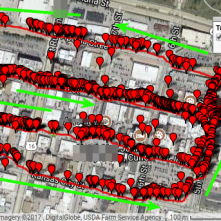
How to: From WarDriving to SSIDs on Google Maps with Latitude/Longitude
Jordan Drysdale // Step 1: Build your capture rig RPi3, Kali, Battery Packs, 2 x supported wifi card of your choosing (I used the Alfa Black for this run). My finished product: Solar Battery […]