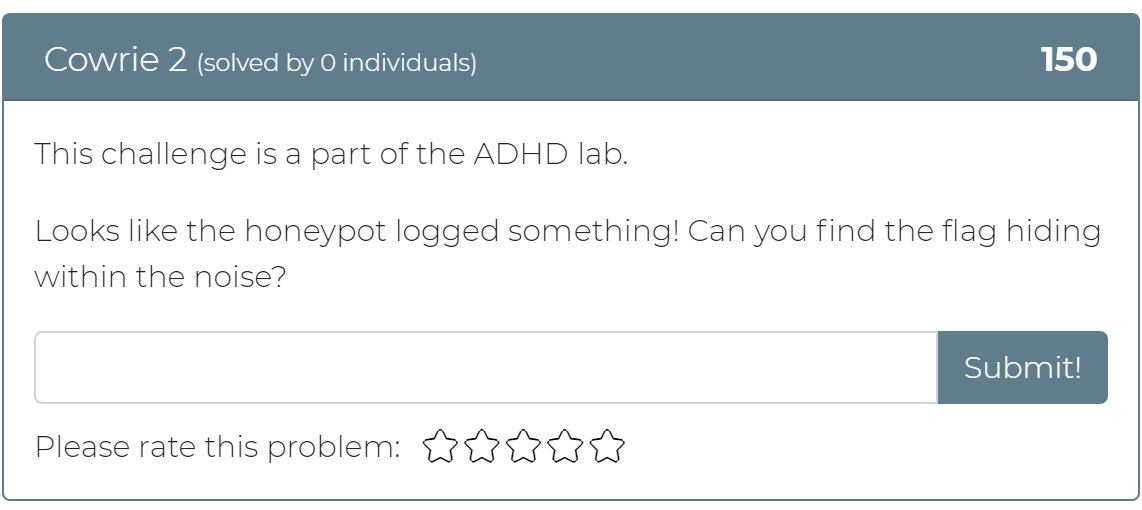
Today the Cyber Range team has released 12 new challenges! Whether you didn’t get a chance to play with Active Defense Harbinger Distribution (ADHD) at Wild West Hackin’ Fest (WWHF) or just want more exposure to the project, these challenges are for you. These challenges are a direct copy of the challenges provided in the WWHF lab, but we hope to add more as we build more labs.
To get started, check out the “Welcome to ADHD” challenge, which includes links to a relevant Black Hills Information Security (BHIS) blog post and the official ADHD documentation. If you have any questions or run into any issues, please feel free to mention @moth in the #adhd channel of BHIS’ Discord server here: https://discord.gg/TPNn833 You can check out some of the screenshots of the challenges below.
Good luck and have fun!
Have you heard about the Antisyphon ACE-T™ certification? When you log in to the Cyber Range and navigate to the Cyber Range Core event, you can see your ACE-T™ progress, challenges, rank, and percentile, which you can share with your boss or colleagues.
October 26, 2020
FIVE NEW PROBLEMS ADDED TO CYBER RANGE
Recently, the Cyber Range team added five new problems to the Cyber Range.
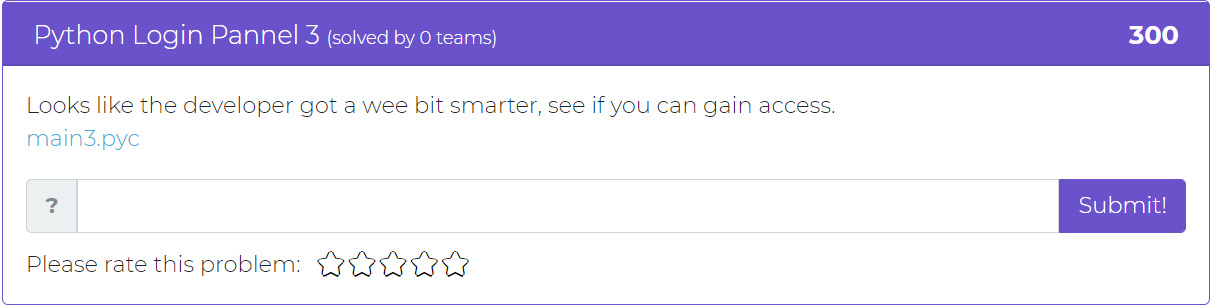
The first challenge addition is part 3 of the “Python Login Pannel” from the previous updates. In this challenge, the user is told that the web developer has gotten “smarter” and sets the challenge of gaining access once more.
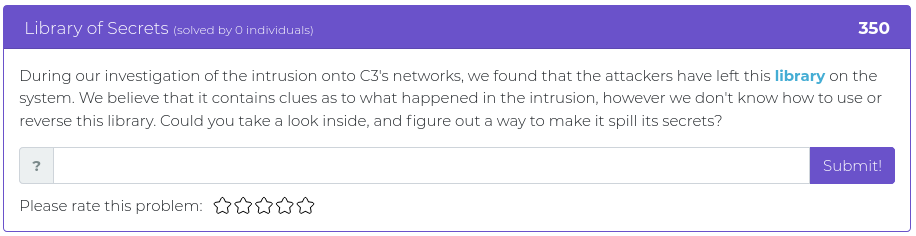
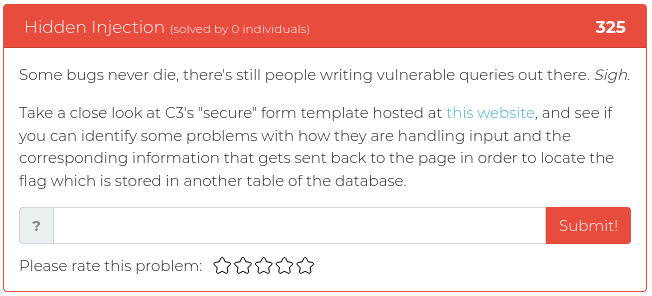
The next challenge to be added is titled “Ransomeware Attack Part 1” and it tasks the user with trying to find out who is behind an “attack” on C3’s system by finding where the intruder hosted their ransomware from and finding a flag in the process.
