PNPT: Certification Review

What is the PNPT?
The Practical Network Penetration Tester (PNPT), created by TCM Security (TCMS), is a 5-day ethical hacking certification exam that assesses a pentester’s ability to perform an external and internal network penetration test. To complete the exam, pentesters must:
- Perform reconnaissance to gather intelligence
- Leverage common web server vulnerabilities to breach the perimeter
- Leverage Active Directory (AD) vulnerabilities to move laterally and vertically within the network
- Compromise the Domain Controller (DC)
- Produce a professionally written pentest report
- Deliver a live report debrief to TCMS assessors
PNPT Exam Preparation & Tips
The PNPT exam follows a series of training courses developed by TCMS and covers a range of methodologies and topics. A complete syllabus and exam overview is available on the TCMS website. Below are a few exam preparation tips and suggestions.
As expected, tools pivotal to completing the exam include Nmap, Burp Suite, Nessus, Metasploit, Impacket scripts, hash crackers, and other software built into Kali Linux.
- Reconnaissance and Enumeration: Reconnaissance and enumeration are essential parts of any penetration test. Be patient. When performing recon, targeting a domain, and leveraging a newly compromised operating system, be thorough about gathering and pillaging information, as one piece of data may be utilized at different portions of the assessment.
- Active Directory: Active Directory stores information about objects on the network, making the information easy for administrators and users to find and use. A comfortable knowledge of AD and common network-based attacks is required to complete the PNPT exam. As mentioned, numerous tools built into Kali Linux were utilized during the exam. Understand what the tools do and how pentesters leverage them to advance their position within an Active Directory environment.
- Windows Credential Storages: Windows will store sensitive information in various parts of the operating system. Understand how Windows protects data and how pentesters may extract them.
- Windows Account Privileges: Windows environments will support different account types with specific user privileges and capabilities. Familiarity with the account types and their respective privileges is important (e.g., standard user, local administrator, service account, domain administrator). Understanding the differences and quickly identifying their capabilities will make the exam more navigable.
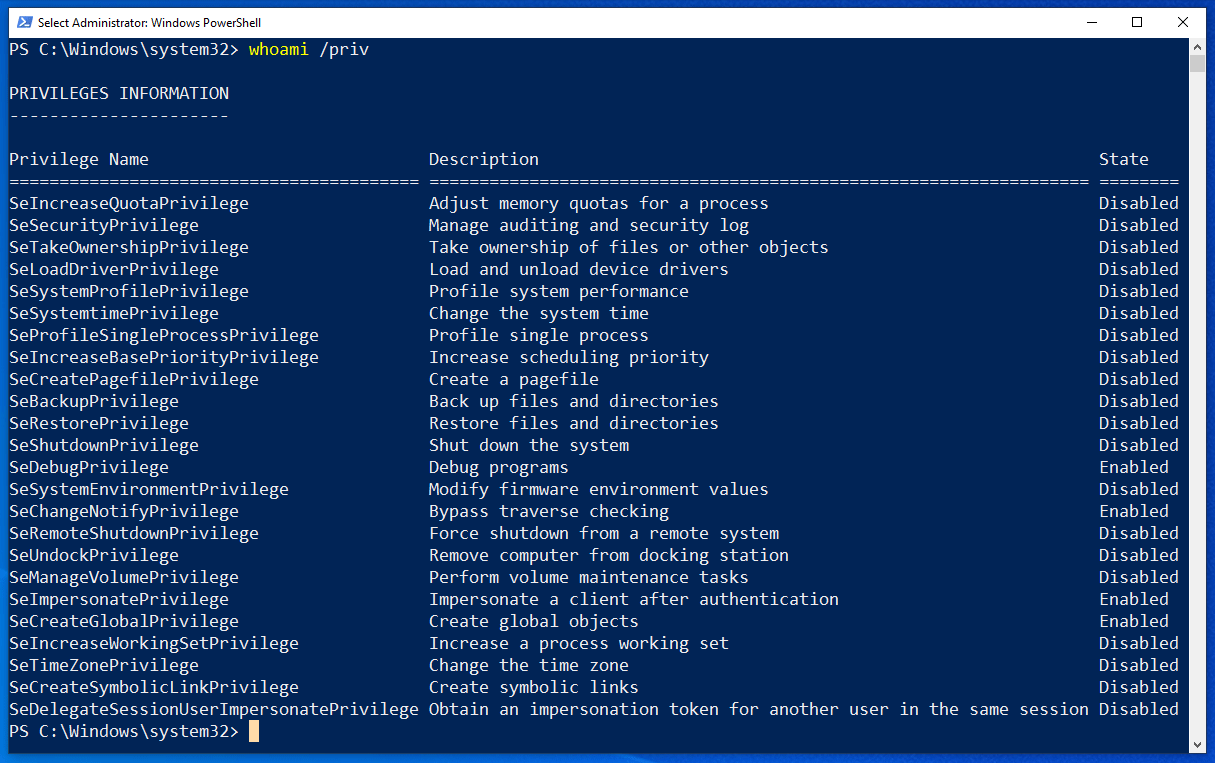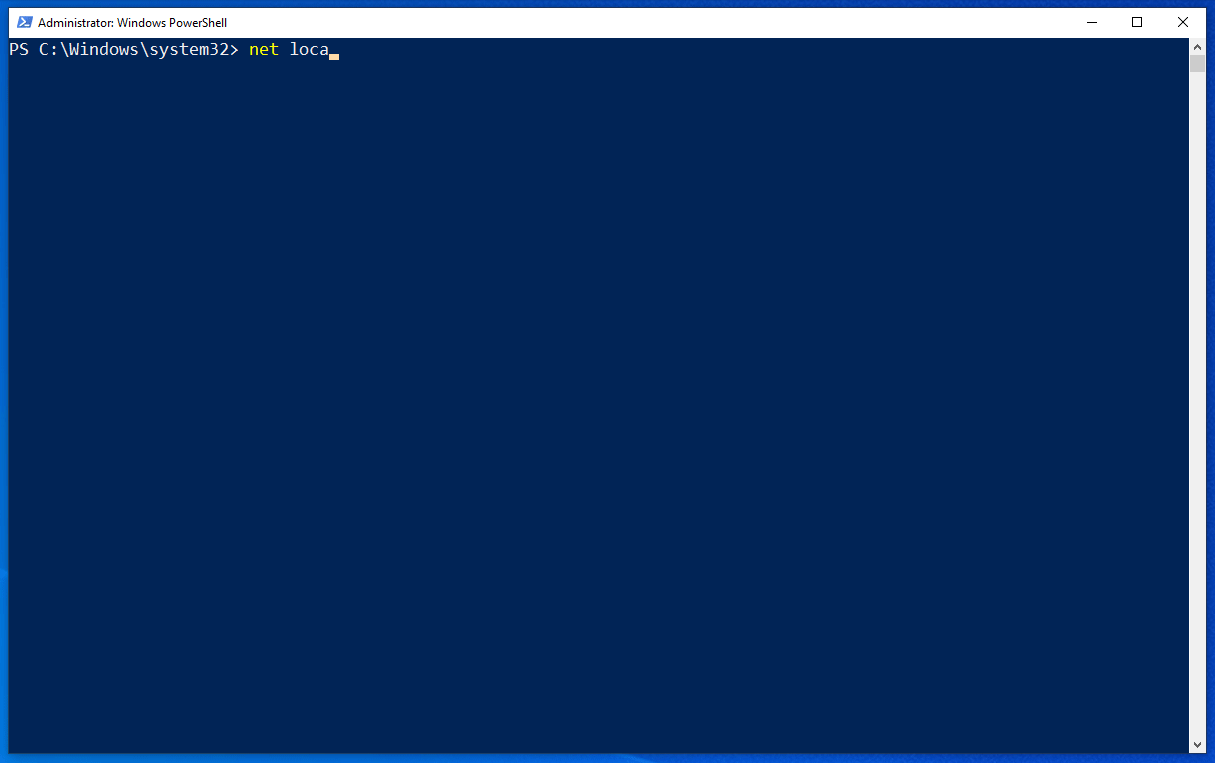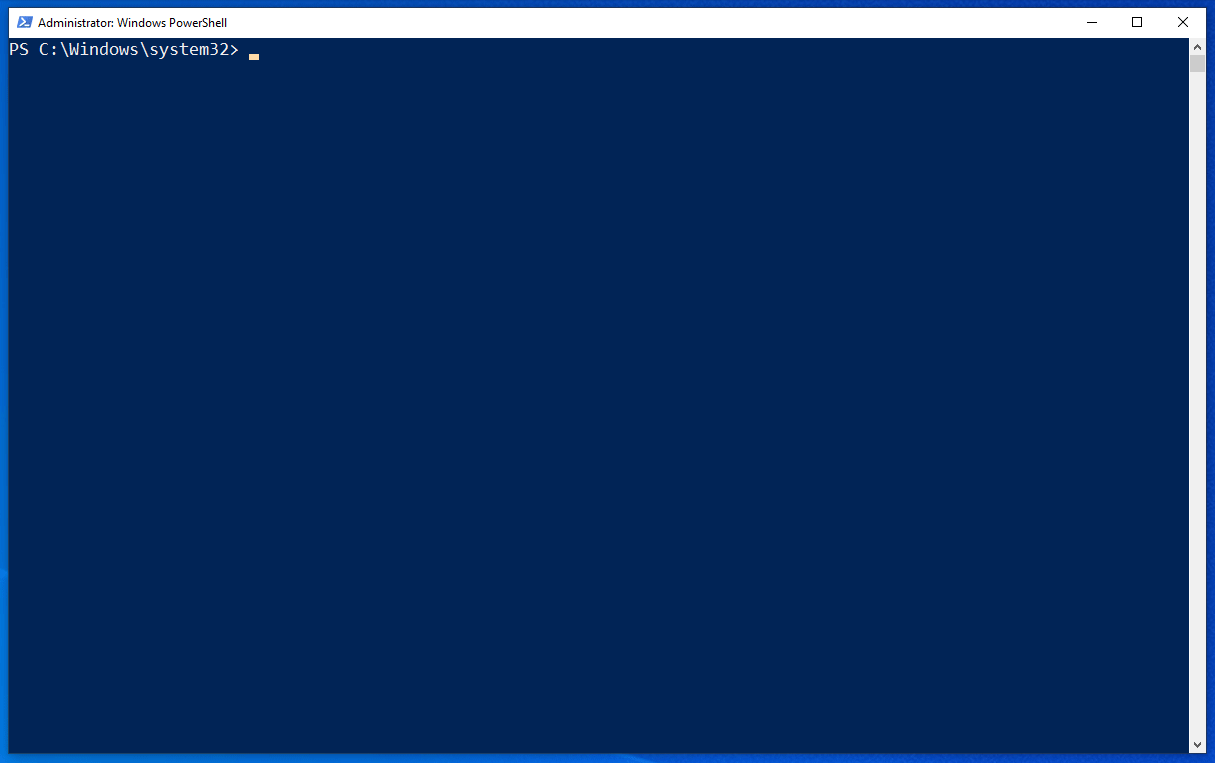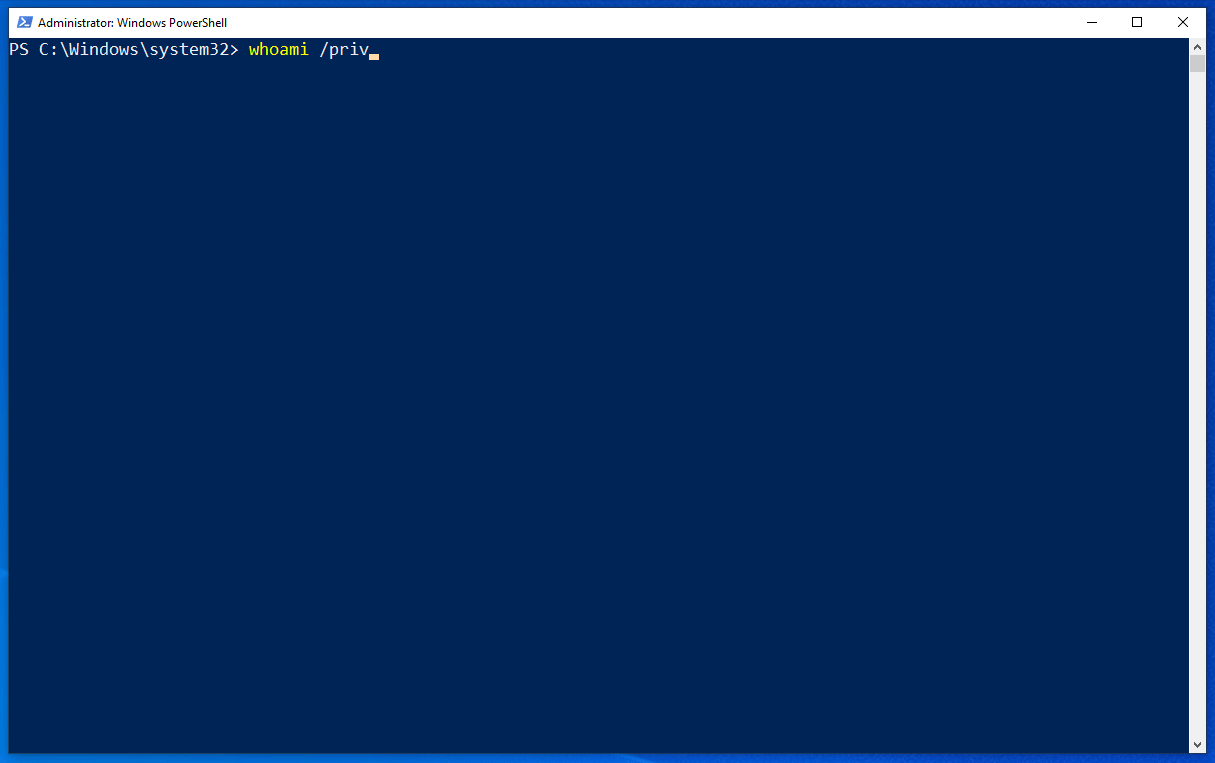
As for general tips:
- Only follow rabbit holes for a few hours. If something seems too elaborate or complex, move on to other avenues. The PNPT exam is not a CTF and closely emulates a (small) real-world AD environment.
