Shenetworks Recommends: Using Nmap Like a Pro
shenetworks //

One day at work I received a case stating a client couldn’t connect to the management interface of a new server. I asked the client to change the IP address of the management interface and try to connect, and the test was successful. The client was confused and asked why the original IP address wouldn’t work. I asked them to ping the old address and the client was surprised to receive a response back. That IP address was assigned to a device somewhere else on the network. While there are new programs that can help manage your IP addresses and ranges, this is still a common issue in networks. Often caused by poor documentation and stale configurations. The client then had the task of tracking down this rogue IP. Where would you start this process? I would say Nmap is a perfect tool.
Nmap is extremely popular for both defenders and attackers. It originally debuted in Phrack Magazine in 1997 by the author Gordon “Fyodor” Lyon. Nmap has grown into a more complex and powerful tool since its release.
As a Network Engineer, I used Nmap to scan for inventory and to check availability and uptime. As a pentester, I use Nmap to gather information on my targets, and with some scripts, Nmap can be used for a lot more than reconnaissance.
Since Nmap has so many options it might be overwhelming to parse through them to see which ones will be beneficial to you. The next section discusses Nmap options and scripts that I frequently use and recommend.
A basic default Nmap scan will probe a target and check for a response. Once Nmap has verified the host is reachable Nmap will probe for open ports. The default Nmap scan is helpful but with a few options, we can get a lot more information.
Nmap [scan types] [options] {target(s)}
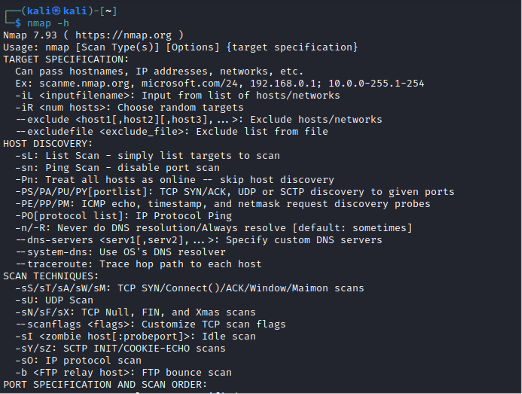
-sL – List Scan
You might want to audit a range of IP addresses knowing some of those IP addresses are unused. Using Nmap with the -sL option will probe every IP address in the given range and do a reverse-DNS lookup. Domain names can often help identify valuable targets. The result will be a list of reachable hosts and their domain name if applicable.
-sV – Version Discovery
Nmap option -sV will attempt to discover the version information of every port open on a host. This information is extremely valuable on an engagement. This will help you identify what type of host you’re probing and the version number. Identifying the version helps prioritize interesting targets and identify available exploits.
-Pn – Skip host discovery
It’s common for network administrators to disable the ICMP protocol or filter traffic to certain hosts. The option -Pn skips host discovery and assumes every IP address is assigned to a host and online. Using this option Nmap can discover additional targets but increase the scan time significantly.
-p- – Scan every port
By default, Nmap scans 1000 ports. Some services may be open but not discoverable with a standard scan. Using the -p- option will scan *every* port 1-65535. This option will increase the duration of scan.
-T4 – Aggressive scan
-T4 will reduce the time for a scan to complete and should be used if you have a fast and reliable connection.
-oX {filepath, filename, and type} – output results into an XML file
I recommend saving your Nmap output into files that can be referenced later in the engagement. The -oX option will save the output in XML format. Saving in XML will allow you to easily parse through the results. This parsing is helpful when you are looking for hosts with specific ports open like SQL, or SMB.
-sC – script scan
Pentesters use a wide variety of specialized tools, however, some may be unaware that the same task can be accomplished with an additional Nmap script. Using Nmap scripts is quick and efficient. With the Nmap Scripting Engine (NSE), users can utilize a collection of scripts with various purposes like discovering additional details about an open port and protocol to further enumeration and brute forcing.
Below are a few Nmap scripts and their descriptions. These are scripts I use regularly. You can find a full list of available scripts here: https://nmap.org/nsedoc/scripts/
sshv1: Checks if an SSH server supports the obsolete and less secure SSH Protocol Version 1.
DHCP discover: Sends a DHCPINFORM request to a host on UDP 67 to obtain all the local configuration parameters without allocating a new address.
ftp-anon: Checks if an FTP server allows anonymous logins.
ftp-brute: Performs brute force password auditing against FTP servers.
http-enum: Enumerates directories used by popular web applications and servers.
http-passwd: Checks if a webserver is vulnerable to directory traversal by attempting to retrieve etc/passwd or \boot(ini).
http-methods: Finds out what options are supported by an HTTP server by sending an OPTIONS request.
ms-sql-info: Attempts to determine configuration and version information for Microsoft SQL server instances.
mysql-enum: Performs valid-user enumeration against MySQL server using a bug.
NSF-showmount: Shows NFS exports, like the showmount -e command.
rdp-enum-encryption: Determines which encryption level is supposed by the RDP service.
smb-enum-shares: Attempts to list shares.
tftp-enum: Enumerates TFTP filenames by testing for a list of common ones.
Nmap is a Swiss army knife and can substitute some of your favorite tools when you’re in a pinch. There are even more Nmap scripts to explore and use. For more information related to Nmap check out their dedicated site and their GitHub https://github.com/nmap/nmap for information on contributing to the project.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