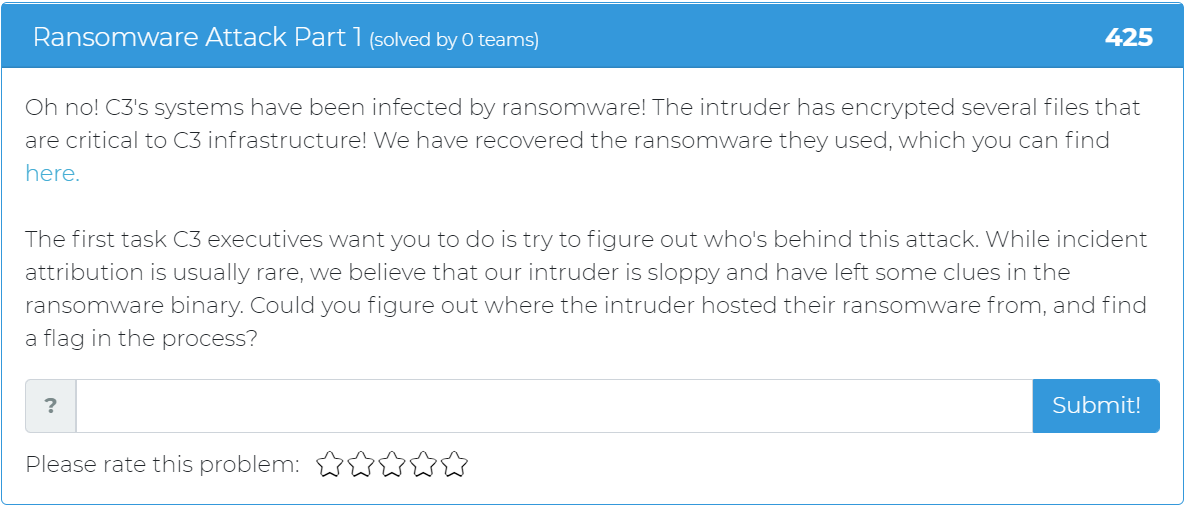
Tune in next week for part 2 of this challenge!
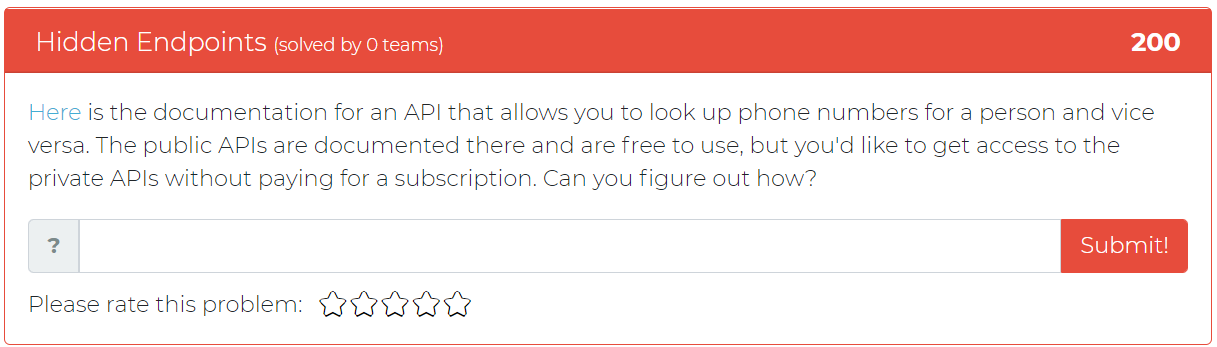
The third challenge addition tasks the user with trying to get access to private API’s without paying for a subscription using a documentation for an API that only gives public API’s.
