Strutting your stuff – Unauthenticated Remote Code Execution
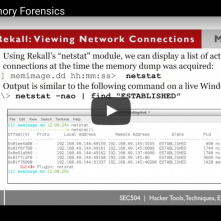
Carrie Roberts // Unauthenticated Remote Code Execution? A hacker’s best friend. And that is what we have with CVE-2017-5638 Apache Struts with working exploit code here: https://github.com/rapid7/metasploit-framework/issues/8064 Save the exploit […]