- Be patient with escalation points; don’t overthink. Think like an APT and focus on common attacks as seen in PNPT training labs and documented in the MITRE ATT&CK Framework.
- When stuck, take a step back. Reconsider the information discovered previously and other ways pentesters will leverage the data.
In addition to the PNPT training labs, several HackTheBox labs are worth completing before attempting the exam, as they cover valuable topics and tool usage.
- Active: SMB null authentication, Active Directory queries, GPO and GPP, Bloodhound usage, and hash cracking.
- Monteverde: ADConnect, MSSQL databases, Windows post-exploitation, and spidering SMB shares.
- Search: User reconnaissance, Kerbrute usage, PFX certificate cracking, PowerShell web access, AV evasion, and Nishang scripts.
- Scrambled: Impacket scripts, TGT, KRB5CCNAME usage, LDAP queries, SID enumeration via PAC, and MSSQLClient usage.
Reporting
The PNPT certification sets itself apart from most offensive certifications by emphasizing the report quality and the post-engagement debrief.
At BHIS, we take pride in the quality of the reports we deliver to clients. As a result, there’s no shortage of excellent content on the BHIS website dedicated to what makes a stellar pentest report.
- https://www.blackhillsinfosec.com/your-reporting-matters-how-to-improve-pen-test-reporting/
- https://www.blackhillsinfosec.com/how-to-not-suck-at-reporting-or-how-to-write-great-pentesting-reports/
Debriefing
Upon submitting the report, the TCMS team will schedule an on-camera debrief via Zoom to review the Findings documented in the report. The debrief is straightforward. The TCMS assessor will ask for a photo ID as proof of identity, an overview of vulnerabilities discovered during the exam, and an explanation of how the domain controller was ultimately compromised.
At this point, focus on creating a narrative; tell a story, and remember to highlight critical portions of the assessment.
- What vulnerabilities and security misconfigurations did you discover?
- Which tools and techniques did you utilize to exploit vulnerabilities?
- How might a security engineer defend against such attacks in the future?
Walk the assessor through each crucial vulnerability leveraged during the exam from beginning to end.
Conclusion
As a learning tool, the PNPT exam and companion training courses provide enormous value for the price point. Unlike other cyber certifications, the PNPT did not feel like an unrealistic, gamified CTF, making it a fantastic resource for anyone interested in gaining well-rounded knowledge of pentesting methodologies and Windows infrastructure. Overall, it was a fun experience. I appreciated the thought behind the attacks required to compromise the domain controller and look forward to exams produced by TCMS in the future.

Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