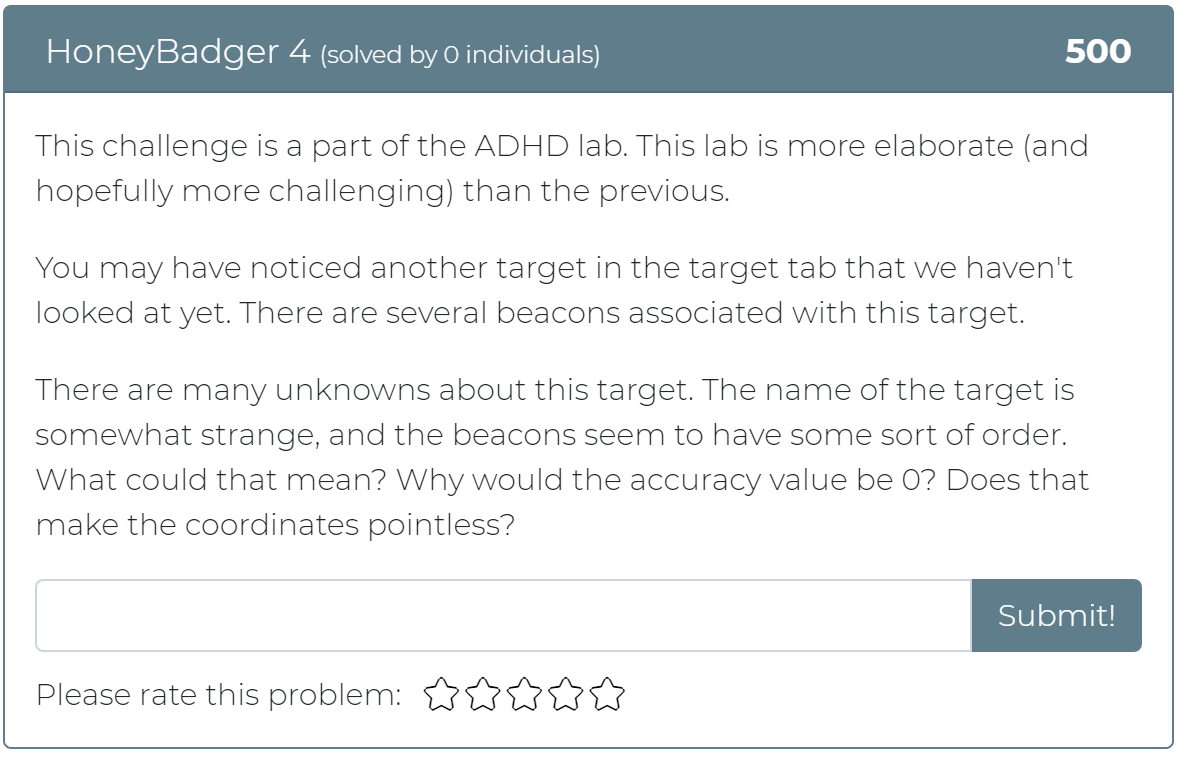
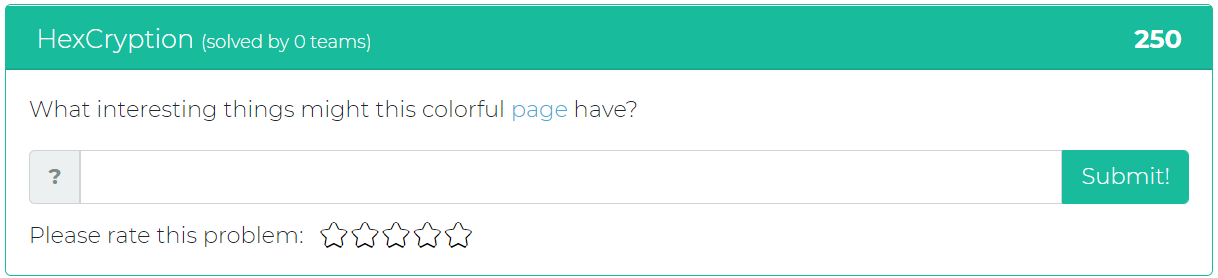
The fourth challenge asks the user to find “interesting things” within a “colorful” page in order to find the flag.
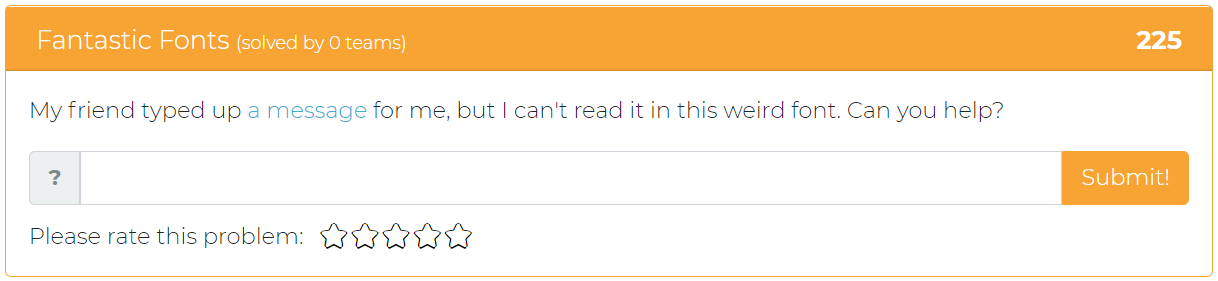
The fifth and final addition asks the user to help “read” a message that was typed up by a “friend” using a weird font.
Last but not least, the CyberRange team has created a challenge seeking the users feedback! The link to the “Feedback Survey” can also be found below!
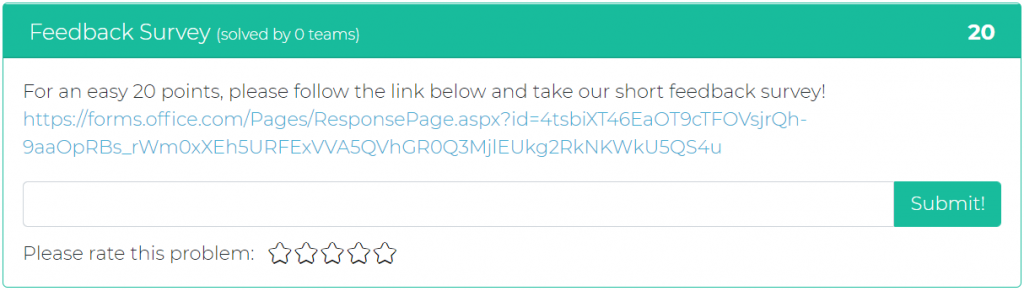
You can find the survey here:
https://forms.office.com/Pages/ResponsePage.aspx?id=4tsbiXT46EaOT9cTFOVsjrQh-9aaOpRBs_rWm0xXEh5URFExVVA5QVhGR0Q3MjlEUkg2RkNKWkU5QS4u
Please be sure to tune back in every two weeks for five new challenges!
