Fixing Content-Security-Policies with Cloudflare Workers
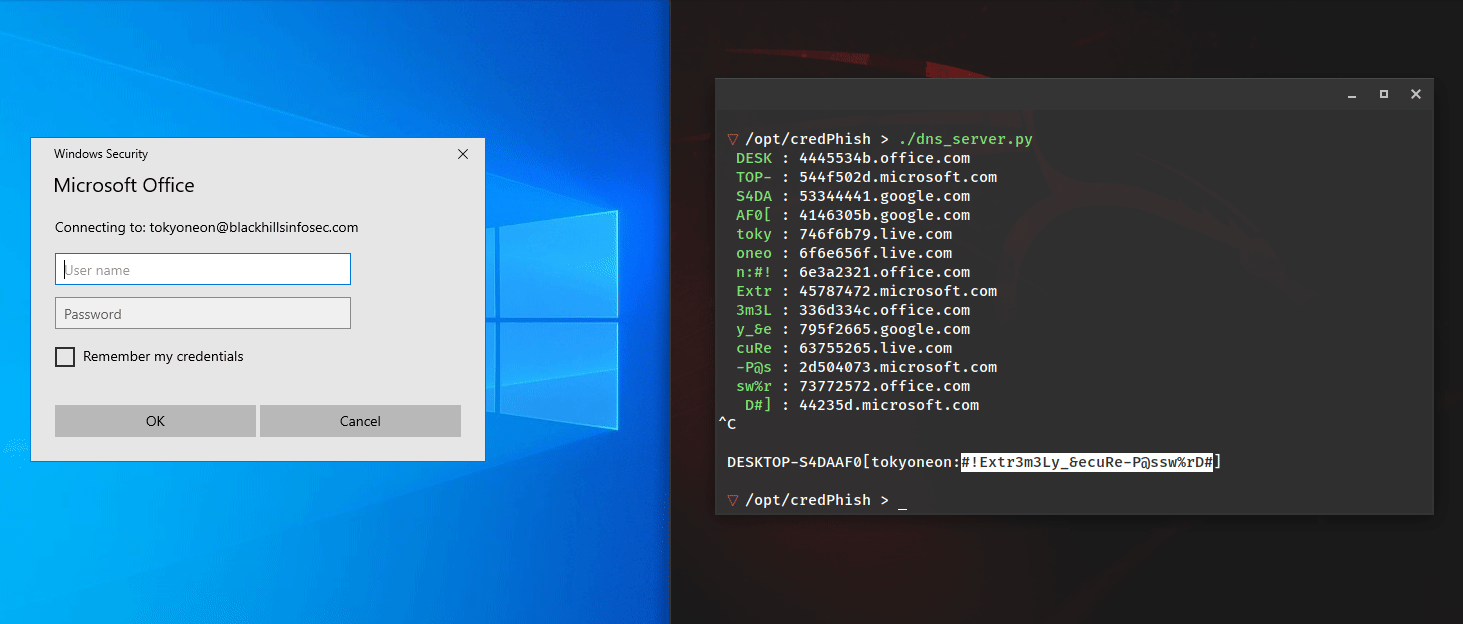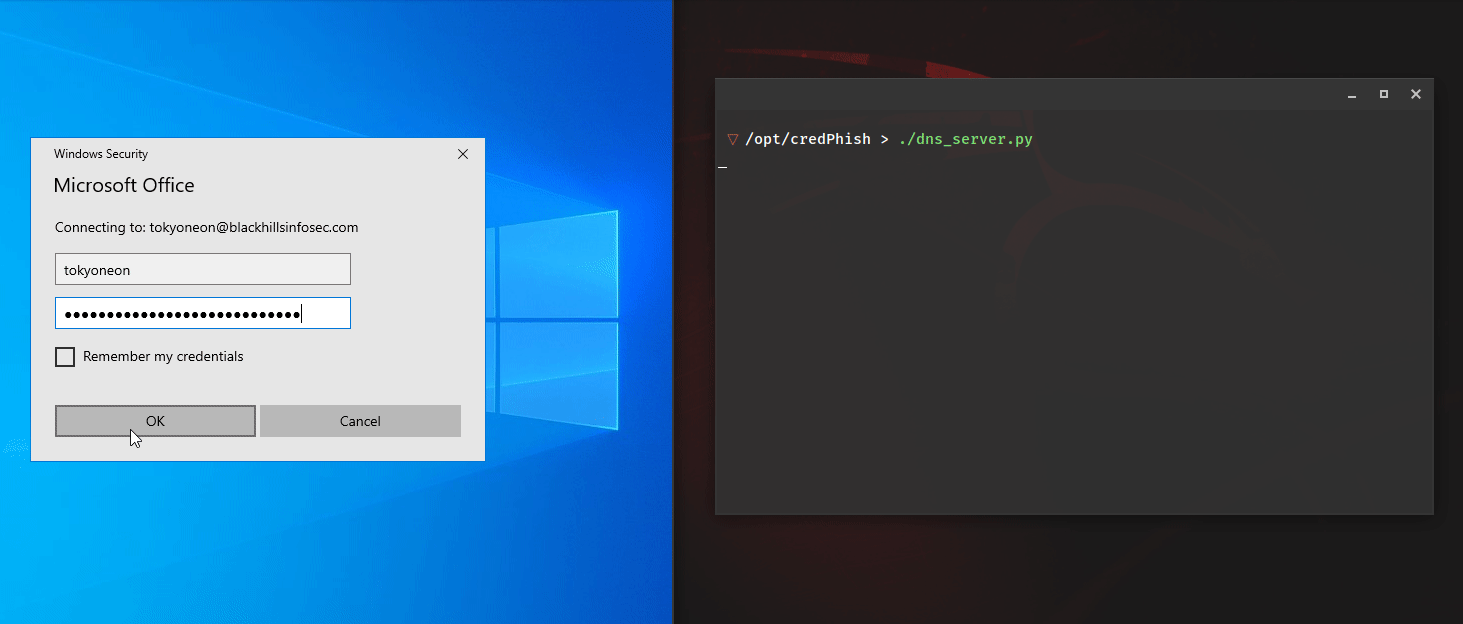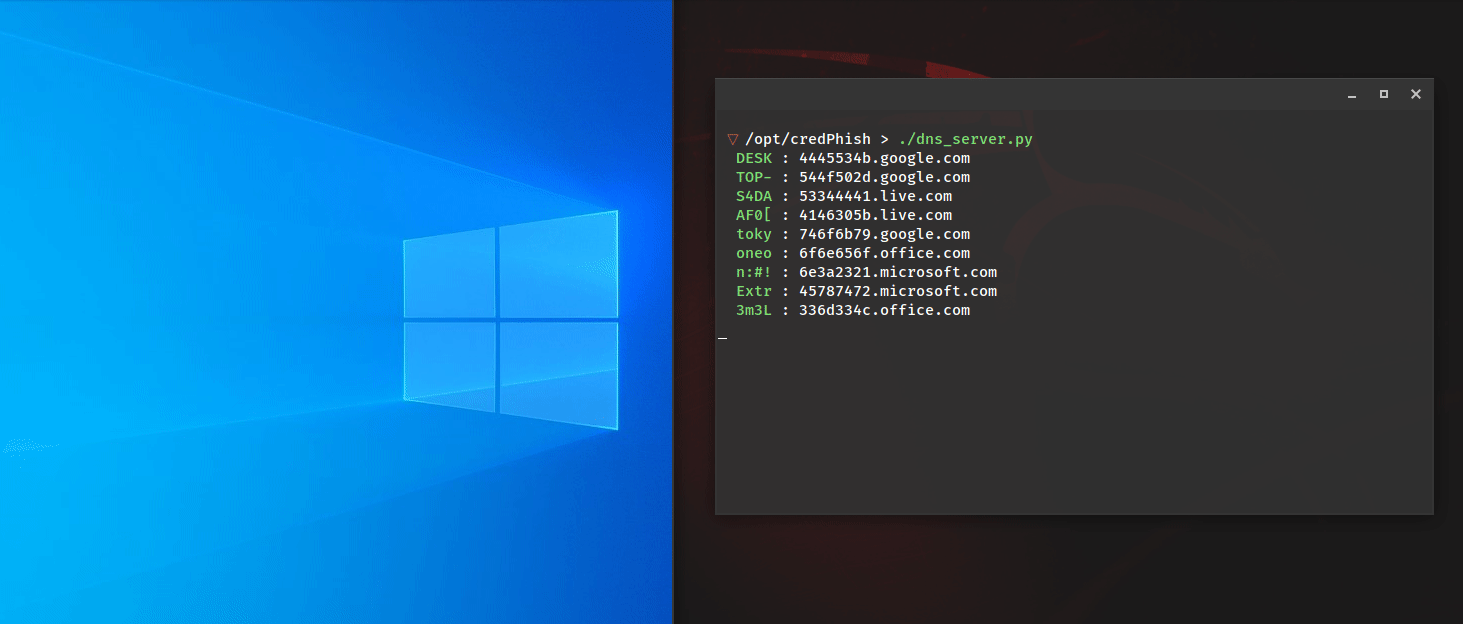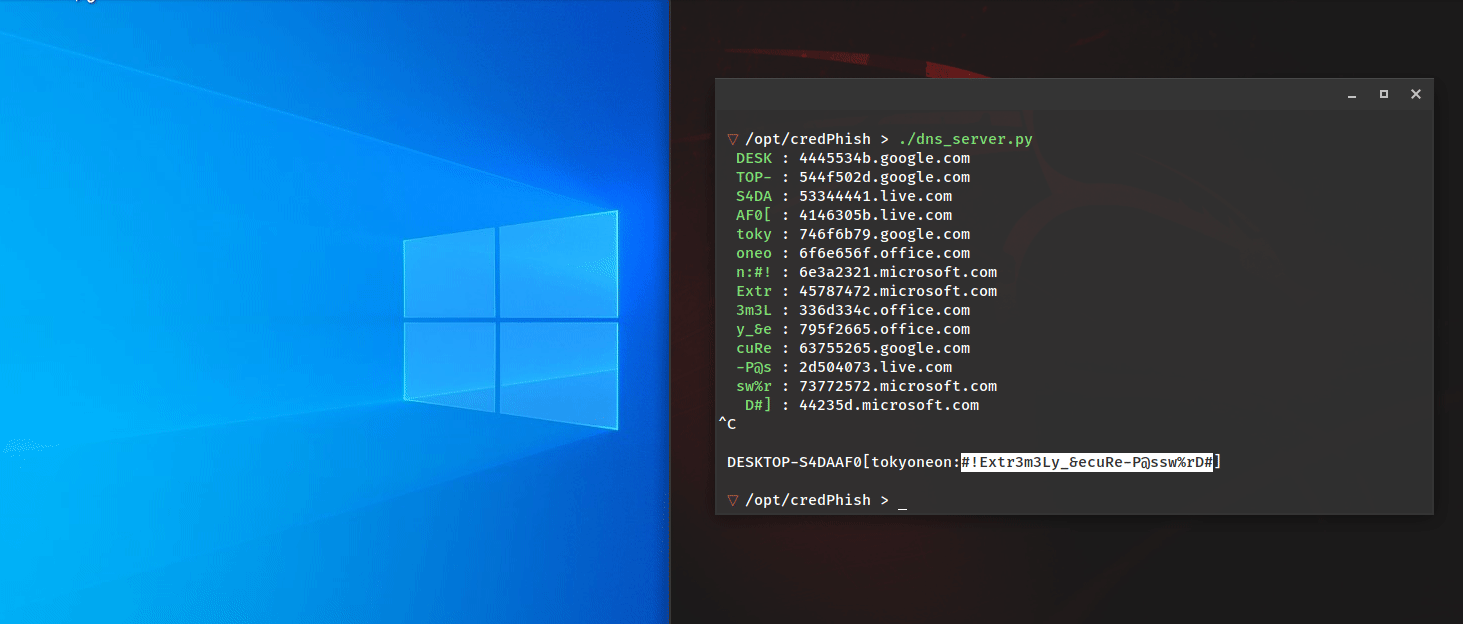
Kent Ickler // Background Over four years ago now, I wrote a blog post on fixing missing Content-Security-Policy by updating configuration on webservers: https://www.blackhillsinfosec.com/fix-missing-content-security-policy-website/. Content-Security-Policies instruct a user’s web browser […]
Podcast: Play in new window | Download
Subscribe: Apple Podcasts | Spotify | Amazon Music | RSS