How to Not Get Scammed on Discord
Max Boehner & Noah Heckman //

Introduction
As 2020 sent us all into our homes social distancing, the demand for online messaging saw a huge spike in an effort for people to stay in contact with each other. In some cases, even entire social events (like conferences and club meetings) were ported to platforms such as Discord and Slack to increase biological security, while still allowing individuals to meet and communicate with each other. But like all things, when the user base moves, so do the actors who will try to take advantage of them. Since Black Hills Information Security (BHIS) has a vested interest in Discord, we wanted to write this blog to provide an overview of currently common attacks against Discord users that we are seeing, and how to protect yourself from them.
User Account Takeover
During our research, we found that one of the most common goals of social engineering on Discord is the takeover of legitimate Discord user accounts. To understand the motives behind those attacks, it is important to understand the value of these accounts and what attackers are using them for. After all, why would the attackers not simply create new accounts instead of going through the trouble of compromising those of others?
While researching this topic, we learned about the value of existing accounts first-hand. To learn more about Discord phishing, we actively tried to become targets of such attacks. We created Discord burner accounts and joined servers on various topics that might attract scammers. However, we noticed that many Discord servers have hurdles in place that make it more difficult for users to join. While some servers only allow user accounts with verified phone numbers, others require solving small challenges to prove the user is not a bot, such as reacting to a specific message.
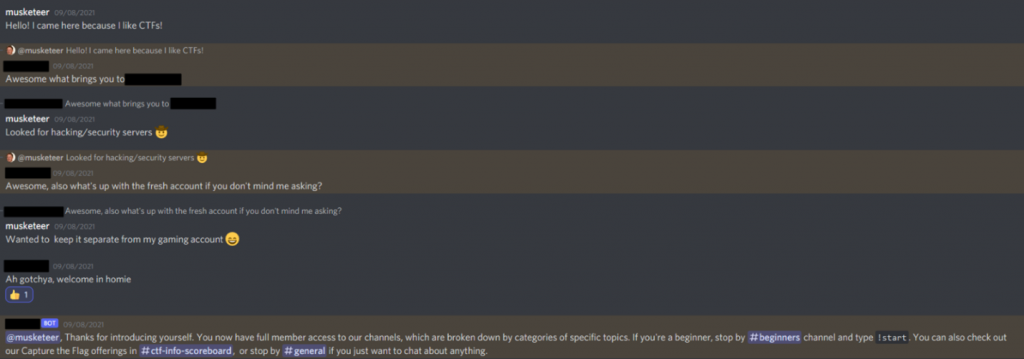
In one case, we were even vetted in a discussion with an administrator who also inquired about the short lifetime of our account.
Compromising existing user accounts can aid attackers in circumventing these server protections since existing accounts will often be members of servers already. Access to such servers gives them the opportunity to post phishing messages within the chat rooms or to send direct messages to other server members. What makes this even more effective for social engineering is the fact that Discord servers are often dedicated to a specific topic—such as gaming, cryptocurrencies, or information security. This allows attackers to craft their message pretexts with a specific audience in mind, increasing the chance of success. For example, members of a Discord server related to cryptocurrency may be more susceptible to phishing messages related to that topic than others. Similarly, members of a gaming Discord server are excellent targets for attacks aimed at taking over accounts for gaming platforms, such as Steam.
Additionally, existing users will often have contacts within Discord that may be more likely to trust them, thus increasing the chance of success for further social engineering attacks. These further attacks can either be aimed at compromising more Discord accounts or at achieving additional goals, such as financial gain. We will discuss typical end goals of these account takeover campaigns later on in this blog.
Now that we have established the value of legitimate Discord accounts, we will provide some examples of common ways attacks are conducted. Here we found that phishing for Discord accounts typically uses pretexts related to Discord.
A social engineering technique that has been discussed in the past (for example, in this Portswigger blog post: https://portswigger.net/daily-swig/discord-users-warned-over-qr-code-login-scam-that-can-result-in-pwned-accounts involves the Discord’s QR code login function. For this to work, the victim needs to be logged in to the Discord mobile app on their phone. An attacker will then send the victim a QR code obtained from the Discord login page and attempt to trick the victim into scanning it with their app.
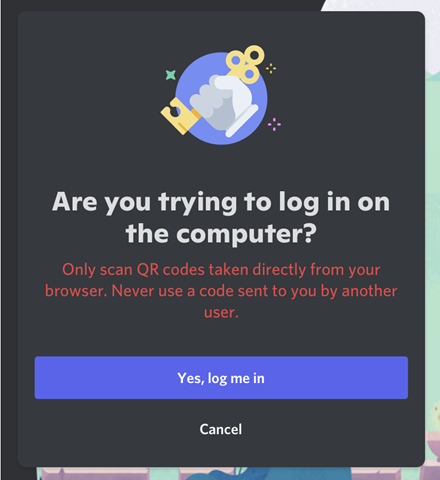
If the victim scans the QR code, they will be prompted to confirm that they want to log in. If the “Yes, log me in” button is pressed, the attacker is logged into the victim’s account.