For more info or to get started on the Cyber Range, please visit https://www.blackhillsinfosec.com/services/cyber-range/.
September 23, 2020
FIVE NEW PROBLEMS ADDED TO CYBER RANGE
Recently, the Cyber Range team added five new problems to the Cyber Range.
The first challenge addition is part 2 of the “Python Login Pannel” from the last update. In this challenge, the user is tasked with finding the correct password to another version of a secure login.
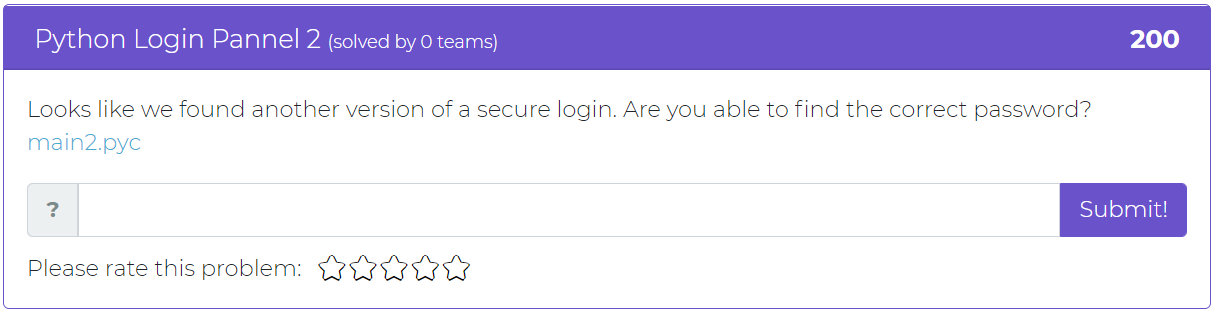
Tune in to the next update for the 3rd and final part of this challenge!
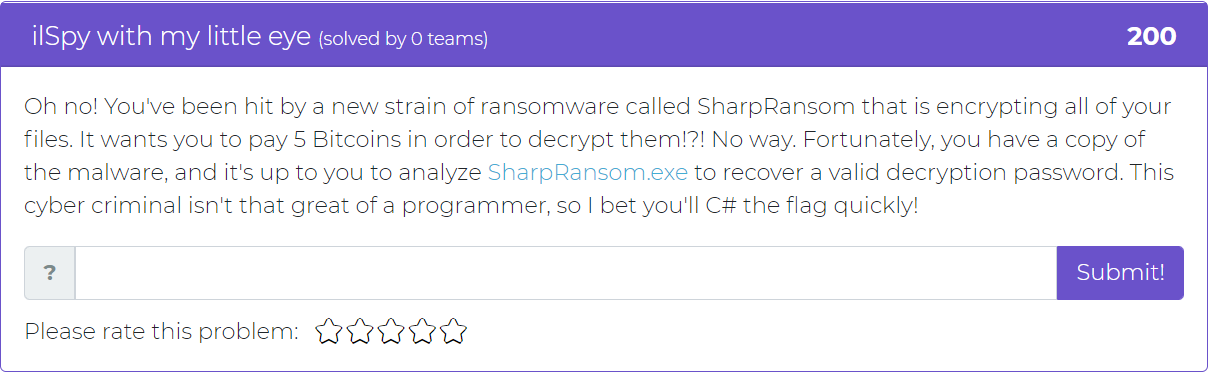
The next challenge to be added tasks the user with analyzing a copy of the “malware” to recover a valid decryption password.
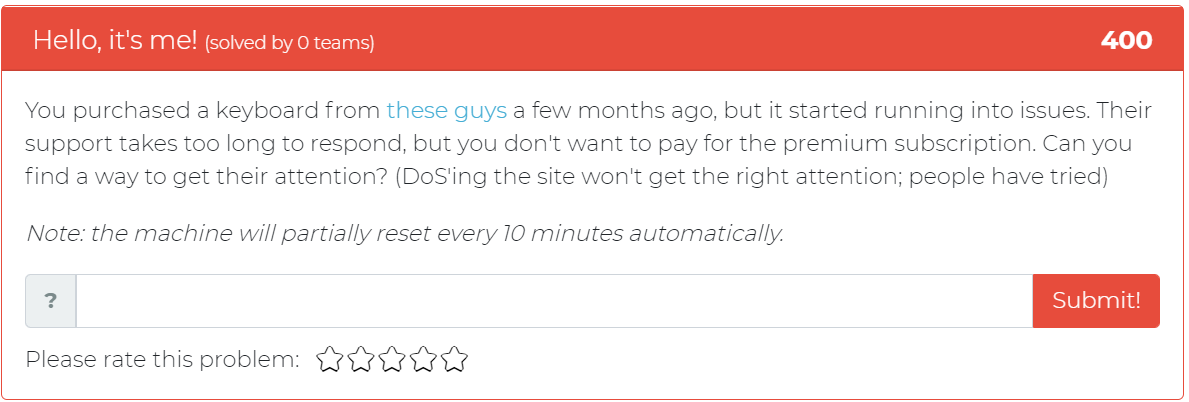
The third challenge addition tasks the user with trying to get the attention of the customer support of a company that a keyboard was purchased from.
