WEBCAST: Attack Tactics Part 1
John Strand // John is starting a new series of webcasts called Attack Tactics. This first part is a step-by-step walk-through of an attack BHIS launched against a customer, with […]

John Strand // John is starting a new series of webcasts called Attack Tactics. This first part is a step-by-step walk-through of an attack BHIS launched against a customer, with […]

Bre Schumacher// Many of you were probably asked as a young child what you wanted to be when you grew up. Maybe you had an idea of something that sounded […]

Kent Ickler and Derrick Rauch* // Sun Protection Factor Err… wait a second. Sender Policy Framework Ladies and Gentlemen of the class of 1997, Wear Sunscreen…I will dispense my advice, […]

David Fletcher// The weak password policy finding is typically an indicator of one of two conditions during a test: A password could be easily guessed using standard authentication mechanisms. A […]

Paul Clark* // What is Software Defined Radio and why should you, the noble InfoSec professional, care about it? What kind of hardware and software do you need to start […]
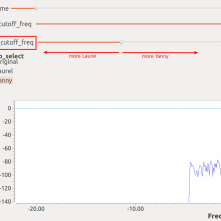
Paul Clark* // Feeling uncomfortably productive today? I’ve got a remedy for that, involving internet memes and signal processing. Come and waste a few minutes of your day with Laurel, […]

Darin Roberts// If you have been in the security field for any length of time at all you have heard the term C2. You might have heard it also called […]

Rick Wisser// Comparing Apples to Oranges (Bus Pirate vs Shikra) this a Hardware Hacking 101 webcast follow up blog post. I recently did a hardware hacking webcast on hacking a router […]

Kent Ickler// TLDR: We use a custom dictionary to crack Microsoft Office document encryption. Then we use a custom dictionary for pwnage in LinkedIn hash database. Background: I recently got […]