BHIS’s 2nd Annual Infosecker’s* Gift-List
Sierra Ward with help from all // Wow, another year, another Christmas and another chance to be totally stumped by what to get you favorite InfoSecker. But fear not! We are […]
Sierra Ward with help from all // Wow, another year, another Christmas and another chance to be totally stumped by what to get you favorite InfoSecker. But fear not! We are […]
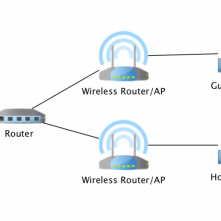
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]
John Strand // I wanted to take a few moments and address the “Hacking Back” law that is working people up. There is a tremendously well-founded fear that this law […]

Matthew Toussain // PowerShell is dead… well dying, kind of. JavaScript interpreters, on the other hand, are everywhere, and they are far from confined to the web browser. Join Matt […]

Gail Menius// The sky is clear, the air is so cool and crisp with the small dusting of snow muting the sounds of Deadwood you can almost hear the stars […]

Beau Bullock & Michael Felch // Source: https://chrome.google.com/webstore/detail/google-calendar-by-google/gmbgaklkmjakoegficnlkhebmhkjfich Overview Google Calendar is one of the many features provided to those who sign up for a Google account along with other popular […]
Lidia Giuliano//* The endpoint protection space is a hot market. With statistics showing malware creation ranging from 300,000 to a million pieces a day, traditional signatures just can’t keep up. […]

Carrie Roberts* // I have added resource file and autorun functionality to PowerShell Empire. Empire now has the ability to run multiple commands at once by specifying the commands in […]
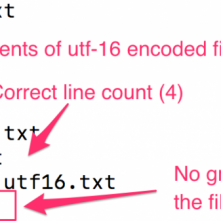
Carrie Roberts//* Have you found yourself trying to Grep through PowerView output, or any PowerShell output for that matter, and find that it returns no results for text you know […]