WEBCAST: Log File Frequency Analysis with Python
Joff Thyer // Information Security professionals often have reason to analyze logs. Whether Red Team or Blue Team, there are countless times that you find yourself using “grep”, “tail”, “cut”, […]
Joff Thyer // Information Security professionals often have reason to analyze logs. Whether Red Team or Blue Team, there are countless times that you find yourself using “grep”, “tail”, “cut”, […]

Jordan Drysdale & Kent Ickler // Jordan and Kent demonstrate why there is only ONE correct way to configure your wireless networks. They also talk about the use of a […]

John Strand // In this webcast, we walk through different tools to establish and test your Command and Control (C2) detection capabilities. Why does this matter? Almost all organizations we […]

John Strand // It’s odd, we try to push security forward through standards like NIST, the Critical Controls, and PCI, but most organizations strive to meet the bare minimum required […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]
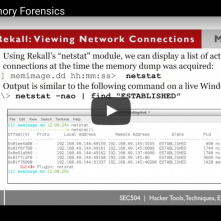
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]

John Strand // So you think you might have a compromised Windows system. If you do, where do you start? How would you review the memory of that system? What […]
John Strand with BHIS testers // Yes, we did this in 2017, but it’s reflecting work done in 2016.
Check out Carrie’s demo of her DPAT, and if you missed her blog, check that out here.