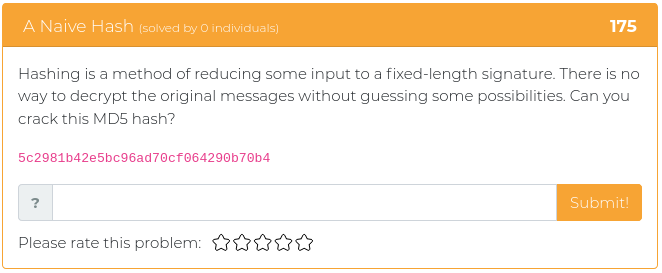
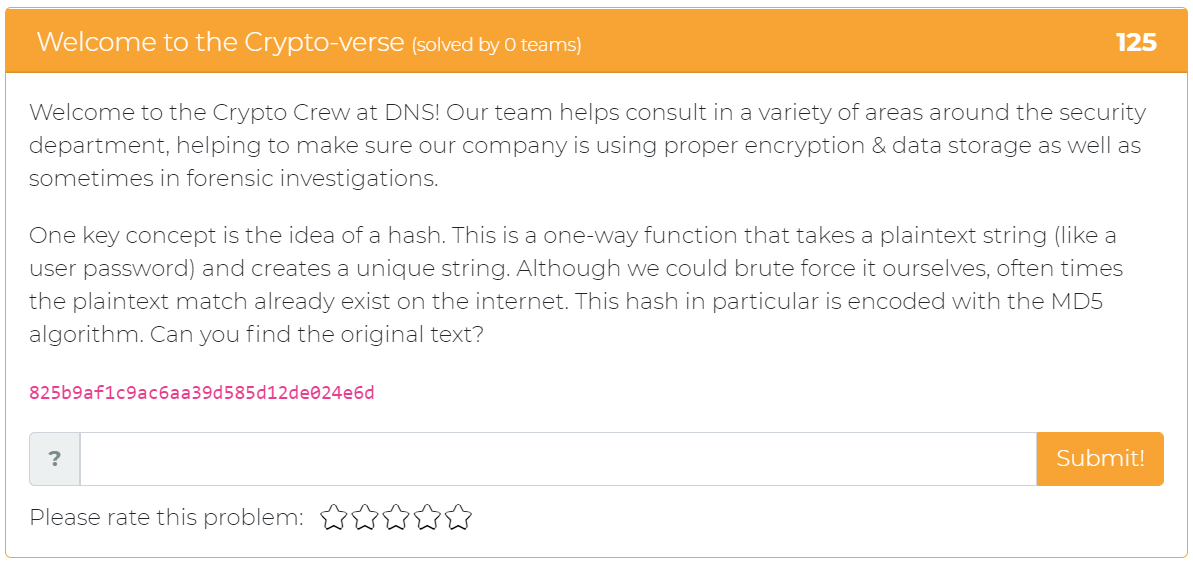
The fourth challenge asks the user to find the original text of a “hash”, which in this case is encoded with the MD5 algorithm.
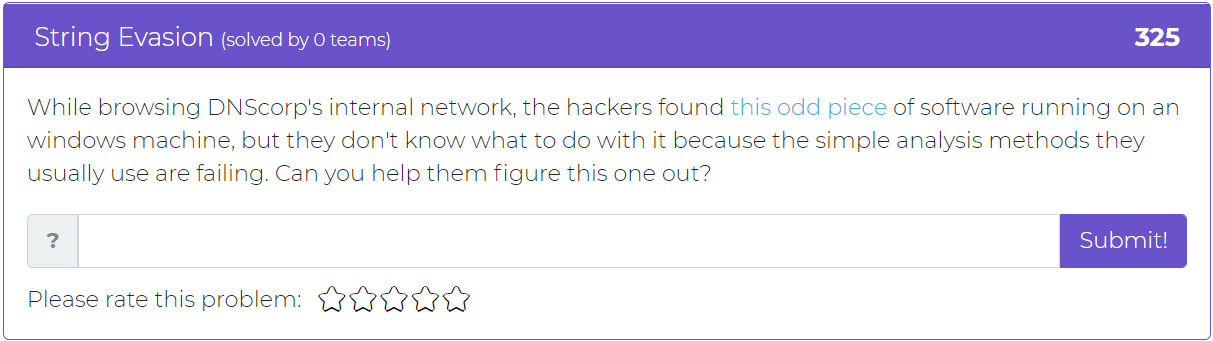
The fifth and final addition asks the user to help hackers figure out what to do with an “odd piece” of running software on an internal network.
Please be sure to tune back in every two weeks for five new challenges!
For more info or to get started on the Cyber Range, please visit https://www.blackhillsinfosec.com/services/cyber-range/.
September 3, 2020
FIVE NEW PROBLEMS ADDED TO CYBER RANGE
Recently, the Cyber Range team added five new problems to the Cyber Range.
The first challenge addition is the first of a 3-part challenge. “Python Login Pannel 1” gives the user some bytecode to a poorly programmed login portal and tasks them with finding the correct password.
