Introducing Squeegee: The Microsoft Windows RDP Scraping Utility

Hi, it’s David with BHIS! You’ll be saying, “Wow,” every time you use this tool. It’s like a shammy. It’s like a towel. It’s like a sponge. A regular towel doesn’t work wet. This works wet or dry. This is for the house, the car, the boat, the RV. It’s Squeegee! Holds 12 times its weight in liquid. Look at this. It just does the work. Why would you want to work twice as hard? It doesn’t drip. It doesn’t make a mess.

Just kidding. Squeegee won’t clean up your messes, but hopefully, you will find it useful on your tests. Squeegee is actually a tool to scrape text from RDP screen captures.

You are probably asking yourself why that might be useful. We are constantly thinking about ways to get information using unconventional techniques. Imagine that you are on an internal penetration test and you want to know what the local administrator account username is on hosts, but you have hundreds or thousands of RDP listeners on the network. How might you approach that problem?
Next, consider a situation where you might want to get active session information from the environment in an effort to move laterally and escalate privileges. Bloodhound session data isn’t as reliable as it used to be, and, in modern Windows environments, session enumeration tends to get caught. What about cataloging users with active RDP sessions?
Squeegee can help in both of these situations. The first step is to collect RDP screen captures using a tool like NCC Group’s scrying. Once you have the RDP screen captures, you can process the entire group of results using Squeegee by just pointing the tool at the correct folder.
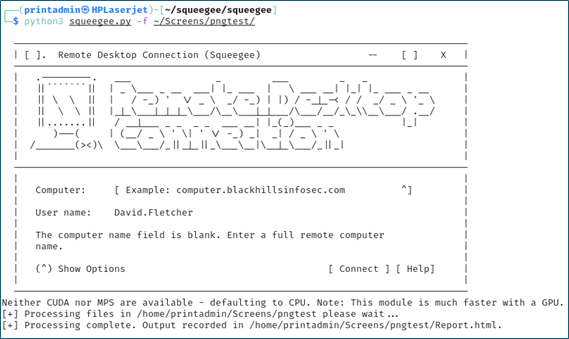
Squeegee will filter string content that is not likely to be useful in the context of username harvesting and system analysis. In addition, the tool will interpret various strings commonly observed in RDP image output to identify the operating system, the domain the computer is joined to, and whether the system is missing patches. Reporting options include console output, logfile output, and an HTML report.
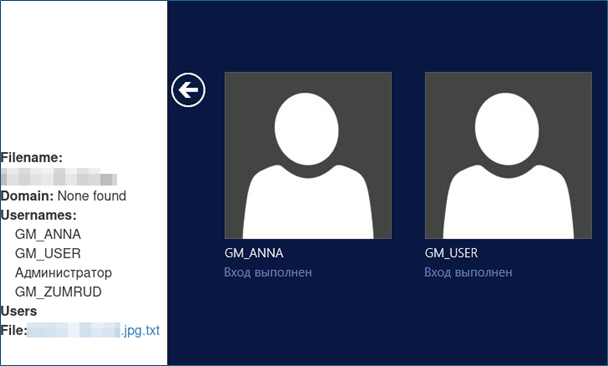
The HTML report organizes results by operating system and includes links to download the full list of unique usernames and usernames associated with a given RDP instance.
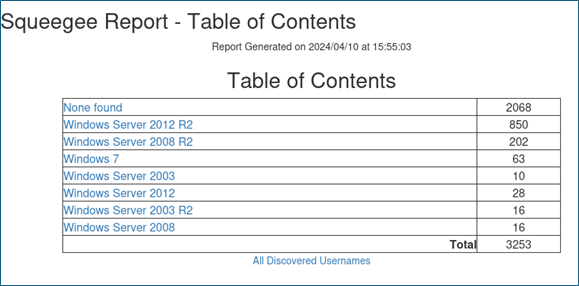
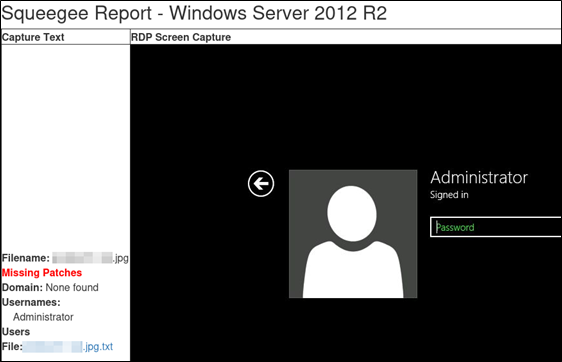
Squeegee uses the easyocr library for OCR support. As a result, text can be extracted from images with support for 81 different languages. This provides an easy method to process an image like the one shown below.
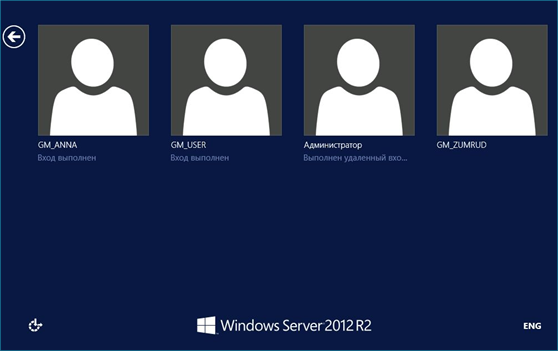
Without OCR support, reproducing strings presented on the screen may take considerable effort. Passing in the ISO language code to the script will cause easyocr to process strings associated with the target language. Once the images have been processed, usernames can be copied and pasted from the report or downloaded in the accompanying text file.
Check out the Squeegee repository at https://github.com/OOAFA/squeegee.
Ready to learn more?
Level up your skills with affordable classes from Antisyphon!
Available live/virtual and on-demand

