Rooting For Secrets with TruffleHog

The potential leaking of confidential information can pose a significant security risk for any organization. When sensitive details (i.e., API keys, passwords, cryptographic keys, and other credentials) are unintentionally committed to version control systems like Git, they could lead to a compromise of systems, data, or other resources.
Leaking secrets can have severe repercussions for an organization, compromising data integrity, confidentiality, and system security. Exposed tokens can provide unauthorized access to sensitive information, enabling malicious actors to manipulate or steal data, disrupt services, and potentially escalate their attacks. Additionally, exploited tokens could also be leveraged to conduct sophisticated phishing campaigns or launch further cyberattacks.
The impact of this lapse in security could manifest as financial losses, reputational damage, and legal consequences.
So how do you know if you have buried secrets hiding in the vast digital landscape of your organization? Easy. You employ a truffle hog.
TruffleHog
TruffleHog1 is a free security tool designed to root around for sensitive information exposure within version control systems, CI, cloud assets, and file systems. Specifically, it helps identify and mitigate security risks related to the inadvertent storage of credentials, secrets, and other sensitive data.

For example, TruffleHog could scan a Git code repository for patterns that resemble known sensitive information, helping the organization and developers proactively identify and remove such data before it becomes a security vulnerability.
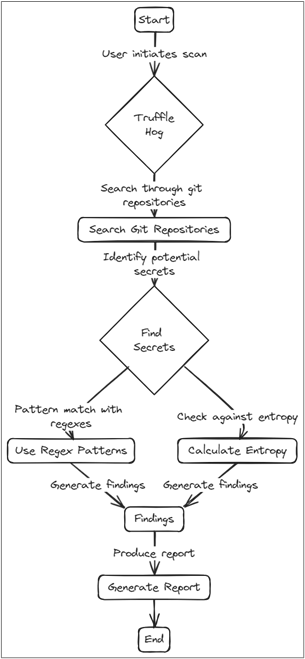
Identifying and cleaning up leaked secrets before an attacker can find them is a crucial component to security.
Installation
Installing TruffleHog is easy using APT by executing the command below.
sudo apt install trufflehogAPT not your thing? Don’t worry. The tool supports several other methods for installation:
- Using
brewon MacOS - Docker
- Binary releases via
https://github.com/trufflesecurity/trufflehog/releases - Git clone and compile from source
- Using the
install.shscript on GitHub (also supports specific version installation
Exact steps for these alternative installation methods can be found at https://github.com/trufflesecurity/trufflehog#floppy_disk-installation.
Sub-Commands
Once installed, it’s time to familiarize yourself with the nine available “sub-commands” that TruffleHog uses to root around for secrets. These can be listed by using the --help flag from the command line as shown below.
trufflehog --help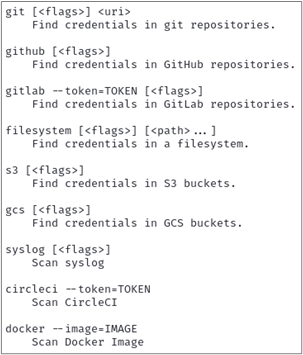
Each of the commands above has specific subsequent “flags” that can be set when executing TruffleHog. These additional flags help to both extend functionality and narrow the tool’s scope. These flags can be listed by including the --help flag after any of the above sub-commands as shown below.
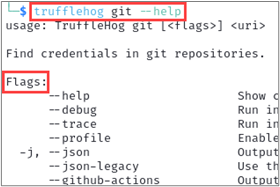
There are some flags that are available across every sub-command. The --json flag, for example, outputs the tool’s results in JSON format.
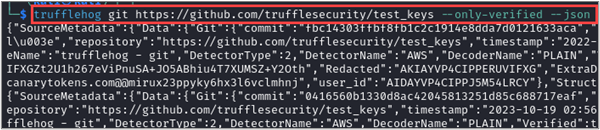
This could then be consumed and parsed by a custom script to convert any findings into even more actionable intelligence. Given the sample TruffleHog JSON output above, let’s say you want to extract information about each detected issue, specifically the commit, file, email, repository, and the detected AWS keys. You can use jq to accomplish this!
The jq command-line tool is a powerful and lightweight way to process and manipulate JSON data. It provides a convenient and efficient way to extract, transform, and filter JSON content, making it a valuable tool for working with JSON-based APIs, configuration files, and data processing.