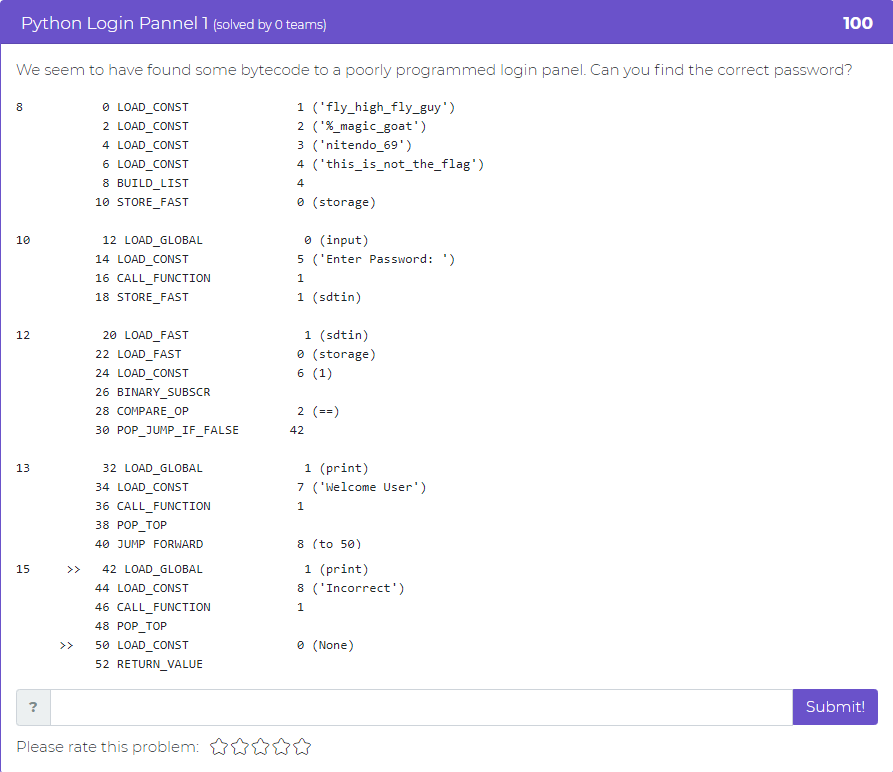
Tune in to the next update for part 2 of this challenge!
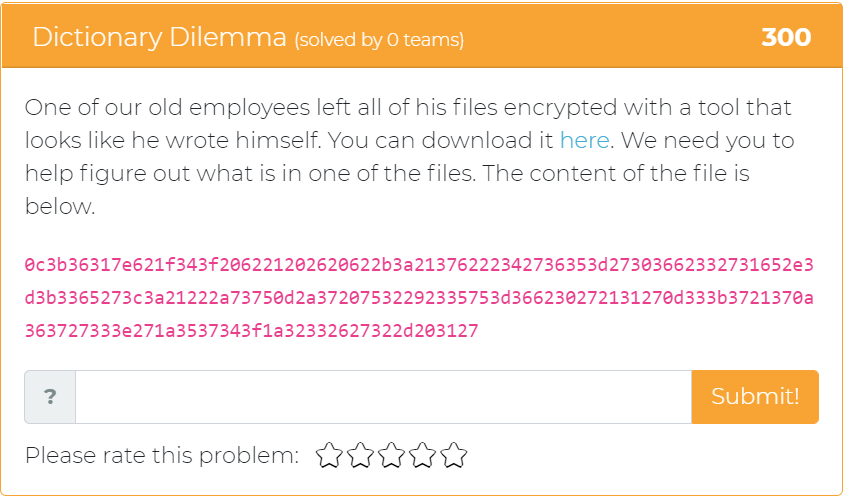
The next challenge to be added tasks the user with using cryptography skills to decrypt a file and find out what is in it.
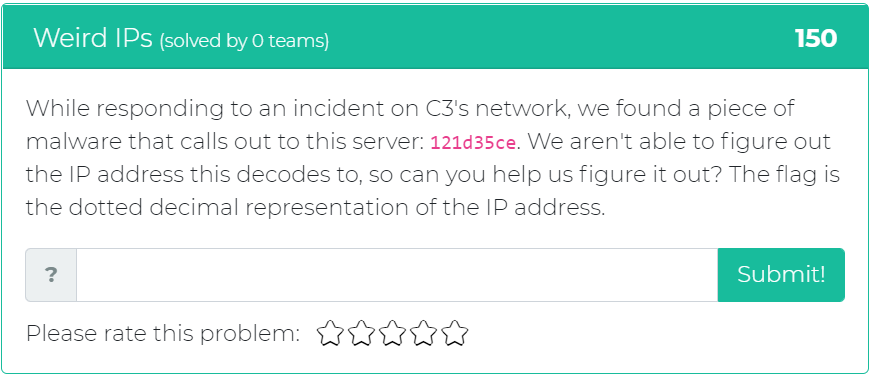
The third challenge addition asks the user to figure out what IP address that a piece of malware decodes to.
