Backdoors & Breaches
Backdoors & Breaches is the original cooperative incident response card game from
Black Hills Information Security and Active Countermeasures.
The Core Deck contains 52 unique cards that help teams run realistic tabletop exercises, explore attack paths, and practice incident response skills—while having fun.
If you’d like to schedule a demo for your team, reach out to Deb Wigley below!
Turn Incident Response Into a Game
Backdoors & Breaches takes traditional tabletop exercises and turns them into a structured, cooperative card game.
An Incident Captain crafts a scenario using hidden Attack cards, while Defenders work together—using Detections, dice, and critical thinking—to uncover what happened before it’s too late.
- Train IR and blue teams on realistic attack paths
- Run tabletop exercises with a clear, repeatable framework
- Introduce students and new analysts to incident response
- Encourage discussion about detection coverage, tools, and playbooks

What’s Included
📦 52 Core Deck Cards
Every Core Deck includes 52 cards representing Attacks, Detections, and Injects. Each card features a title, description, detection ideas, tools, and resources so the learning continues long after the game ends.
🎯 Four Attack Categories
Attacks are broken into four categories—Initial Compromise, Pivot & Escalate, Persistence, and C2 & Exfil. Combining one card from each category gives you thousands of unique incident scenarios.
📘 Visual Guide & Turn Tracker
The downloadable Visual Guide walks you through setup and gameplay step-by-step, and the printable Turn Tracker helps you record turns, rolls, and key findings during each exercise.
How the Game Works
Four simple steps. Cooperative incident response practice.
1️⃣ Build the Incident
The Incident Captain secretly selects one Attack card from each category (Initial Compromise, Pivot & Escalate, Persistence, and C2 & Exfil) to create a four-step attack path.
