Your Infosec Supply List
Bre Schumacher // As I was walking through the back to school display at the store the other day, I picked up a handy-dandy school supply list. Of course there were […]

Bre Schumacher // As I was walking through the back to school display at the store the other day, I picked up a handy-dandy school supply list. Of course there were […]

Kent Ickler // It seemed like we were always cross-referencing the Hashcat Wiki or help file when working with Hashcat. We needed things like specific flags, hash examples, or command […]

Lee Kagan* // Expanding upon the previous post in this series, I decided to rewrite C2K (find it here) to change its behavior and options for the user. In this […]

Jordan Drysdale // tl;dr uBlock Origin appears, based on non-scientific testing, to be fairly effective at keeping trackers from making outbound HTTP GET requests. Tested Extensions: No Add-ons v Ghostery […]

Jordan Drysdale // A few of us have discussed the stress that small and medium business proprietors and operators feel these days. We want to help stress you out even […]

John Strand// In this webcast John talks about the new ACDC law and what it means exactly. There has been quite a bit of anger and great GIFs about hacking […]
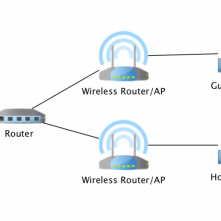
Ethan Robish // In this series of posts, I’ll discuss how I segmented my home network using VLANs and how I moved away from using a risky consumer-grade router at […]

Jordan Drysdale // The following content is loosely based on a presentation I gave at BSides Denver. After speaking at BSides Denver, one of the audience members spent some time […]

David Fletcher// My wife and I recently purchased a 2016 Ford Flex to replace an aging version of the same make and model that met an untimely fate. During the […]