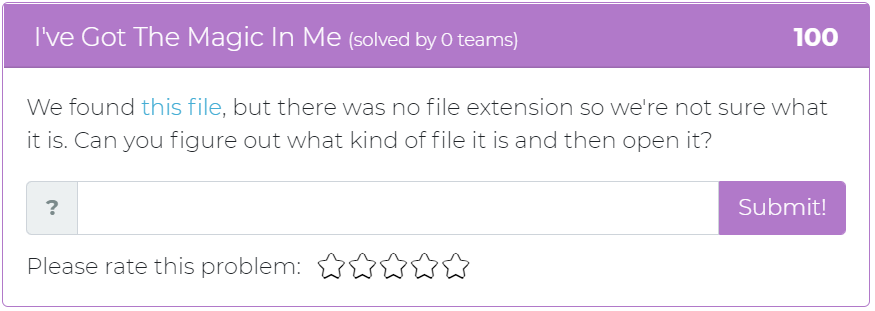
The fourth challenge asks the user to look at a file, find out what kind of file it is, and then open it.
The fifth and final addition asks the user to find a bypass to “unmotivated” security protections on a given website.
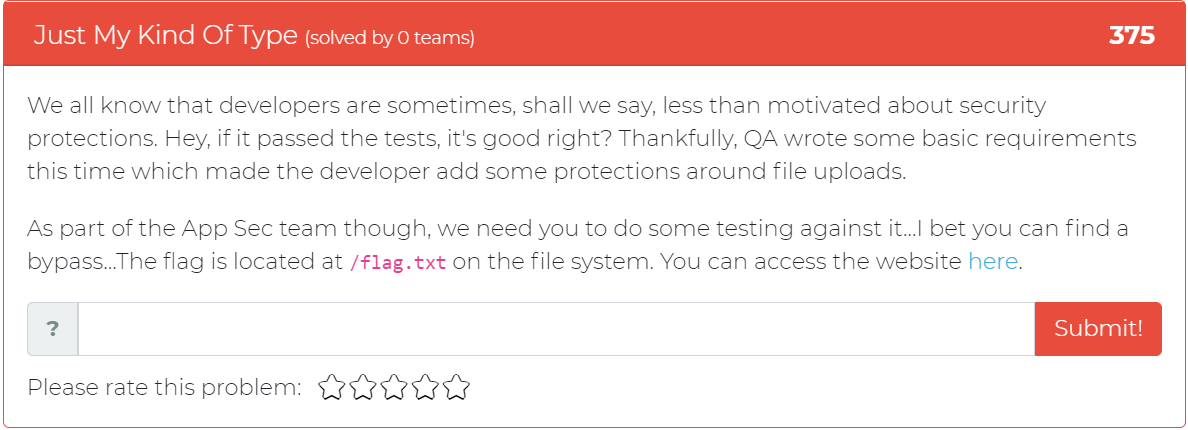
Please be sure to tune back in every two weeks for five new challenges!
For more info or to get started on the Cyber Range, please visit https://www.blackhillsinfosec.com/services/cyber-range/.
August 4, 2020
FIVE NEW PROBLEMS ADDED TO CYBER RANGE
Recently, the Cyber Range team added five new problems to the Cyber Range.
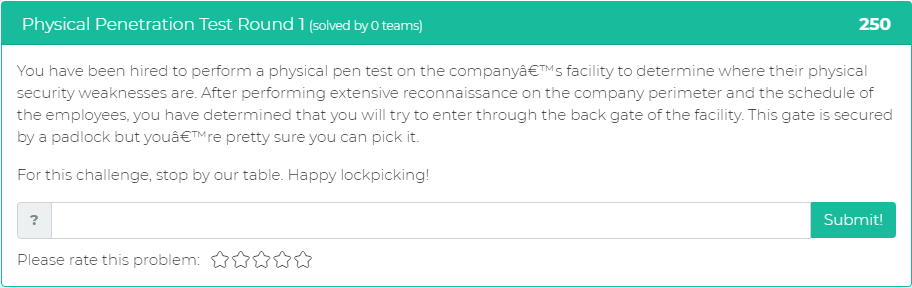
The first problem puts the user in the scenario of performing a physical penetration test where you have to pick a lock on an entrance to a facility:
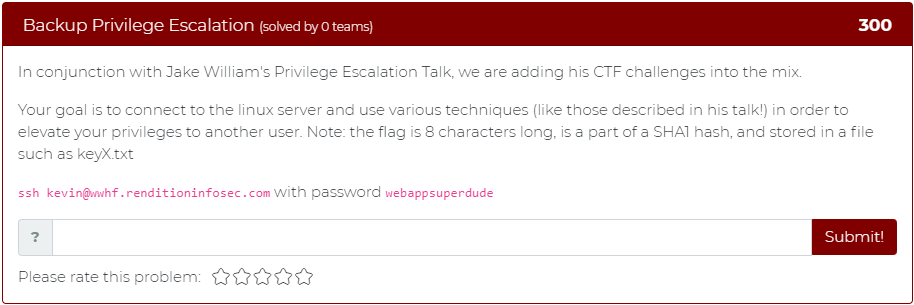
The second problem tasks the user with connecting to a linux server and utilizing various techniques to elevate privileges to another user:
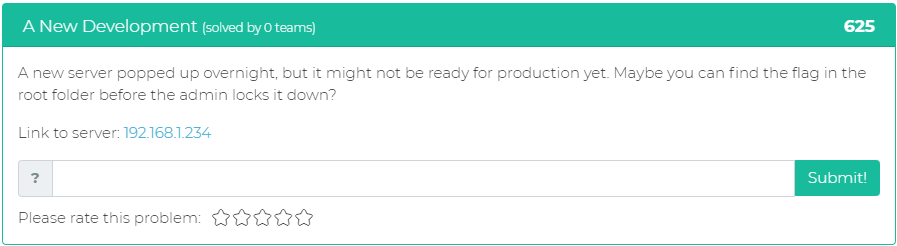
The third problem gives a task to find the flag in the root folder of a server using the link provided:
The fourth problem relates to cryptography and asks the user to decrypt the given message in order to find the flag:
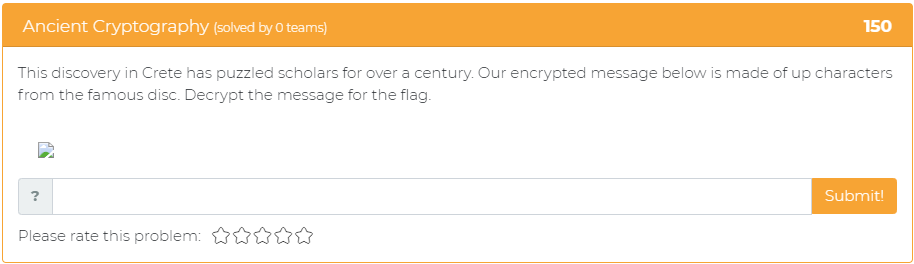
