Small and Medium Business Security Strategies: Part 2
Jordan Drysdale // A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]

Jordan Drysdale // A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]

John Strand // Lately we’ve been running a very cool game with a few of our customers. There’s been some demand for incident response table top exercises. For the […]

Jordan Drysdale// Blurb: A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]

Jordan Drysdale// Physical Pentest Upcoming? Bring a Badgy. While badge reproduction may not be the intended use of this product, if you are a physical tester and you don’t own […]

Brian Fehrman // Privilege escalation is a common goal for threat actors after they have compromised a system. Having elevated permissions can allow for tasks such as: extracting local password-hashes, […]

Joff Thyer // If you have been penetration testing a while, you likely have ended up in a Red Team situation or will be engaged in it soon enough. From […]

John Strand// In this webcast John talks about the new ACDC law and what it means exactly. There has been quite a bit of anger and great GIFs about hacking […]
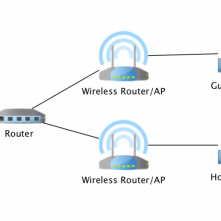
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]
John Strand // I wanted to take a few moments and address the “Hacking Back” law that is working people up. There is a tremendously well-founded fear that this law […]