How to Get USB_Exfiltration Payload Using the Bash Bunny
Jordan Drysdale // This is a super quick write-up on the first very useful payload we tested and confirmed as 100% reliable on all Windows systems (XP-SP3+) with PowerShell enabled. […]

Jordan Drysdale // This is a super quick write-up on the first very useful payload we tested and confirmed as 100% reliable on all Windows systems (XP-SP3+) with PowerShell enabled. […]

Jordan Drysdale // The Wi-Fi travel kit part one was popular enough that, back by demand, here are the specific parts, part numbers and links. Pretty much everything on the list […]

John Strand // Want to get started on a hunt team and discover “bad things” on your network? In this webcast, we will walk through the installation and usage of […]
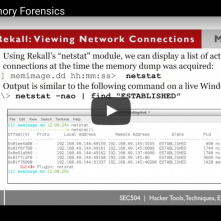
John Strand // In the last webcast we covered initial Windows Live Forensics (see the recording here), in this one we play with memory from a compromised system. We cover the […]

Jordan Drysdale // Sally and I recently ventured to an on-site wireless engagement with a very security-mature customer. Long story short, the level of protection that WPA2 Enterprise with certificate validation provides […]

John Strand // There have been a few conversations at conferences and meet-ups over the past year or so about the validity of penetration testing. There are many things on […]

Brian King // I use GNU Screen mainly to prevent processes from dying when I disconnect from an SSH session, but GNU Screen can do a whole lot more than that […]

Derek Banks // As pentesters, it is probably not a surprise that we tend to make fairly heavy use of Kali Linux on a fairly regular basis. The folks at Offensive […]

Brian Fehrman // As described in my last blog post, Powershell Without Powershell – How To Bypass Application Whitelisting, Environment Restrictions & AV (sheeesh…it’s been a bit!), we are seeing more environments in […]