Discord has acknowledged these QR code attacks and shortened the validity period of QR codes to two minutes to reduce the likelihood of success (https://support.discord.com/hc/en-us/articles/360039213771-QR-Code-Login-FAQ). However, within these restrictions, the attack is still possible in the way described above.
Our research indicates that some of the most common account takeover attacks are related to free Discord Nitro subscriptions. Discord Nitro is a paid subscription which offers additional features to Discord users. These include more detailed profile pages, additional emojis and stickers, bigger file uploads, and so on. These features are desirable enough to many users that the offer of free Nitro has become a quite successful social engineering pretext. One factor that may aid attackers here is that legitimate Nitro giveaways have happened in the past. On top of that, a legitimate way to gift Discord Nitro to other users exists, which generates a link pointing to the discord.gift domain (source: https://support.discord.com/hc/de/articles/1500001829622-Claiming-a-Nitro-Gift-FAQ). Users who know about these legitimate giveaways may be more inclined to react to social engineering attacks that mimic these giveaways.
These phishing attacks can take various forms. They may, for example, entice the user into opening a link to an attacker’s website that prompts the user to log in with their Discord credentials, potentially providing the attacker with access to the user’s account. One way to trick users into thinking a link is legitimate is through typosquatting a domain that appears to be related to Nitro gifts. Those can either be targeted at Discord account takeover or at the takeover of third-party platform accounts. We will provide an example of the latter in the next section.
Steam Account Takeover
A popular variant of this attack method uses the promise of free Nitro access to compromise Steam accounts. Steam is a popular gaming platform used by millions of players. It also includes marketplace and trading features that can be used to buy, sell, and trade virtual items from games, as well as a wallet feature that lets users store funds. Attackers who compromise Steam accounts may be able to gain a direct financial benefit from doing so. Steam forums and communities like Reddit contain numerous reports of users who have suffered from account takeovers after falling for similar Discord Nitro phishing attacks.
The outline below provides an example of such a phishing attack. The attack starts with a message sent to users containing a typosquatting link.
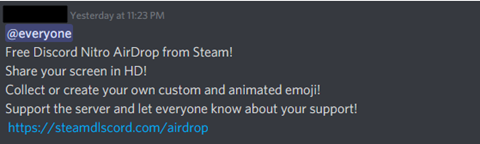
The page that is opened attempts to mimic the look of the official discord.com website. Many of the links contained even point back to the valid Discord domain in an attempt to make the site look as legitimate as possible.
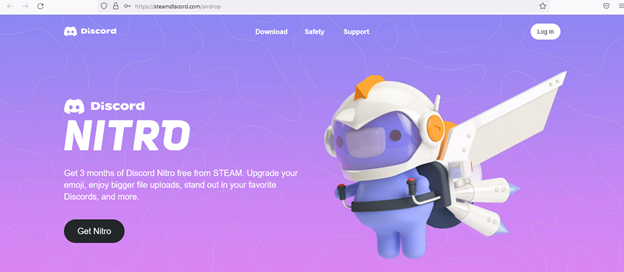
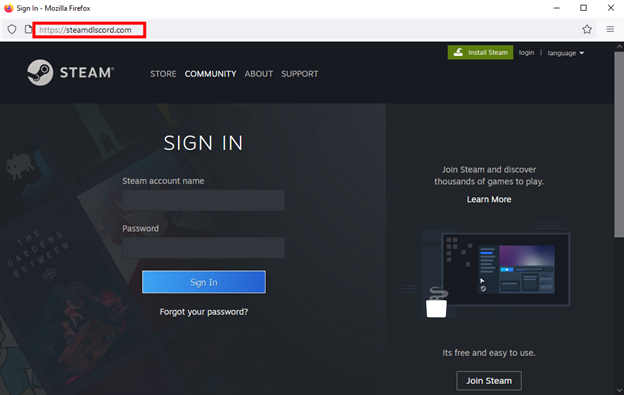
Clicking the “Get Nitro” button opens a login page that is visually similar to the Steam login page. However, this page is also hosted on the steamdlscord[.]com domain, suggesting that this is aimed at capturing Steam credentials.
If the account takeover is successful, the attackers may attempt to trade off any valuable items in the account inventory or use the account’s wallet balance to buy game gift codes. While account recovery from this is typically possible, those efforts may not be able to restore any lost valuables.
Another dishonorable mention in the Steam account takeover category involves scammers messaging victims on Discord that they have “accidentally” reported them for abuse on Steam and now the victim must take action to prevent their account from being banned. An important part of the pretext here is that the victim has linked their Discord and Steam accounts, providing a very useful piece of information to the attacker, allowing them to create a more believable pretext. This blog describes this technique in detail: https://blog.malwarebytes.com/scams/2021/03/steam-users-dont-fall-for-the-i-accidentally-reported-you-scam/.
Cryptocurrency Scams
Cryptocurrencies are another commonly used topic within social engineering attempts on Discord. While they are expectedly quite common on servers related to this topic, they are also prevalent on unrelated servers. While the pretexts and delivery methods can vary, the end goal is always the same: gaining a financial benefit at the expense of unsuspecting victims.
The following message shows an example that attempts to get the victim to visit a seemingly legitimate cryptocurrency change website under the guise of a Bitcoin giveaway.
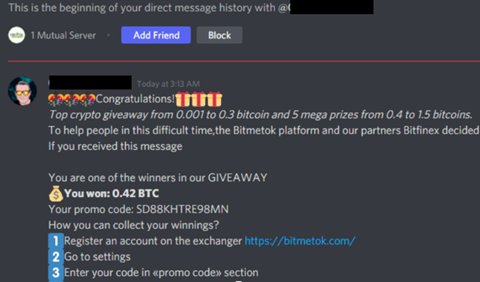
The messenger offers a promo code that promises 0.42 BTC (Bitcoin) as a giveaway. At the time of this writing, that is equivalent to approximately 20k USD. That sounds too good to be true, right?
The scammers have made great efforts to make the target site appear like a legitimate crypto exchange.

When scanning the site via urlscan.io, an interesting observation can be made though. There appear to be a large number of similar other sites available.
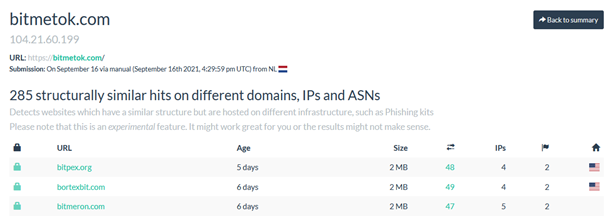
Visually, the only difference between these sites is their domain name, as well as the name displayed on the site.

From this point forward, the victim would need to register to this trading site to enter the “promo” code. We did not investigate further into this specific site but, based on other research, we suspect that the next steps would have asked us to pay a fee to unlock the 0.42 BTC, without the promised Bitcoin ever being paid afterwards. For further explanation of this scam, please have a look at this video: https://youtu.be/R7WL_xFF0R8.
Another common social engineering technique that we observed includes sending Discord server invite links via direct messages or other server chat rooms. While inviting users to new servers is not directly malicious, it can function as a precursor to later social engineering attacks.
We received the following message inviting us to a cryptocurrency arbitrage trading server, promising free money via arbitrage between different trading platforms.
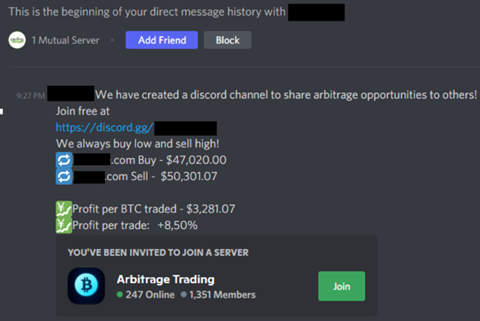
This particular attack appears to revolve around victims being coerced into buying cryptocurrency from a legitimate trading site and then sending it to a fraudulent one.
Malware Distribution via Discord
Oftentimes used along with the methods above, there has been a multitude of reports regarding malware distribution via Discord. There are several contributors as to why this works specifically well with Discord vs other platforms. One of the main reasons is due to Discord having a universally available worldwide content delivery network (CDN). Intended to allow users to share files and pictures back and forth, this service allows attackers to host malware on trusted servers owned by Discord. When files are uploaded to Discord, it will upload them to the service which is hosted at cdn.discordapp.com. While CDN abuse is not new, when paired with spear phishing, this may convince some users that this file is coming from a “trusted” source.