2️⃣ Set Up the Table
Separate the deck into Attacks, Procedures, and Injects. Deal out rows of Procedure cards—some as “Established Procedures” with a roll bonus, and others as backup options when you need them.
3️⃣ Investigate & Roll
On each turn, Defenders choose a Procedure, discuss what they’re looking for, and roll a d20. Successful rolls can reveal Attack cards; failures advance the turn counter and can trigger Injects that change the scenario.
4️⃣ Win (or Lose) as a Team
The game is fully cooperative: you win or lose together. Reveal all four Attack cards within 10 turns to win; if time runs out, use the debrief to talk about gaps, tooling, and real-world improvements.
More of a visual learner?
Check out this video showing gameplay in action!
Deck Preview
Here’s a closer look at some of the cards and the original playmat you can use for in-person or virtual games.
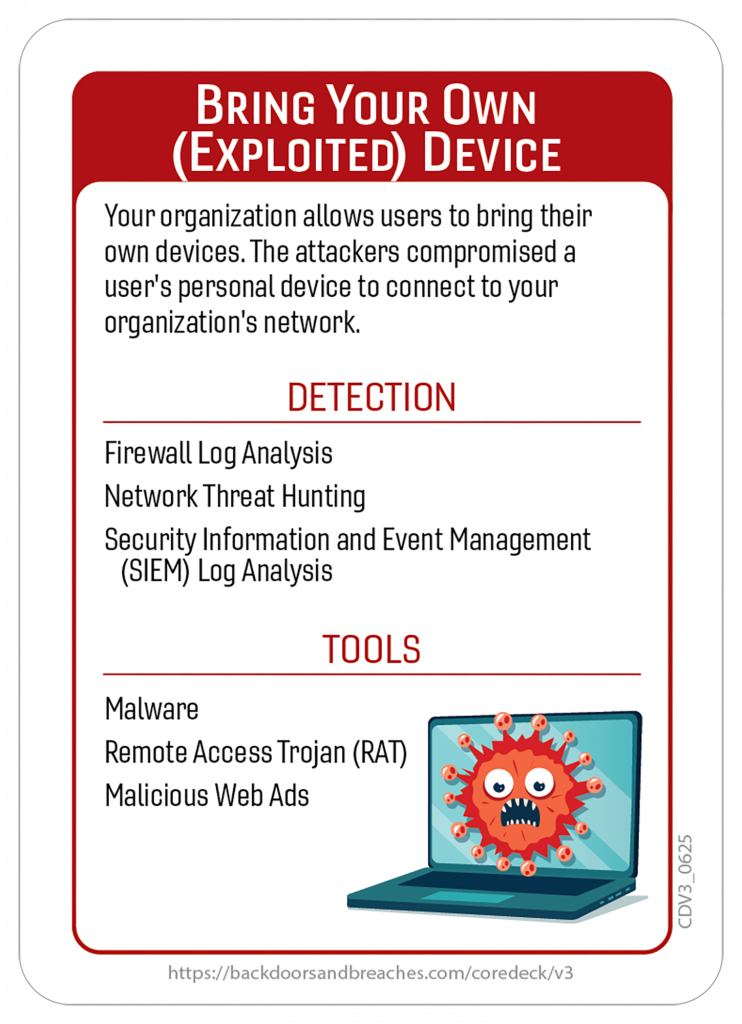