Some of jq‘s useful features are:
- Querying and Selecting Data
- Filtering and Transformation
- Prettifying Output
- Conditional Processing
- Combining with Other Unix Tools (i.e.,
cat,grep,sed) - Scripting Support
The command below takes our TruffleHog JSON output and extracts commit, file, email, repository, and the detected AWS keys to display in a shortened JSON format.
cat trufflehog_output.json | jq -c '.SourceMetadata.Data.Git as $git | {commit: $git.commit, file: $git.file, email: $git.email, repository: $git.repository, awsKey: .Raw}'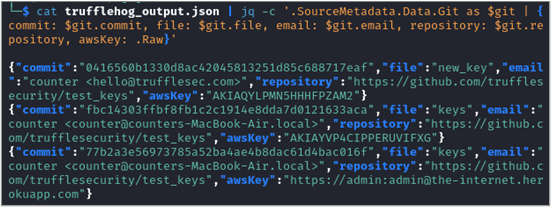
Another shared sub-command flag is --only-verified, which directs TruffleHog to check every potential credential that is detected against the API that it thinks it belongs to. This additional step can help eliminate false positives. For example, the AWS credential detector performs a GetCallerIdentity API call against the AWS API to verify if an AWS credential is active.
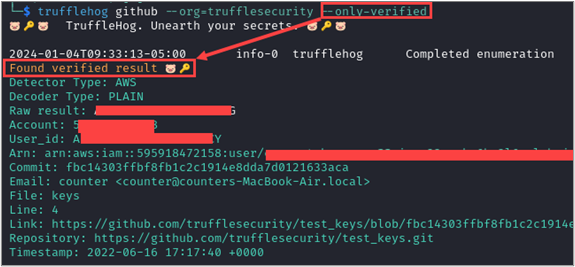
Other flags are sub-command specific like --since-commit and --max-depth, which are available in the git command and control how far back and to what depth into commits the scan focuses on. These are useful to narrow the scope of the scan and incorporate it into your CI process to identify problems before they reach a distributed repository.
Now that we know what TruffleHog is, why it’s important, and understand the basics of how it works, let’s look at some real examples.
Web Application… err… Application
TruffleHog has been so successful in reviewing repositories, filesystems, cloud assets, and CI implementations that it has also been adapted (by third parties) into browser extensions (Chrome2 and Firefox3) to scan web application code returned by a server for secrets too!
For example, the image below shows a React application that graciously returned numerous secrets for a company’s CI/CD pipeline within the main.js file. Including GitHub, Bamboo, Polaris, AWS, and SonarQube secrets.
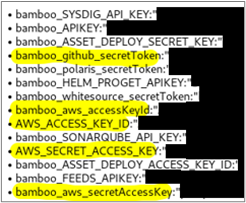
This issue is made worse by the file not requiring authentication to get — meaning anyone online could retrieve these keys. With a little extra legwork, and the help of GitHub’s API, an attacker would discover the GitHub token allowed for full read-write to the organization’s private GitHub. This could also permit user information for who issued the token, the organization’s larger list of users, and repository enumeration.
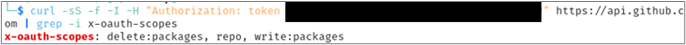
The leaked AWS keys were also valid and could be abused using AWS’s own cli tool4.
My Code Has Secrets. What Now?
BHIS recommends taking the following steps when you encounter secrets in your (or your customer’s) code:
- Remove all secrets.
- Remove the previous commit(s) in the repository’s history that contained the secret.
- Periodically run open-source token scanning software such as TruffleHog.
- Review the CI/CD configurations.
What Next?
If you’re interested in learning more advanced usage of TruffleHog, you can start by checking out their guide on GitHub (https://github.com/trufflesecurity/trufflehog#advanced-usage).
References
- https://github.com/trufflesecurity/trufflehog ↩︎
- https://chromewebstore.google.com/detail/trufflehog/bafhdnhjnlcdbjcdcnafhdcphhnfnhjc ↩︎
- https://addons.mozilla.org/en-US/firefox/addon/trufflehog/ ↩︎
- https://aws.amazon.com/cli/ ↩︎
Enjoyed this blog? Want to learn more?
Chris will be presenting live, online training during The Most Offensive Con That Ever Offensived!
Find more details here: