Wrangling the M365 UAL with PowerShell and SOF-ELK (Part 1 of 3)
Patterson Cake // When it comes to M365 audit and investigation, the “Unified Audit Log” (UAL) is your friend. It can be surly, obstinate, and wholly inadequate, but your friend […]

Patterson Cake // When it comes to M365 audit and investigation, the “Unified Audit Log” (UAL) is your friend. It can be surly, obstinate, and wholly inadequate, but your friend […]

rvrsh3ll // Introduction This blog post is intended to give a light overview of device codes, access tokens, and refresh tokens. Here, I focus on the technical how-to for standing […]

Hannah Cartier // Social engineering, especially phishing, is becoming increasingly prevalent in red team engagements as well as real-world attacks. As security awareness improves and systems become more locked down, […]

Max Boehner & Noah Heckman // Introduction As 2020 sent us all into our homes social distancing, the demand for online messaging saw a huge spike in an effort for people to stay […]
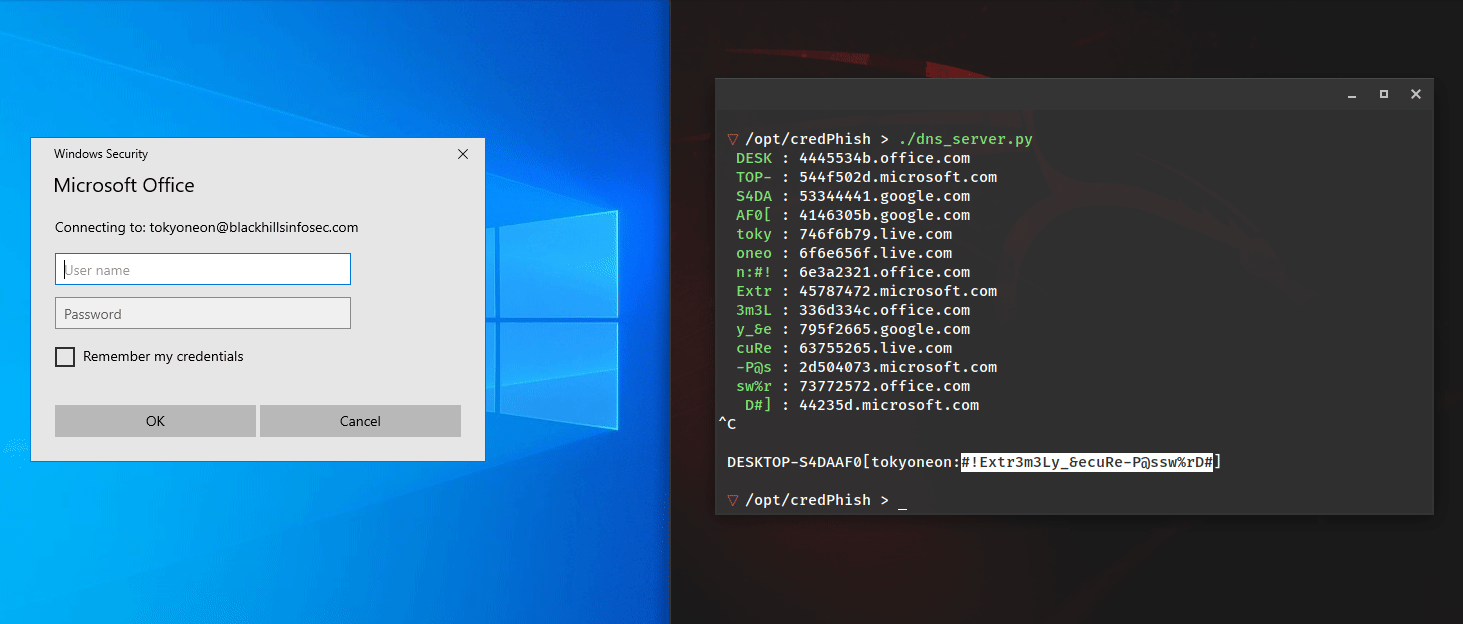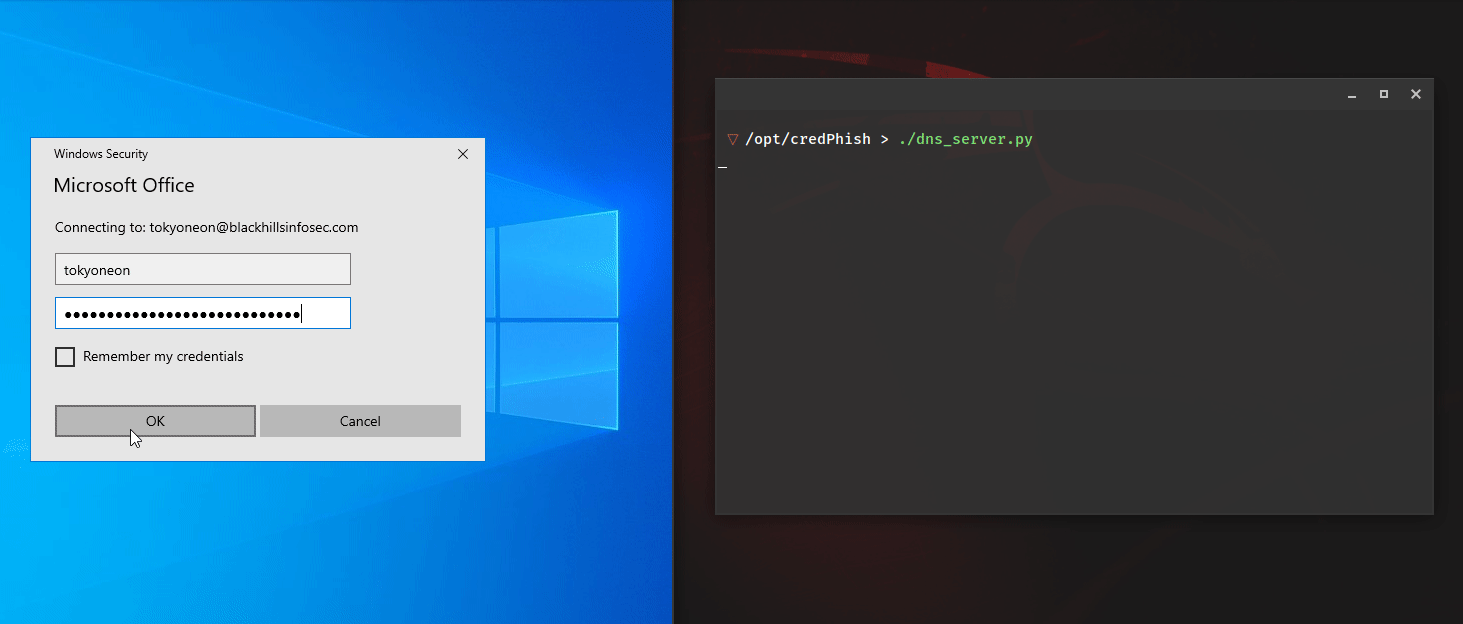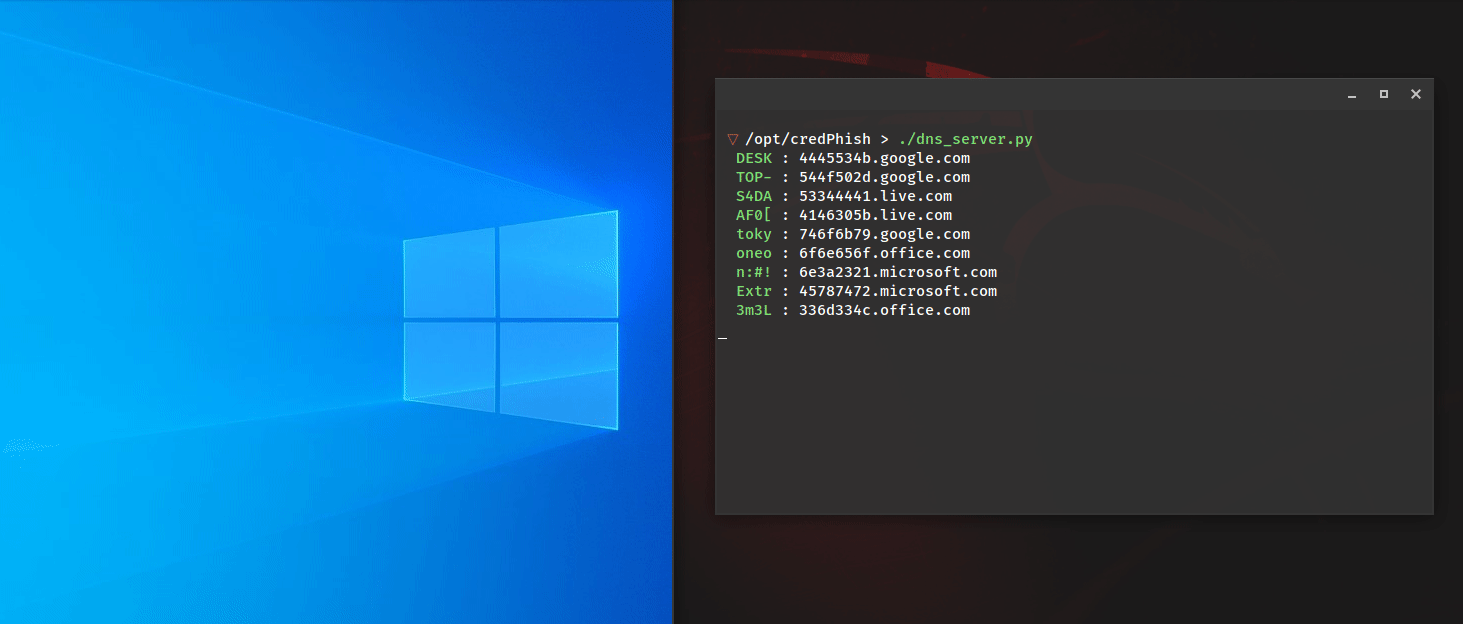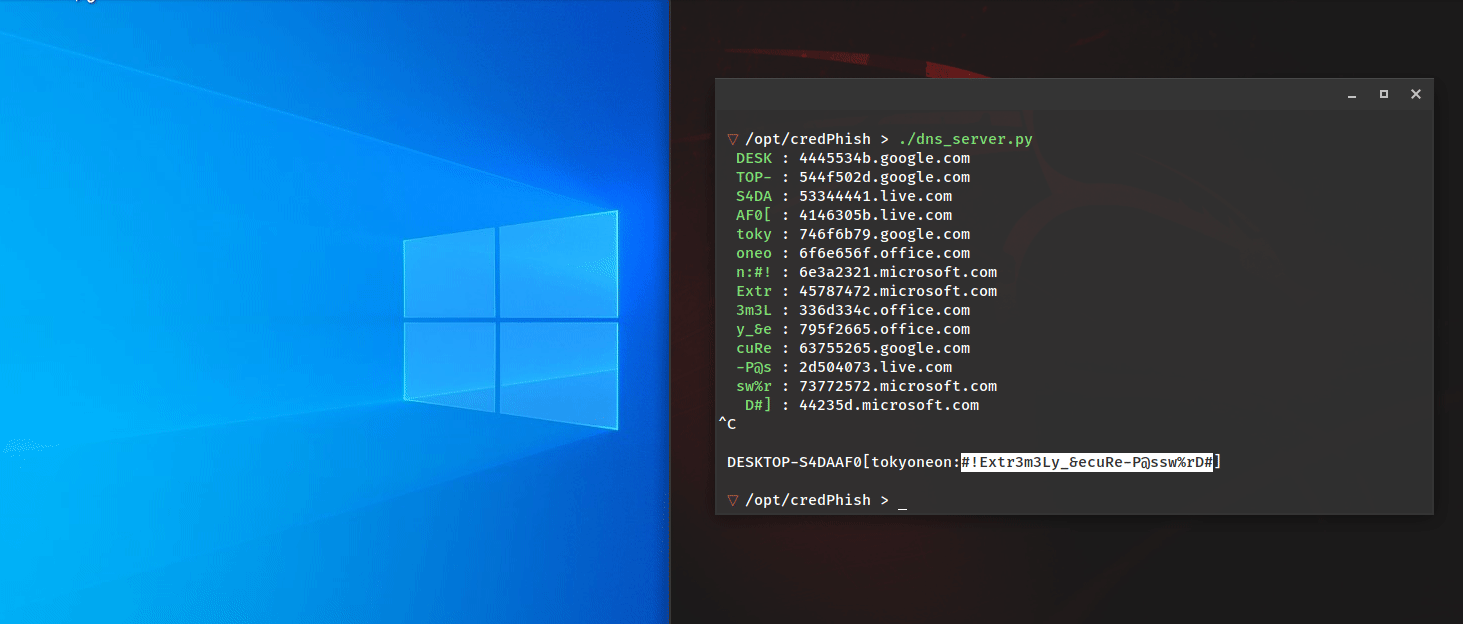
tokyoneon // Spoofing credential prompts is an effective privilege escalation and lateral movement technique. It’s not uncommon to experience seemingly random password prompts for Outlook, VPNs, and various other authentication […]
Building a phishing engagement is hard. While the concept is straightforward, real-world execution is tricky. Being successful takes enormous amounts of up-front setup and knowledge in quickly evolving phishing tactics. […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS

Justin Angel // Penetration testing and red team engagements often require operators to collect user information from various sources that can then be translated into inputs to support social engineering […]

Beau Bullock & Mike Felch// Strategically targeting a corporation requires deep knowledge of their technologies and employees. Successfully compromising an organization can depend on the quality of reconnaissance a tester […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS

Beau Bullock & Mike Felch// Strategically targeting a corporation requires deep knowledge of their technologies and employees. Successfully compromising an organization can depend on the quality of reconnaissance a tester […]