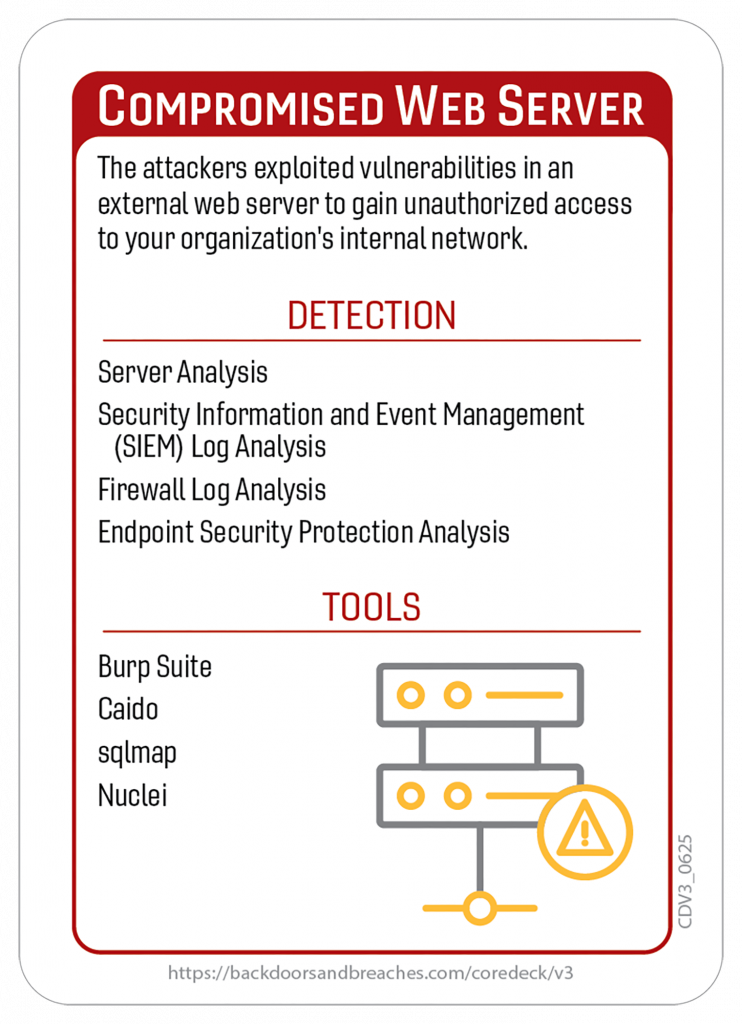

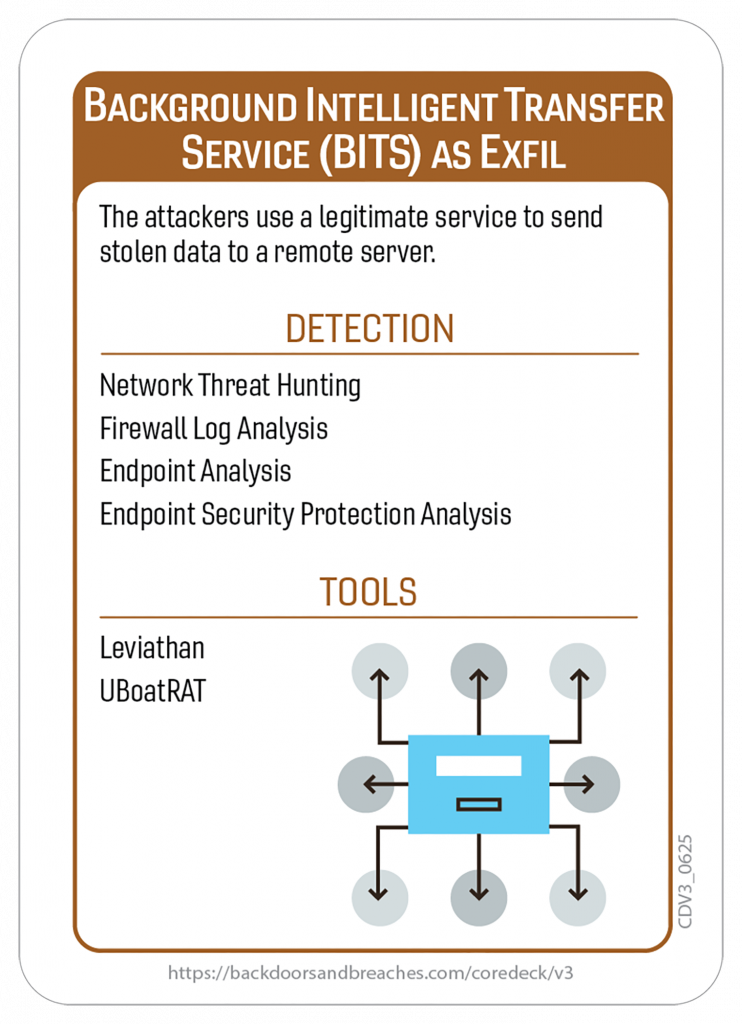
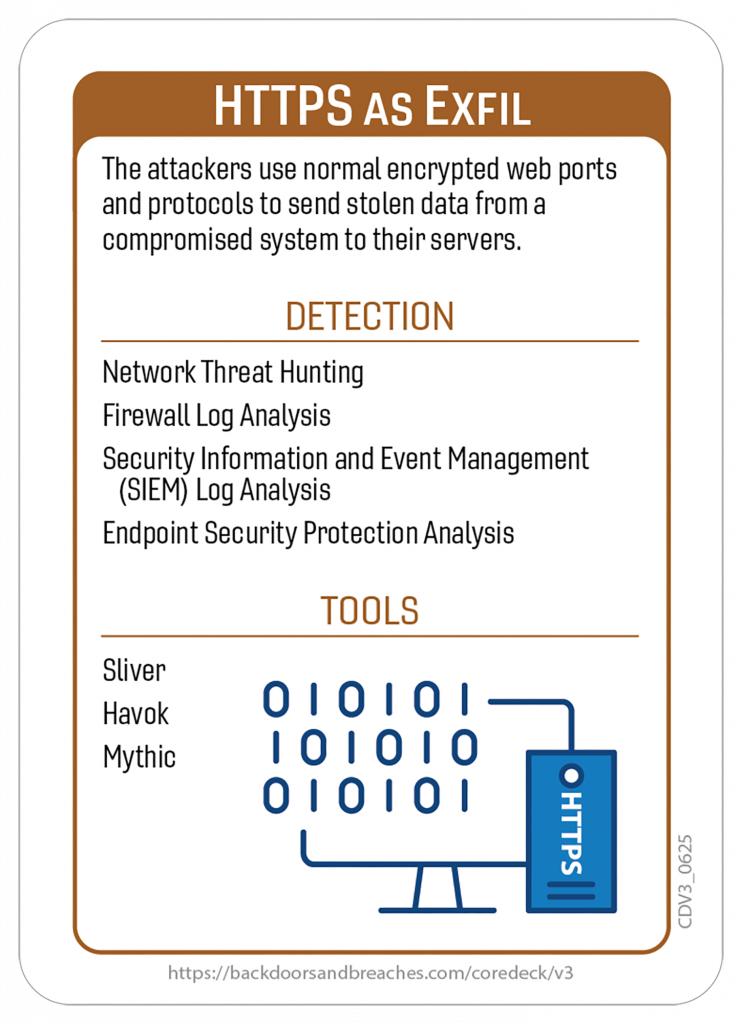
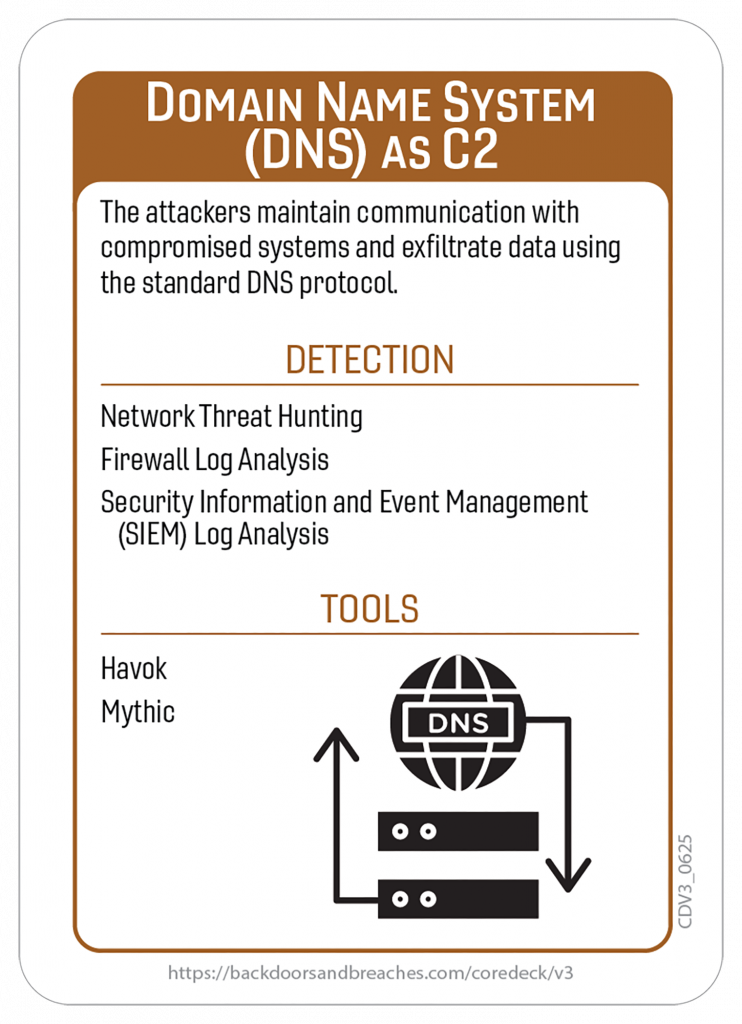
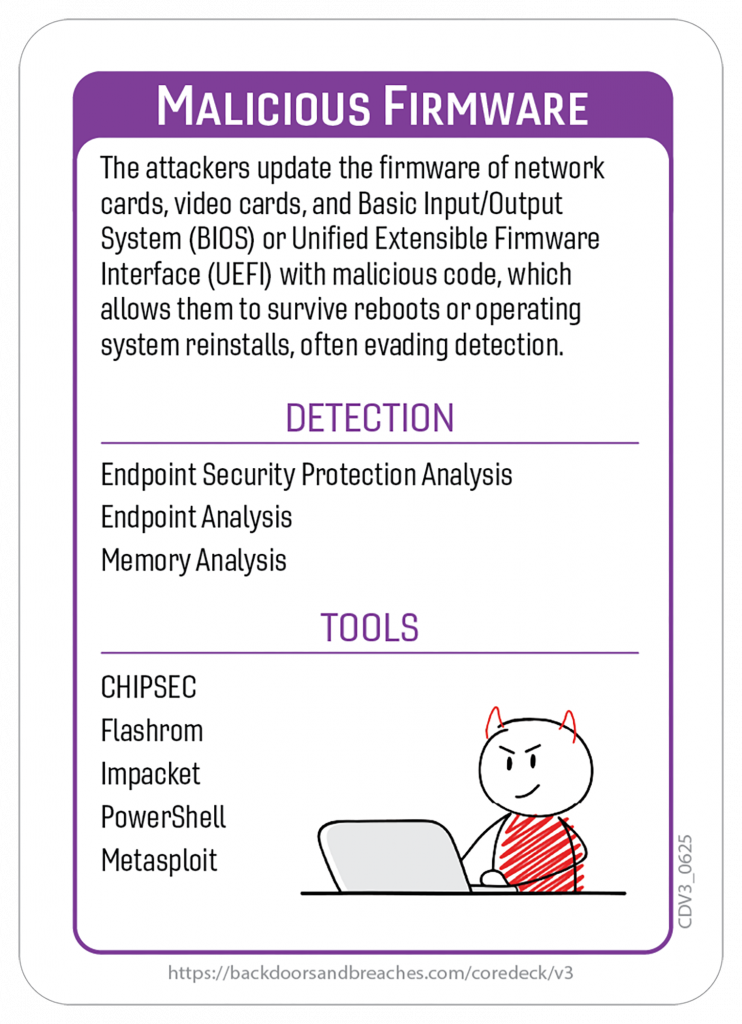
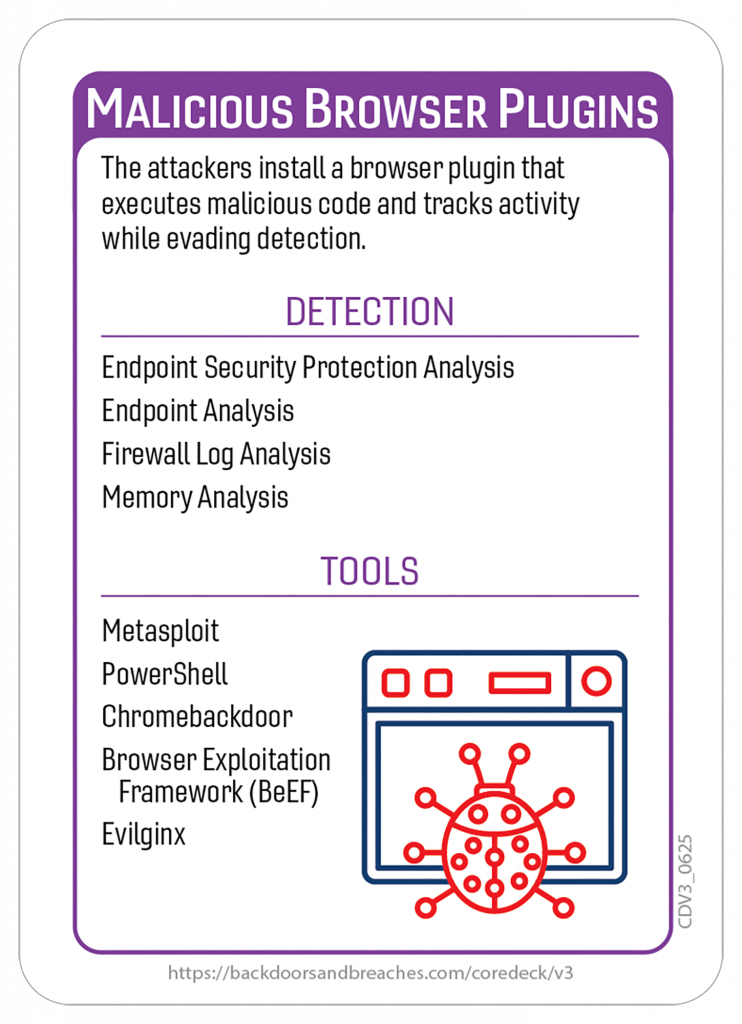

Download the Rulebook
Everything you need to run Backdoors & Breaches at your organization, classroom, or event is in the Visual Guide.
Using Backdoors & Breaches at Your Event
Backdoors & Breaches works well for security meetups, conferences, cyber clubs, and internal trainings.
Use it as a standalone exercise or pair it with talks, workshops, or live demos.
- Run 30–60 minute game sessions for lunch-and-learns or drills
- Use real logs, SIEM queries, and EDR data alongside gameplay
- Capture findings and action items with the Turn Tracker
- End each session with a debrief focused on your environment
Want BHIS to run a Backdoors & Breaches session for your team or event?
Community!
Play online and connect with the community:
References & Resources
Explore card references, tools, & detections:
Frequently Asked Questions
Do I need anything besides the Core Deck?
You’ll need a Backdoors & Breaches Core Deck, a d20 (or dice app), and at least two players.
The ideal group size is 5–7 Defenders plus one Incident Captain. Expansion decks are optional but add new cards and variety.
Is Backdoors & Breaches used for real training?
Yes. Backdoors & Breaches is used by high school and university cyber clubs, security consultants, enterprises, and government teams around the world to practice incident response and identify gaps in detection and process.
Where can I find references for tools and detections?
Use the Core Deck and expansion reference pages to see suggested tools, detections, and BHIS blog posts mapped to each card:
How do I get help running a session?
We’re happy to help facilitate Backdoors & Breaches sessions and workshops.