Parsing Sysmon Logs on Microsoft Sentinel

Tl;dr: Many parsers have been written and several are referenced here. This blog describes a simple parser for Sysmon logs through Event ID (EID) 28 for Microsoft Sentinel.
Let’s start with a description of the Sysmon schema version. As shown below, the latest schema version as of 23-DEC-22 was 4.83. This will need to be updated in your Sysmon config files if you wish to stay bleeding edge.
The following blocks include some additions to the version of Sysmon modular generating as of 23-DEC-22. Modular was referenced in a link above, the few lines below allow the writing of Sysmon EIDs 27 and 28 to the operational logs.
But wait… why am I talking about these things in the Sentinel Sysmon parser’s GitHub repo? Hang tight, trust the process, we will get through this.
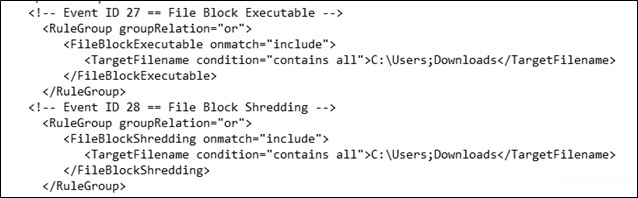
As you can see, default download (c:\users*\downloads) locations in userland get blocked with the Sysmon EID 27 configuration shown above. This configuration is insufficient for proper usage for modern protective considerations but demonstrates the possibilities.
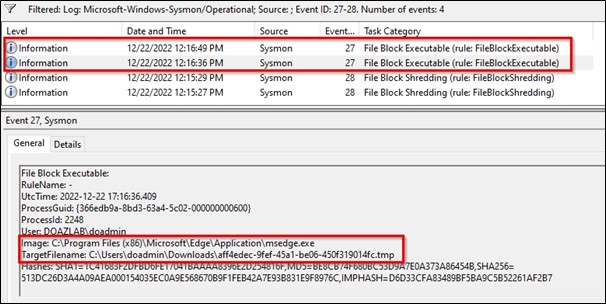
This event then gets written to Windows logs. Assuming you are integrated with Microsoft Analytics or Log Analytics agents and are capturing Sysmon logs in your workspace, these logs will be queryable in just a few minutes.
We can now also restrict file shredding in locations we configure with the config file directives. Scroll back up and check out the <– EID 28 –> config block. All we restrict is c:\users*\Downloads; obviously, this is insufficient.
Shown next is an attempt to SDelete (shred) the Firefox installer (pretend this is an adversary trying to cover their tracks). BLOCKED!!!!!!!
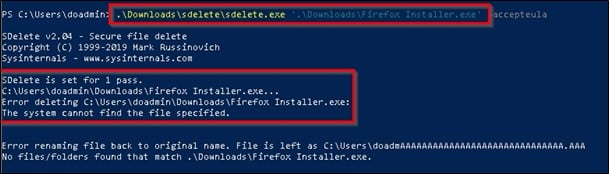
This was also written to the event log.
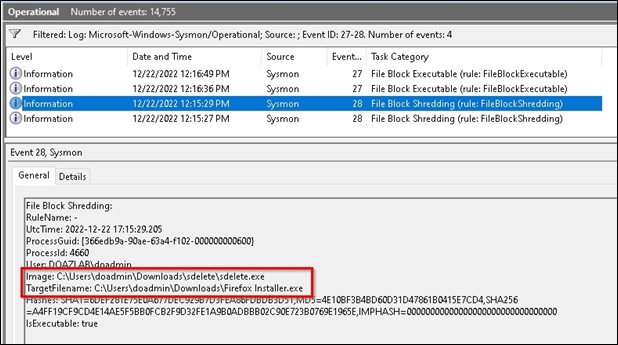
Now for the actual goods — what we all came here for. If you want to make your Sysmon logs meaningful in most SIEMs, you need to parse them. There are a few parsers available, and some appear to be well-maintained. The link below was last updated on March 1, 2023, and appears to cover all versions of Sysmon.