The fifth and final problem tasks the user with finding the name of the type of encoding and then recovering the flag by scanning it:
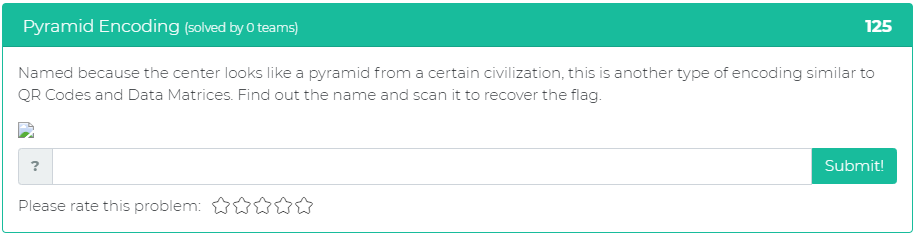
Please be sure to tune back in every two weeks for five new challenges!
For more info or to get started on the Cyber Range, please visit https://www.blackhillsinfosec.com/services/cyber-range/.
July 20, 2020
Five New Problems Added to Cyber Range
Recently, the Cyber Range team added five new problems to the Cyber Range.
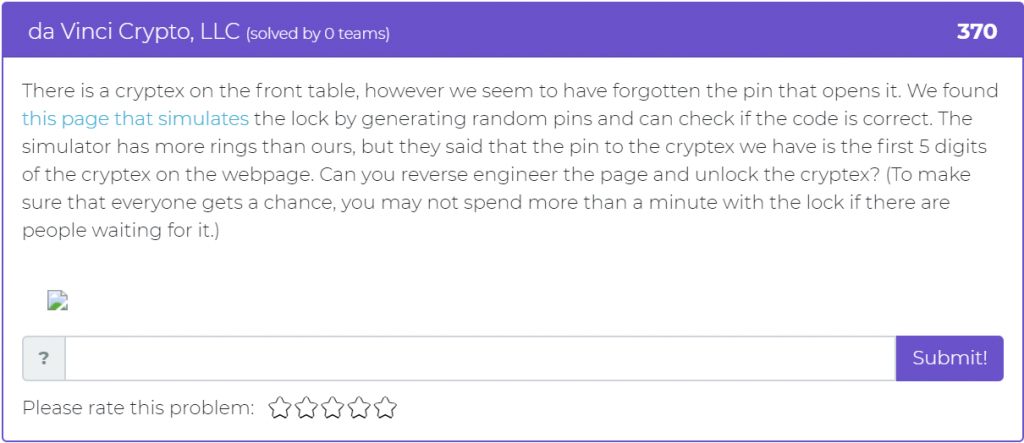
The first problem involves using da Vinci Crypto to reverse engineer a page to unlock a cryptex:
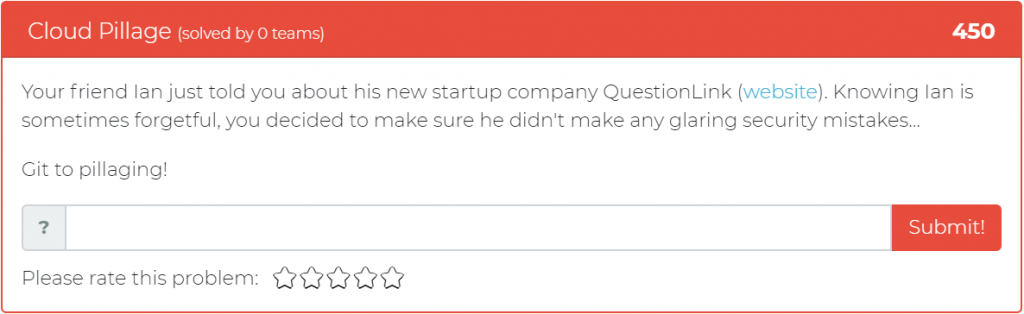
The second problem deals with web exploitation and focuses on finding glaring security mistakes on a website:
The third problem gives a link to a site full of binary where the user is supposed to find the flag:
The fourth problem relates to forensics and asks the user to analyze a “flash drive” to search for anything of interest:
The fifth and final problem concerns penetration testing and challenges the user to connect to a Linux server and elevate privileges to another user:
Please be sure to tune back in every two weeks for five new challenges!
For more info or to get started on the Cyber Range, please visit https://www.blackhillsinfosec.com/services/cyber-range/