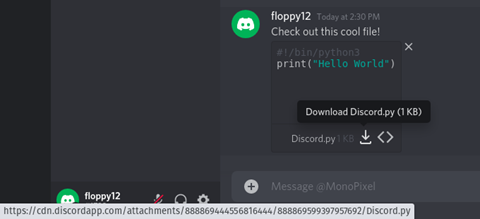
This also means that for any users/employers who are running access control lists (ACL’s) blocking commonly abused sites such as GitHub or Pastebin, the attackers may be able to bypass said protections if you allow traffic to Discord’s CDN service.
Malware Targeting the Discord Client
Of course, that example requires the user to download and execute the file stored on the CDN. There are historically easier methods however… In 2020, Masato Kinugawa published a blog post regarding a full exploit chain on the Discord client to achieve remote code execution by simply having the end user click on an iframe, causing a 3d project file hosted on sketchfab to render and execute NodeJS code. Discord is built on Electron, which can allow the web application to access local system resources, bypassing some of the sandboxing features which have become a staple in the security of the modern web browser. While the client may be a convenient way to access the chat application, it may not be your safest option. Another notable element in the exploit chain was the exploit of Discord’s iframe embedding in its web application. While this feature can be disabled in the user settings, it is enabled by default.
Another notable Discord malware known as BlueFace was found by MalwareHunterTeam and reported by bleepingcomputer.com back in 2019, when malware was discovered to be modifying the JavaScript for the application to weaponize the client and exfiltrate information to the attacker. These examples show that the Discord client is actively being tested for exploits that are specifically related to its use of Electron. Depending on your threat model, you may want to consider disabling this, though it will come at the expense of breaking all those fantastic gifs in your chat. Even better still, consider accessing Discord via a web browser instead of the Electron app, if possible.
Protections and Countermeasures
The best protection against social engineering attacks is knowing that they can occur and staying suspicious of messages, links, or server invites. This will also be the last line of defense, if all other preventative measures fail and a malicious message gets through to the user. To lower the likelihood of such messages appearing there, the following settings can be configured by users:
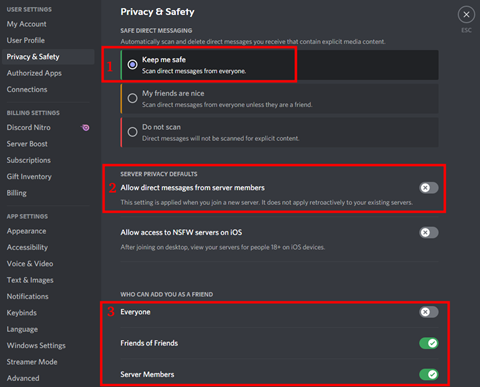
- Safe Direct Messaging: This will scan all images and videos sent to the user via direct messages and block potentially undesired content. While not directly aimed at preventing phishing, this may help filter out malicious messages, in some cases. We recommend choosing either the top or middle option.
- Server Privacy Defaults: This option sets the default value for allowing direct messages from users that have at least one common server with the user. Disabling this option will reduce the risk of receiving phishing messages. This option can also be set on a per-server basis by right-clicking on a specific server. We recommend setting the default value to “disabled” and enabling direct messages only for servers that you trust.
- Who Can Add You as a Friend: This option defines who can add you as a friend in Discord. Any user that you add as a friend will be able to send you direct messages, regardless of setting #2. Disabling the “Everyone” option can help prevent social engineering attacks but may also prevent legitimate friend requests. For added security, disabling the “Server Members” setting is also an option.
To reduce the likelihood of successful account hijacking attacks, we recommend enabling Two-Factor Authentication. While this does not protect against the QR code attack described above, it can reduce the impact of other credential-stealing attacks.
Using Discord from within a web browser, as opposed to the Desktop application for added security, was already mentioned earlier. However, if you choose to use the Desktop application, we recommend checking that the feature “Automatically detect accounts from other platforms on this computer” is disabled.

Additionally, we advise you not to connect accounts from other services, such as Steam or Twitch, to your Discord account. Having other accounts connected may give attackers additional information that can be used for social engineering attacks. This practice is also good for privacy.
On top of measures that can be taken by individual users, there are also ways for server admins to improve security. Please refer to this official Discord documentation page for more information: https://discord.com/safety/360043653152-Four-steps-to-a-super-safe-server
Summary
We wrote this blog with the intention of providing an overview of currently common attacks against Discord users. We showed that attackers are often using Discord to target specific user groups, such as Steam users or cryptocurrency enthusiasts, and may be using the Discord platform itself to host malicious files for their attacks. Knowing about the prevalence and different variants of social engineering attacks can help strengthen users’ security posture. To follow up, we have provided a list of mitigations, and instructions on how users can implement them to reduce the likelihood of falling victim to such attacks. However, like most phishing and social engineering attacks vectors, it often comes down to the vigilance of each individual user to avoid falling victim.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand
