Why You Really Need to Stop Disabling UAC
Noah Heckman //

Windows Vista didn’t have many fans in the Windows community (to put it lightly). It beaconed in a new user interface, file structure, and a bunch of darn popups asking if you really want to execute the software you just told it to execute.
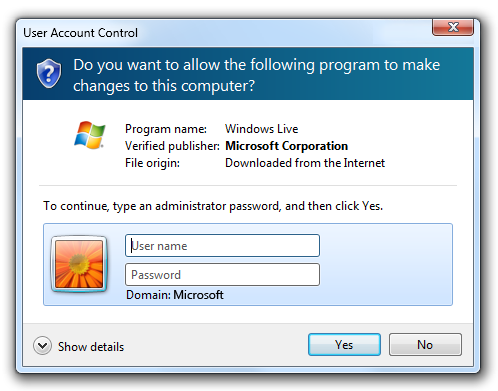
Many sysadmins have found this annoying, but even more annoying was all the end users calling to tell them about how annoying it was. There was a simple solution: just disable it.
Over time, some went back and turned it on, while others did not — instead letting the GPO’s disabling UAC remain in their active directory to this day. However, for those who turned it back on, they were once again reminded about how annoying it was and how many issues it caused. This was, of course, a double-edged sword, as UAC was also annoying to our adversaries.
So what does UAC do? UAC starts its work as soon as you log in. It checks if your account is an admin on the system, and if it is, then the UAC subroutine effectively splits the account into a high privilege and low privilege account. It locks admin operations behind an admin token, which then will prompt you for approval when you go to perform high privilege processes as you see below.
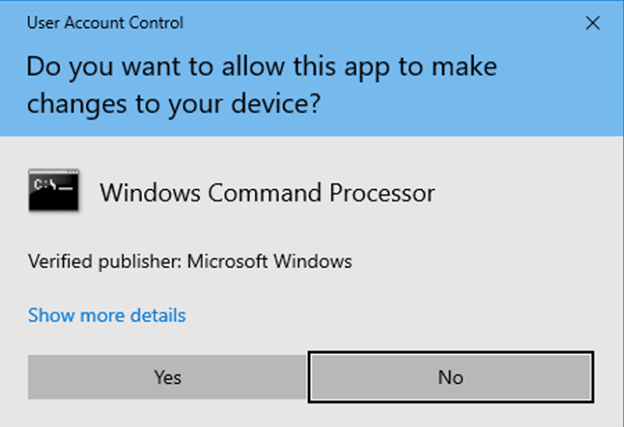
This is known as Admin Approval mode and does not require the user to input the password. In my opinion, this window should say “WARNING! This process is trying to perform admin actions. Do you expect this for this application?” because that is what it means when it interrupts your important spreadsheet session. If you are performing a process that only requires low privilege activities and you see this, you should stop right now!
A common question that has been asked about admin approval mode is “How is this safe? Can’t the process just hit yes for the user and execute the payload?” Not exactly; both the normal UAC and the admin approval UAC prompt are supposed to come up in the Windows Secured Desktop Environment. When this happens, only certain processes can interact with it. Specifically, the logged-in user’s explorer.exe process. So, in general, no, there is not a way for the malware to just “click yes.” Of course, there is a slew of UAC bypass attacks that attempt to subvert these protections, so it is not infallible, but it does dramatically increase the security posture of the system versus having it disabled.
If that is not enough of a reason to make sure you have it enabled, then how about macros? UAC protects a computer from malicious macros more than you think. Of course, it will go off as described above if the macro tries to access or modify sensitive system objects, but what many don’t know is that when you disable UAC, you also disable Mark of The Web (MoTW). MoTW is used to flag files that have been downloaded to your computer from untrusted locations, such as downloaded from the internet or sent as an email attachment. Office applications and other Windows processes look for this “mark” and will restrict certain actions based on it until you approve it.

This is why when you open an Excel document with macros on the internal share, it doesn’t prompt you to “enable editing” and exit Microsoft Office’s Protected Viewer. If your security team is pushing out the GPO settings to “Block Macros in Files Downloaded from the Internet,” this also relies on MoTW. Therefore, if UAC is disabled, the document will not have the MoTW attribute and will sometimes run the macro without prompting, which makes phishing your end users a walk in the park. Another notable feature related to MoTW is the Windows Smart Screen, which is in place to prevent the execution of untrusted code. SmartScreen operates around many of the same principles above by prompting the user on the Secure desktop, asking if they really want to execute the untrusted program. Again, this can help with preventing many initial compromise attacks.
As defenders, we not only need to ensure that these protections are active but that we are using them to our advantage. Disabling macros from documents downloaded from the internet is a great start. Ensure Windows SmartScreen is enabled on the system. For bonus points, consider preventing your end users from being able to bypass it with the “run anyway” button. This will harden your systems, making it even harder for attacks to gain a foothold. All of these settings can be managed by GPO or Intune policy and pushed to the environment with minimal impact. The foundation of a security program is built on good communication. So, should you get complaints from your IT staff, developers, or end-users, please take a moment to explain the underlying process. In their eyes, UAC is nothing but an annoyance, and the standard “because security said so” response is not going to convince them otherwise. We are all busy but taking the time now to educate our people helps to prevent misinformed configurations like the ones that prompted this article from being made in the future.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