Microsoft Azure Parsers GitHub Repo — and has a Sysmon parser available.
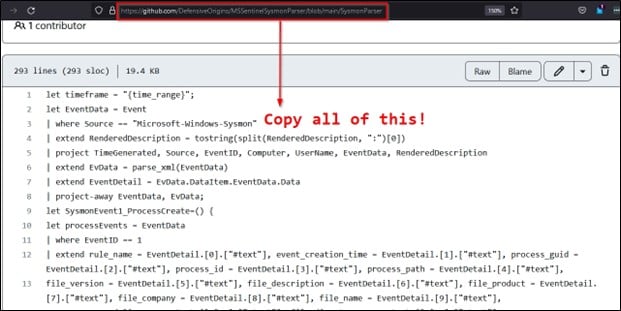
Buttttttttt, here’s another one we wrote for our APT class crafted from other bits and pieces available.
As shown, you want to copy the contents of the parser.
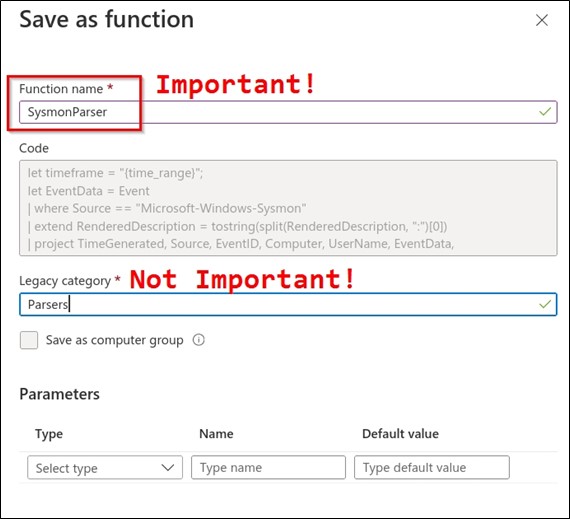
Paste the entire blob into a Sentinel > Logs query window and run it. The query may take a moment. Once complete, click to Save As > Function.
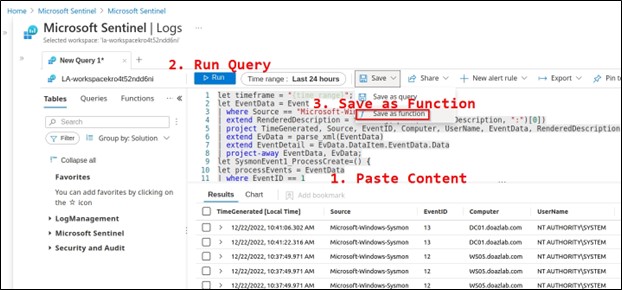
Name the function accordingly — it matters — because you will be using this to query Sysmon logs in all future queries. As shown, it was named SysmonParser.
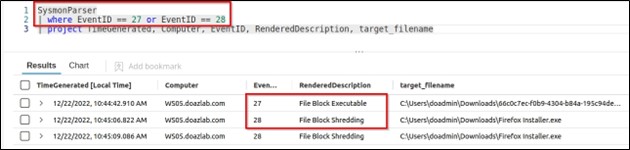
Finally, run the function in a new query window by calling SysmonParser() and looking for those couple of event IDs – 27 and 28.
Reference Materials:
Sysmon – the best system monitor for Windows! Even better than Windows auditing!
Olaf Hartong’s Sysmon Modular – The best configuration generator for Sysmon ever shared with the world!
Olaf Hartong’s recent article on Sysmon EID 27 – file block executables – and the baseline for getting this written, the parser cleaned up, and pushed to GitHub.
Thanks for reading and keep defending out there!
-jd
Want to learn more mad skills from the person who wrote this blog?
Check out this class from Kent and Jordan:
